Trending News
-

Linux systems commonly rely on iptables and its modern replacement nftables as core utilities for firewall configuration. These tools allow administrators to create and manage firewall rules that filter traffic based on IP addresses, ports, protocols, and connection states. Linux firewalls operate at a very low level, offering fine-grained control of packet filtering and network…
-

Cloud computing is the delivery of computing services—including servers, storage, databases, networking, software, analytics, and more—over the internet rather than through local infrastructure. It offers organizations flexibility, scalability, and reduced upfront costs by eliminating the need for physical hardware. The most common cloud computing types are public cloud, private cloud, hybrid cloud, and community cloud.…
-

OpenAI is facing substantial financial hurdles, with projected losses accumulating to $44 billion by 2028. Despite generating significant revenue, largely from its generative AI models such as ChatGPT, the company anticipates it will not turn a profit until 2029. The high costs associated with AI training and the necessary infrastructure are key factors driving these…
-

Client-side virtualization is the practice of running virtual machines (VMs) directly on a user’s local device, such as a desktop or laptop, instead of relying on remote servers. This is made possible through the use of hypervisor software, such as Type 2 hypervisors (hosted), which run on top of a host operating system. Common examples…
-

As of July 2024, the United States’ national debt surpassed $35 trillion, marking a dramatic increase from $17 trillion just a decade ago. This surge, driven by both structural fiscal policies and pandemic-related expenditures, presents significant concerns for the future of the U.S. economy. Economists warn of potential long-term consequences, such as rising interest costs…
-

Self-Monitoring, Analysis, and Reporting Technology (SMART) is a monitoring system embedded in computer hard disk drives (HDDs) and solid-state drives (SSDs). Its primary function is to detect and report various indicators of drive reliability, aiming to anticipate potential hardware failures. When SMART data suggests an imminent drive failure, software on the host system can…
-

The Federal Deposit Insurance Corporation (FDIC) has announced that banks no longer need prior approval to engage in cryptocurrency-related activities, provided they adequately manage associated risks. This policy shift rescinds the previous guidance from April 2022, which required FDIC-supervised institutions to obtain approval before engaging in crypto-related activities. Acting FDIC Chairman Travis Hill stated that…
-
In the context of embedded systems and hardware-level communication, UART, or Universal Asynchronous Receiver-Transmitter, is a fundamental protocol for serial data transfer. It allows devices to communicate by transmitting data one bit at a time in a sequential fashion. Unlike synchronous protocols, UART does not rely on a shared clock signal but instead uses a…
-

A recent survey by financial giant Charles Schwab has revealed that 45% of ETF investors plan to allocate funds to Bitcoin and crypto-related exchange-traded funds (ETFs) in 2024. This marks a significant uptick in interest compared to last year, when only 38% of investors expressed similar intentions. Schwab’s findings come at a time when the…
-

The New York Yankees have ignited discussions across Major League Baseball (MLB) with their adoption of the innovative “torpedo” bats, contributing to a record-tying 15 home runs in their first three games of the season. Designed by former Yankees analyst and MIT physicist Aaron Leanhardt, the torpedo bats feature a unique shape with the…
-

In a recent statement, the U.S. Securities and Exchange Commission (SEC) clarified that Proof-of-Work (PoW) cryptocurrency mining activities, such as those involving Bitcoin, do not fall under federal securities laws. The SEC’s Division of Corporation Finance noted that both solo and pooled mining operations do not meet the criteria of a securities transaction under the…
-

In a landmark decision, the United Arab Emirates (UAE) has officially exempted all cryptocurrency transactions from value-added tax (VAT), a move set to take effect on November 15, 2024. This exemption applies retroactively to transactions dating back to January 1, 2018, ensuring that individuals and businesses alike will no longer face the 5% VAT levy…
-

IPv6 is the latest version of the Internet Protocol, designed to replace IPv4 due to the exhaustion of available IPv4 addresses. IPv6 provides a vastly larger address space by using 128-bit addresses instead of the 32-bit format used by IPv4. This means IPv6 can support approximately 340 undecillion (3.4 x 10³⁸) unique addresses, which is…
-

