comptia A+
-

Understanding cable types and their respective connectors is essential in modern IT environments, where the efficiency of data transmission depends on the correct physical medium. Common cable types include twisted pair (Ethernet), fiber optic, coaxial, HDMI, and USB, each serving unique roles in networking and communication systems. Ethernet cables, such as Cat5e, Cat6, and Cat6a,…
-

Setting up a Small Office/Home Office (SOHO) network requires a balance of reliability, security, and scalability. Wired networks offer stability and speed, typically using Ethernet cables (Cat5e, Cat6, or Cat6a) connected to a router or switch. The installation process involves configuring the router’s LAN settings, assigning static or dynamic IP addresses through DHCP, and ensuring…
-
Networked hosts provide essential services that enable communication, resource sharing, and security within a network. One of the most fundamental services is web hosting, where web servers deliver websites using HTTP and HTTPS protocols, ensuring content is accessible globally. File hosting and sharing services, such as FTP (File Transfer Protocol), SMB (Server Message Block), and…
-
Network configuration involves assigning and managing how devices connect and communicate across a network. IP addressing is a fundamental concept—devices can be assigned static IP addresses (manually set and unchanging) or dynamic IP addresses (automatically assigned by a DHCP server). Static IPs are often used for devices like servers or printers to ensure consistent accessibility,…
-

RISC, or Reduced Instruction Set Computer, represents a CPU architecture designed with simplified instructions, enabling processors to execute instructions at high speeds with fewer cycles per operation. According to IBM, RISC architectures streamline instruction processing by reducing complexity, enabling faster and more efficient performance at lower power consumption. ARM processors are built on RISC principles,…
-

Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two core transport-layer protocols that facilitate network communication, each serving distinct purposes. TCP is connection-oriented, meaning it establishes a reliable session between devices before data is transmitted. It uses a three-way handshake (SYN, SYN-ACK, ACK) to ensure that both sender and receiver are ready to…
-
Understanding how to use networking tools in real-world scenarios is a core part of CompTIA A+ training. Each tool has a specific purpose, from diagnosing connection issues to testing cables or analyzing network traffic. Below is a breakdown of essential tools and how they would be used when given a practical situation: Cable Tester A…
-

Ensuring seamless network connectivity on mobile devices requires proper configuration of Wi-Fi, cellular data, and Bluetooth settings. Wi-Fi connections should be set up using the appropriate security protocols, such as WPA2 or WPA3, to prevent unauthorized access. When configuring cellular data, users must input the correct Access Point Name (APN) settings, which define how the…
-

Effective troubleshooting is essential for maintaining system reliability and performance. The CompTIA A+ certification outlines a structured approach to problem-solving, ensuring that IT professionals can systematically identify and resolve issues. 1. Identify the Problem The initial step involves gathering comprehensive information about the issue. Technicians should consult system logs, engage with end-users to understand the…
-

Installing and configuring laptop hardware involves replacing or upgrading essential components such as memory (RAM), storage drives, and batteries. When upgrading RAM, the laptop must be powered off, and the correct type and size of memory modules must be installed in the designated slots. Storage upgrades often involve swapping out traditional hard disk drives (HDDs)…
-
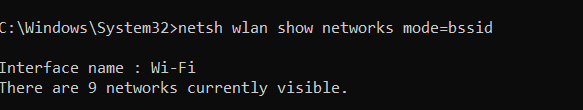
The command netsh wlan show networks mode=bssid is a Windows command-line instruction used to display detailed information about wireless networks available within range of the computer’s Wi-Fi router or adapter. The netsh utility, short for Network Shell, allows users to configure and monitor network settings from the command prompt. In this case, the command queries…
-
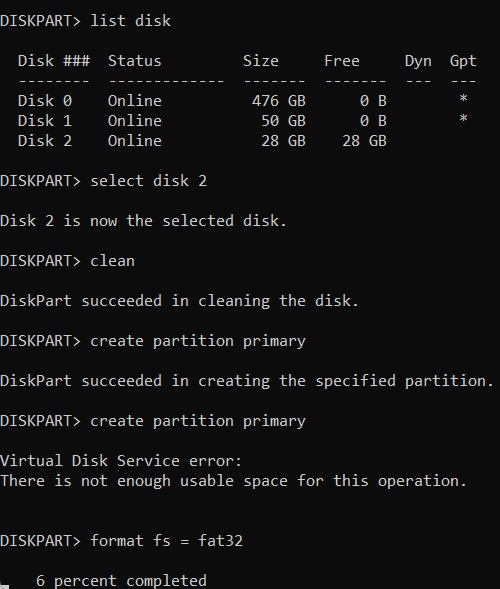
DiskPart is a command-line disk partitioning tool built into the Windows operating system. It allows users to manage their storage devices such as hard drives, SSDs, USB flash drives, and SD cards. DiskPart provides more control and flexibility over disk management compared to the GUI Disk Management utility in Windows. BitcoinVersus.Tech Editor’s Note: We volunteer…
-

