network +
-

LDAP (Lightweight Directory Access Protocol) is an open, vendor-neutral protocol used to access and maintain distributed directory information services over an Internet Protocol (IP) network. LDAP is widely used for storing and managing information about users, groups, computers, and other resources in a centralized database, known as a directory. The protocol allows clients to connect…
-

Fully Homomorphic Encryption (FHE) represents a significant advancement in cryptography, enabling computations on encrypted data without the need for decryption. This capability ensures that data remains confidential throughout processing, addressing longstanding security challenges in various sectors. Traditionally, data had to be decrypted before processing, exposing it to potential breaches. FHE allows analytical functions to operate…
-
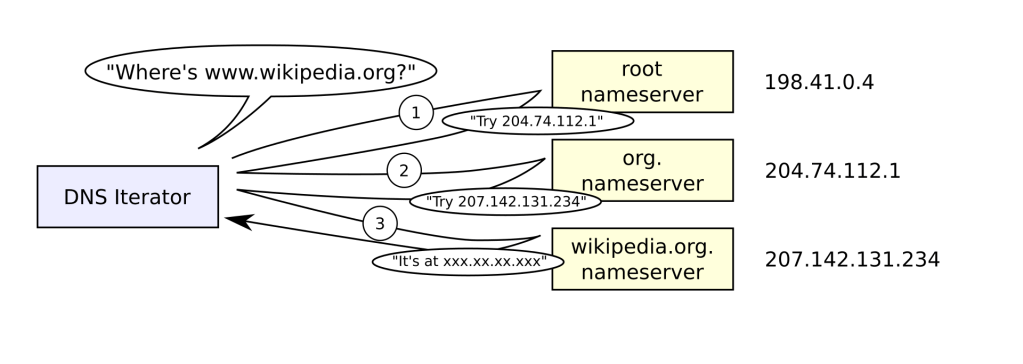
The Domain Name System (DNS) is like the phonebook of the internet. It translates human-friendly domain names such as www.google.com into IP addresses like 142.250.190.78, which computers use to locate and communicate with each other across networks. Without DNS, users would need to memorize long strings of numbers to access websites, making the internet much…
-

Setting up a Small Office/Home Office (SOHO) network requires a balance of reliability, security, and scalability. Wired networks offer stability and speed, typically using Ethernet cables (Cat5e, Cat6, or Cat6a) connected to a router or switch. The installation process involves configuring the router’s LAN settings, assigning static or dynamic IP addresses through DHCP, and ensuring…
-
Networked hosts provide essential services that enable communication, resource sharing, and security within a network. One of the most fundamental services is web hosting, where web servers deliver websites using HTTP and HTTPS protocols, ensuring content is accessible globally. File hosting and sharing services, such as FTP (File Transfer Protocol), SMB (Server Message Block), and…
-
Network configuration involves assigning and managing how devices connect and communicate across a network. IP addressing is a fundamental concept—devices can be assigned static IP addresses (manually set and unchanging) or dynamic IP addresses (automatically assigned by a DHCP server). Static IPs are often used for devices like servers or printers to ensure consistent accessibility,…
-

Setting up network connectivity on a mobile device involves configuring Wi-Fi, cellular data, Bluetooth, and VPN settings to ensure seamless access to the internet and other devices. Wi-Fi networks must be set up using the correct security protocols, such as WPA2 or WPA3, to prevent unauthorized access. Users should also verify SSID visibility and ensure…
-

Ensuring seamless network connectivity on mobile devices requires proper configuration of Wi-Fi, cellular data, and Bluetooth settings. Wi-Fi connections should be set up using the appropriate security protocols, such as WPA2 or WPA3, to prevent unauthorized access. When configuring cellular data, users must input the correct Access Point Name (APN) settings, which define how the…
-

Network Address Translation (NAT) is a networking technique that enables multiple devices on a local network to access external networks, such as the internet, using a single public IP address. This process involves modifying the IP address information in the packet headers as they pass through a router or firewall, effectively mapping private internal addresses…
-

Michael Saylor, Executive Chairman of Strategy, delivered a keynote address at the “Bitcoin for America” summit in Washington, D.C., organized by the Bitcoin Policy Institute. In his speech, Saylor emphasized Bitcoin’s potential to transform the U.S. economy and advocated for the nation to secure a substantial portion of the cryptocurrency. Bitcoin as a Strategic Asset…
-
Network ports serve as essential communication endpoints, allowing devices to exchange data over the internet and private networks. These numerical identifiers, assigned to specific services and applications, ensure proper data routing between devices. The IT industry relies on well-defined port numbers to facilitate secure and efficient networking operations across various protocols and services. Commonly Used…
-