The motherboard is the central backbone of any computer system, acting as the main printed circuit board (PCB) that connects and allows communication between all essential components. It houses the CPU socket, RAM slots, chipset, power connectors, and expansion slots such as PCIe, enabling the installation of graphics cards, network cards, or storage controllers. Motherboards…
-

The Ten Commandments hold an unparalleled position in the religious, historical, and legal frameworks of society. These stone tablets, traditionally believed to have been handed down to Moses by God, serve as a foundational artifact for the three major Abrahamic faiths: Judaism, Christianity, and Islam. Their influence on the development of law and moral principles…
-
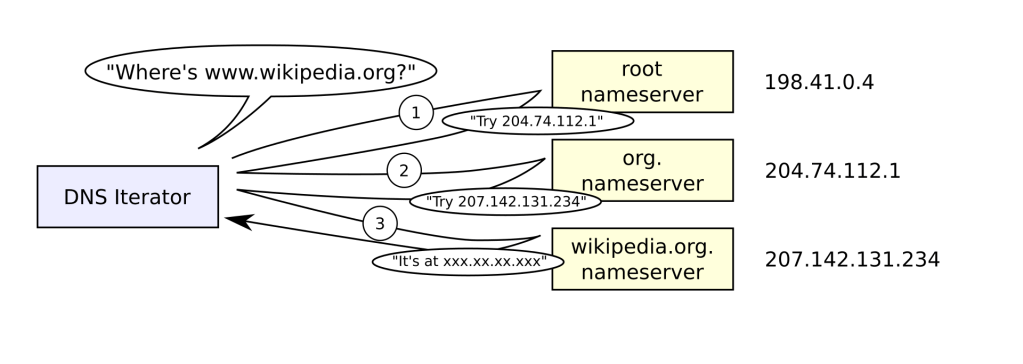
The Domain Name System (DNS) is like the phonebook of the internet. It translates human-friendly domain names such as www.google.com into IP addresses like 142.250.190.78, which computers use to locate and communicate with each other across networks. Without DNS, users would need to memorize long strings of numbers to access websites, making the internet much…
-
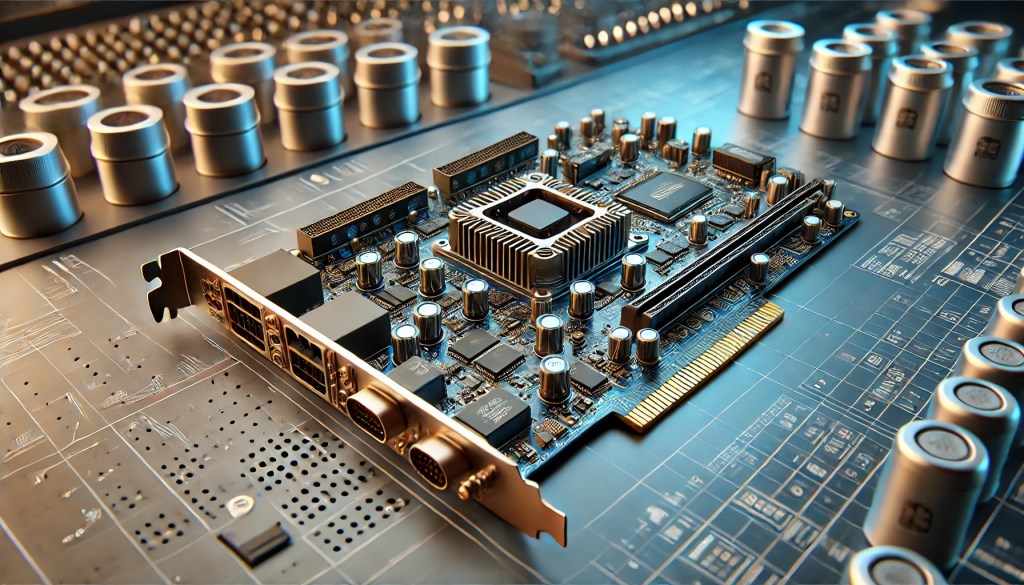
Add-on cards, also known as expansion cards, are hardware components inserted into expansion slots on a motherboard—typically PCIe slots—to extend a server’s functionality. These cards enable specialized performance beyond the system’s native capabilities, including enhanced network connectivity, accelerated processing, and advanced storage management. Common types include GPU cards for high-performance computing, network interface cards (NICs)…
-