The tasklist command is a Windows utility that lists all currently running processes on the system, along with key details like Process IDs (PIDs), memory usage, and executable names. It is commonly used for monitoring and troubleshooting processes. For instance, it can be combined with filters to locate specific tasks, such as running tasklist |…
-
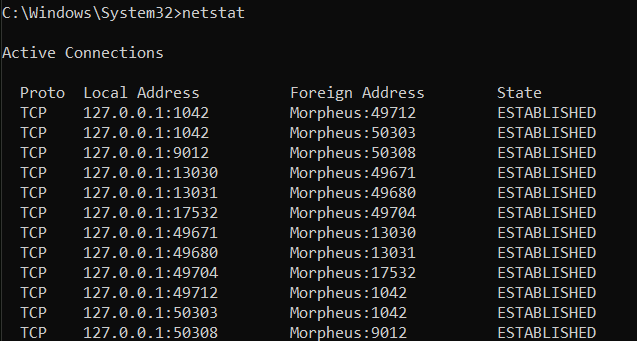
The netstat command provides statistics on current network connections and listening ports, offering insight into which applications are communicating over the network. Running netstat -a displays all active connections and ports. Netstat -b reveals the applications associated with each connection, valuable for security assessments (you need admin privileges for the “netstat -b” command). This command is used to detect suspicious…
-
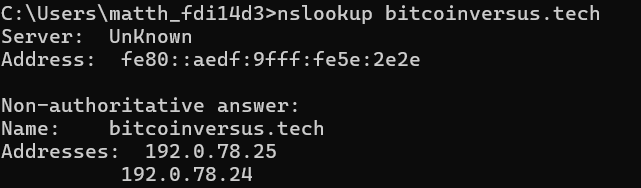
Nslookup (Name Server Lookup) is a command-line tool for querying Domain Name System (DNS) servers. It allows users to obtain the IP address associated with a domain name, or vice versa, helping in diagnosing DNS-related issues. For instance, nslookup google.com will show the IP addresses linked to bitcoinversus.tech This command is useful for troubleshooting DNS…
-
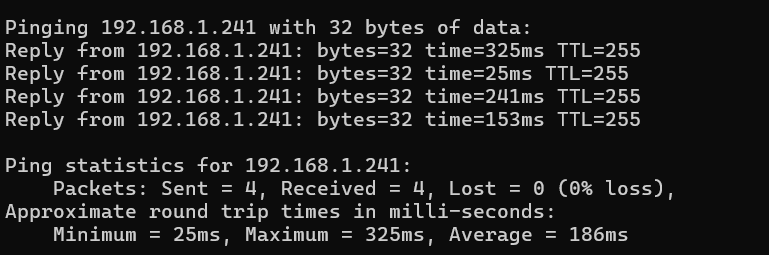
BitcoinVersus.Tech Editor’s Note: We volunteer daily to ensure the credibility of the information on this platform is Verifiably True.If you would like to support to help further secure the integrity of our research initiatives, please donate here The ping command is a fundamental network utility used to test the reachability of a host on an…
-

The ‘tracert’ command, short for ‘Trace Route,’ is a network diagnostic tool that tracks the path data packets take from your device to a specified IP address or domain. By listing each hop and measuring the time it takes to travel between them, ‘tracert’ helps identify delays or connection issues along the route. For instance,…
-

The ipconfig command in Windows OS provides essential network configuration details, helping users view IP addresses, subnet masks, and default gateways, vital for resolving connectivity issues. Running ipconfig /all offers extended data such as DNS servers, DHCP settings, and MAC addresses. This command is commonly used in troubleshooting scenarios where network connectivity is interrupted or…
-
The reason I had to change the color of the cursor was simply because I kept having a recurring issue with the cursor “disappearing” on different platforms. Changing your mouse color on Windows can improve cursor visibility, making it easier to locate on a complex screen and reducing eye strain. It also adds a personal…
-
-

Network topology is essential for network design and performance, as it determines data transfer efficiency, scalability, and maintenance costs. Physical and logical topologies play vital roles, with key types including star, bus, ring, mesh, tree, and hybrid topologies. Understanding these is crucial for effective network management and resilience.