Cryptocurrency mining relies on specific algorithms that ensure the security, decentralization, and integrity of blockchain networks. Each coin uses tailored algorithms like SHA-256, Scrypt, and Ethash, which have unique properties affecting mining efficiency, energy consumption, and security. Understanding these algorithms is essential for effective mining strategy and hardware selection.
-

Editor’s Note: Dr. Santostasi exact price predictions are more of a theory than a law. It’s a law in the sense that it does definitively explain where the price is going. But he’s theorizing on the exact price. Bitcoin’s adoption rate, per Giovanni Santostasi’s detailed analysis titled The Bitcoin Growth Game, is surpassing the early…
-

Solo.ckpool.org, a platform facilitating solo Bitcoin mining, has recently surpassed 9,000 users, marking its highest user count to date. This surge indicates a growing interest among individual miners in participating in the Bitcoin network. Despite the increase in users, the pool’s overall hashrate has declined to its lowest point in a considerable period. This trend…
-
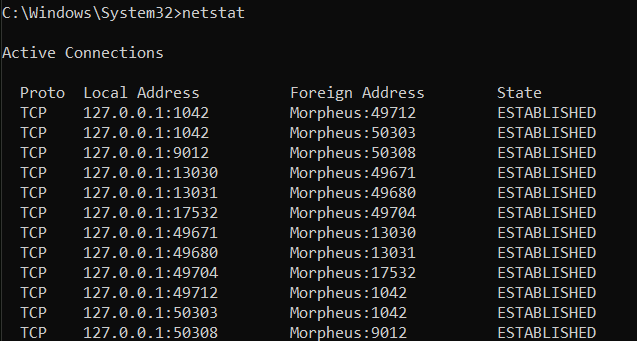
The netstat command provides statistics on current network connections and listening ports, offering insight into which applications are communicating over the network. Running netstat -a displays all active connections and ports. Netstat -b reveals the applications associated with each connection, valuable for security assessments (you need admin privileges for the “netstat -b” command). This command is used to detect suspicious…
-
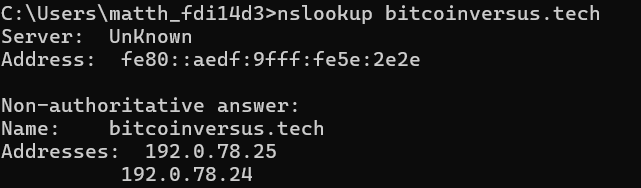
Nslookup (Name Server Lookup) is a command-line tool for querying Domain Name System (DNS) servers. It allows users to obtain the IP address associated with a domain name, or vice versa, helping in diagnosing DNS-related issues. For instance, nslookup google.com will show the IP addresses linked to bitcoinversus.tech This command is useful for troubleshooting DNS…
-
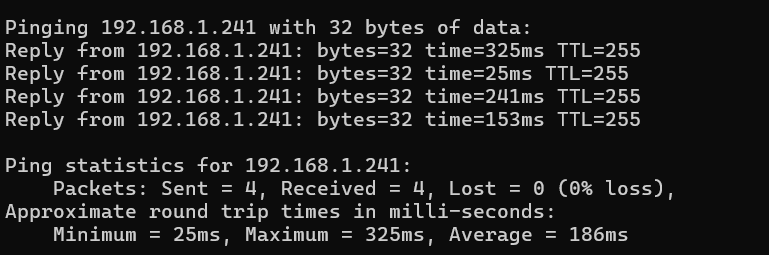
BitcoinVersus.Tech Editor’s Note: We volunteer daily to ensure the credibility of the information on this platform is Verifiably True.If you would like to support to help further secure the integrity of our research initiatives, please donate here The ping command is a fundamental network utility used to test the reachability of a host on an…
-
-
Lightning Labs has launched Taproot Assets, a protocol enabling the issuance and management of real-world assets on Bitcoin and Lightning Network. This advancement leverages Bitcoin’s liquidity, security, and Lightning’s low fees to support diverse asset issuance. Developers benefit from improved APIs and security measures, positioning Bitcoin as a central player in global finance.
-

Network topology is essential for network design and performance, as it determines data transfer efficiency, scalability, and maintenance costs. Physical and logical topologies play vital roles, with key types including star, bus, ring, mesh, tree, and hybrid topologies. Understanding these is crucial for effective network management and resilience.
-
-

The Bitcoin ecosystem has seen the Lightning Network grow exponentially, with River Financial being a significant advocate since 2019. The network has witnessed a 1,212% increase in routed transactions since 2021 and successfully routed $78.2m using 5,000 BTC in August 2023. Its increasing adoption by exchanges, forthcoming upgrades, and interest from non-Bitcoin businesses indicate a…
-