Storage devices are critical components in computing, used to retain digital information permanently or temporarily. The two most common types of internal storage are Hard Disk Drives (HDDs) and Solid-State Drives (SSDs). HDDs use spinning magnetic platters and read/write heads to store data and are valued for their high storage capacities at lower cost per…
-

As humanity sets its sights on Mars, the theoretical valuation of Martian land has ignited intense discussions among space enthusiasts and economists alike. Speculative estimates for the value of an acre on Mars range from $400 million to over $1 billion. These figures are based on the immense costs associated with developing infrastructure on the…
-
Selecting and installing RAM (Random Access Memory) starts with identifying the system’s compatibility requirements. The first step is to determine the form factor—most desktop motherboards use DIMM (Dual Inline Memory Module), while laptops use the smaller SO-DIMM (Small Outline DIMM). Next, determine the DDR generation your system supports—DDR3, DDR4, or DDR5. These are not backward…
-

Mt. Gox has announced another delay in reimbursing its creditors. The repayment deadline has been extended by a full year, pushing the new date to October 31, 2025. This decision has caused frustration among creditors, many of whom have waited since 2014 to recover their funds. The delay reflects the complexity of the bankruptcy case,…
-

Understanding cable types and their respective connectors is essential in modern IT environments, where the efficiency of data transmission depends on the correct physical medium. Common cable types include twisted pair (Ethernet), fiber optic, coaxial, HDMI, and USB, each serving unique roles in networking and communication systems. Ethernet cables, such as Cat5e, Cat6, and Cat6a,…
-

Crypto.com, has relocated its North American headquarters from Miami to Tyler, Texas. The move places the company at the heart of Texas, a state known for its booming cryptocurrency infrastructure, particularly Bitcoin mining. This strategic relocation positions Crypto.com to take advantage of the state’s talent pool and favorable political climate. The new office, located in…
-
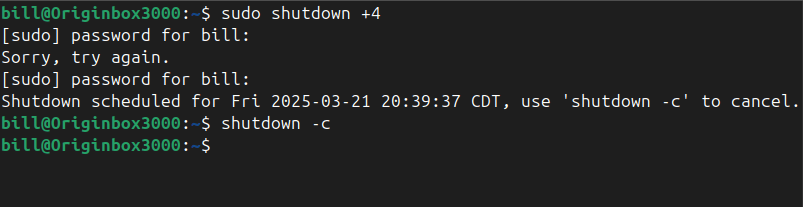
The shutdown command in Linux safely powers off or reboots a system, allowing users and administrators to schedule the shutdown after a certain time interval or at a specific time. It ensures the system terminates all processes correctly and prevents data corruption. The command accepts various parameters to specify time and behavior, with the option…
-

Setting up a Small Office/Home Office (SOHO) network requires a balance of reliability, security, and scalability. Wired networks offer stability and speed, typically using Ethernet cables (Cat5e, Cat6, or Cat6a) connected to a router or switch. The installation process involves configuring the router’s LAN settings, assigning static or dynamic IP addresses through DHCP, and ensuring…
-

Computer Engineering for Babies, authored by Chase Roberts, is a groundbreaking book designed to introduce young children, primarily toddlers, to the fundamentals of computer engineering. The book combines interactive elements with simple explanations to help kids grasp the basics of logic gates—such as AND, OR, and NOT gates—through a visually appealing, hands-on experience. At its…
-

The Avalon Nano 3S, developed by Canaan, is a compact Bitcoin miner designed for home use, combining cryptocurrency mining with heating functionality. It offers a hashrate of 6 terahashes per second (TH/s) while consuming a maximum of 140 watts of power. The device operates on an input voltage of 28 volts and supports frequencies of…
-
Networked hosts provide essential services that enable communication, resource sharing, and security within a network. One of the most fundamental services is web hosting, where web servers deliver websites using HTTP and HTTPS protocols, ensuring content is accessible globally. File hosting and sharing services, such as FTP (File Transfer Protocol), SMB (Server Message Block), and…
-
Network configuration involves assigning and managing how devices connect and communicate across a network. IP addressing is a fundamental concept—devices can be assigned static IP addresses (manually set and unchanging) or dynamic IP addresses (automatically assigned by a DHCP server). Static IPs are often used for devices like servers or printers to ensure consistent accessibility,…
-

A woman on x.com recently shared a life-changing experience where her Apple Watch played a pivotal role in saving her life. After receiving two low heart rate notifications, she decided to check her blood pressure, which led her to discover dangerously high levels of 237/99. She was quickly admitted to the hospital and diagnosed with…
-

RISC, or Reduced Instruction Set Computer, represents a CPU architecture designed with simplified instructions, enabling processors to execute instructions at high speeds with fewer cycles per operation. According to IBM, RISC architectures streamline instruction processing by reducing complexity, enabling faster and more efficient performance at lower power consumption. ARM processors are built on RISC principles,…
-
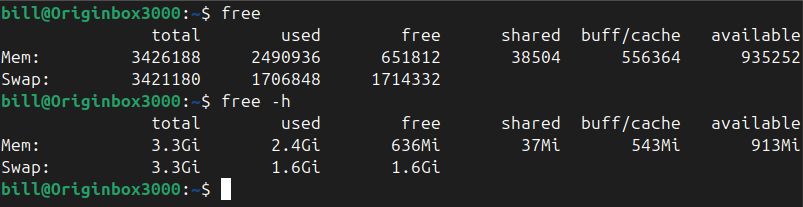
The free command in Linux is used to display comprehensive memory usage information, reporting the total, used, free, shared, buffer/cache, and available memory, including both RAM and swap space. It provides essential insights for system administrators and users to efficiently monitor and manage resources. By default, running the command free outputs memory details numerically in…
-

Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two core transport-layer protocols that facilitate network communication, each serving distinct purposes. TCP is connection-oriented, meaning it establishes a reliable session between devices before data is transmitted. It uses a three-way handshake (SYN, SYN-ACK, ACK) to ensure that both sender and receiver are ready to…
-

CleanSpark, Inc. (Nasdaq: CLSK), a prominent Bitcoin mining company, is set to join the S&P SmallCap 600 index before the market opens on March 24, 2025. This inclusion signifies a notable milestone for CleanSpark, reflecting its consistent performance and growth within the cryptocurrency mining sector. The S&P SmallCap 600 index measures the small-cap segment of…
-

Corporate universities are leading the charge in reshaping education as tech giants like Nvidia, Google, Amazon, and Walmart increasingly offer tailored learning platforms. By creating practical, career-oriented educational programs, these companies provide a direct route into the workforce. Their initiatives focus on equipping students with in-demand skills, often at a fraction of the cost of…
-

Setting up network connectivity on a mobile device involves configuring Wi-Fi, cellular data, Bluetooth, and VPN settings to ensure seamless access to the internet and other devices. Wi-Fi networks must be set up using the correct security protocols, such as WPA2 or WPA3, to prevent unauthorized access. Users should also verify SSID visibility and ensure…
-
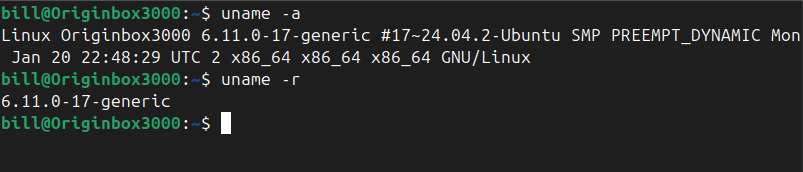
The uname command in Linux prints system information about the current machine. Specifically, it reports details such as the kernel name, kernel release, kernel version, machine hardware name, and the operating system. This command is commonly used by administrators and users alike to quickly determine system details for troubleshooting, software compatibility checks, or documenting system…
-

Apple is gradually moving away from its long-standing tradition of annual product releases, signaling a major change in its approach to innovation and consumer expectations. Historically, the company adhered to a predictable schedule, launching updated iPhones, iPads, and Macs each year. This strategy benefited investors and aligned product releases with key sales periods, such as…
-

“Rite Where U Stand,” a standout track from Gang Starr’s 2003 album “The Ownerz,” exemplifies the duo’s signature fusion of sharp lyricism and DJ Premier’s masterful production. The song features a notable collaboration with Jadakiss, adding a distinctive edge to the composition. DJ Premier’s production on “Rite Where U Stand” is a testament to his…
-
Understanding how to use networking tools in real-world scenarios is a core part of CompTIA A+ training. Each tool has a specific purpose, from diagnosing connection issues to testing cables or analyzing network traffic. Below is a breakdown of essential tools and how they would be used when given a practical situation: Cable Tester A…
-

Ensuring seamless network connectivity on mobile devices requires proper configuration of Wi-Fi, cellular data, and Bluetooth settings. Wi-Fi connections should be set up using the appropriate security protocols, such as WPA2 or WPA3, to prevent unauthorized access. When configuring cellular data, users must input the correct Access Point Name (APN) settings, which define how the…
-

The growing influence of artificial intelligence in education has sparked intense debate among educators. Amy Clukey, a former university professor, voiced her frustration on social media, saying, “I’m no longer a teacher. I’m just a human plagiarism detector.” Clukey highlights how her time once spent offering constructive feedback to students has now shifted primarily to…
-

Effective troubleshooting is essential for maintaining system reliability and performance. The CompTIA A+ certification outlines a structured approach to problem-solving, ensuring that IT professionals can systematically identify and resolve issues. 1. Identify the Problem The initial step involves gathering comprehensive information about the issue. Technicians should consult system logs, engage with end-users to understand the…
-

Mobile devices rely on a variety of accessories and ports to enhance functionality and improve user experience. Properly setting up and configuring these peripherals ensures seamless connectivity and optimized performance. Common accessories include external keyboards, wireless headphones, docking stations, and styluses, each requiring correct pairing and settings adjustments. Bluetooth-enabled accessories must be paired through the…
-
Nano is a simple and user-friendly command-line text editor for Unix-based systems, including Linux. It is designed to be easy to use, even for beginners, with a straightforward interface and on-screen shortcuts. Unlike more complex editors like Vim or Emacs, Nano does not require users to learn advanced keybindings or modes, making it an accessible…
-

Applied Digital (NASDAQ: APLD) has raised $160 million in strategic financing, with backing from notable investors like NVIDIA and Related Companies. This significant capital infusion is set to propel Applied Digital’s data center expansion, focused on high-performance computing (HPC) and AI workloads. By leveraging NVIDIA’s GPU technologies, the company is positioning itself as a leader…
-
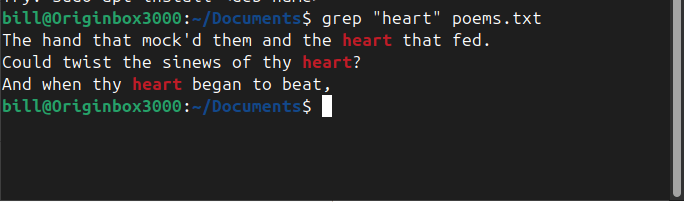
The grep command in Linux is a powerful text-search utility used to find specific patterns within files. In the screenshot, the command grep “heart” poems.txt was executed, instructing the system to search for the word “heart” inside poems.txt and display all matching lines. The output highlights instances where “heart” appears within the poem, helping the…
-

Links in Linux are essential for managing files efficiently, offering flexibility in how files are referenced and accessed. Two primary types exist: hard links and symbolic links (also called soft links). While both serve as references to files, they function differently in how they store and manage data. A hard link is a direct reference…
-

The Small Computer System Interface (SCSI), pronounced “scuzzy,” is a set of standards for connecting and transferring data between computers and peripheral devices. Introduced in the 1980s, SCSI became a prevalent interface for hard drives, scanners, printers, and other peripherals, especially in high-performance and server environments. Despite the advent of newer interfaces like USB and…
-
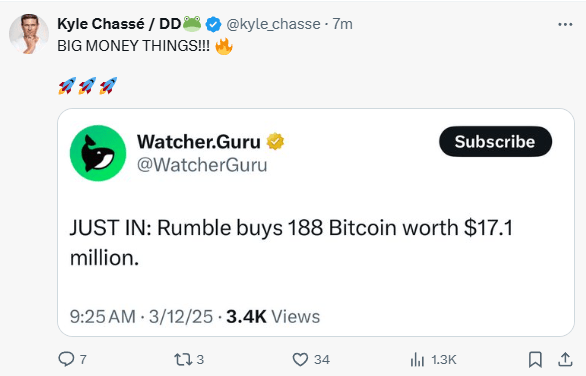
Rumble has made a significant investment by purchasing 188 Bitcoin, valued at approximately $17.1 million. This substantial acquisition underscores the company’s confidence in Bitcoin as a strategic asset and aligns with the recent trend of major corporations incorporating digital assets into their balance sheets. Investor and crypto advocate Kyle Chassé celebrated the news on social…
-

Installing and configuring laptop hardware involves replacing or upgrading essential components such as memory (RAM), storage drives, and batteries. When upgrading RAM, the laptop must be powered off, and the correct type and size of memory modules must be installed in the designated slots. Storage upgrades often involve swapping out traditional hard disk drives (HDDs)…
-

Oneil Cruz, the shortstop turned outfielder for the Pittsburgh Pirates, is set to make history in the 2025 MLB season with a potential 50-home run campaign. Known for his incredible power, Cruz has recorded some of the hardest-hit balls in Statcast history, including a 122.4 mph shot, the fastest ever tracked. His raw power has…
-
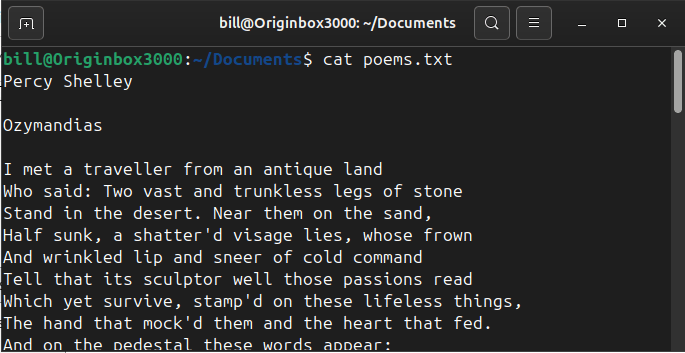
The cat command in Linux is used to display the contents of a file directly in the terminal. In the screenshot, the command cat poems.txt was executed from the ~/Documents directory. The cat command instructs the system to read the file poems.txt and print its contents line by line on the screen. The output shows…
-

El Salvador’s President, Nayib Bukele, has reaffirmed the nation’s commitment to Bitcoin by announcing the purchase of an additional 11 BTC, valued at over $1 million, for the country’s strategic reserves. This move comes despite the International Monetary Fund’s (IMF) recent $1.4 billion loan agreement, which includes stipulations aimed at limiting the country’s exposure to…
-
-

Bitfarms Ltd. (NASDAQ/TSX: BITF), a global Bitcoin mining and data center company, has completed its acquisition of Stronghold Digital Mining, Inc. (SDIG), significantly enhancing its U.S. operations. This acquisition increases Bitfarms’ energy portfolio to 623 megawatts under management, adding 165 MW of active generating capacity and 142 MW of available import capacity. It also secures…
-

The Proof-of-Power Wall concept from Jason P. Lowery’s SOFTWAR introduces a cybersecurity model where control signals must carry proof of computational work to be accepted. By rejecting signals that lack this proof, the system ensures that every authorized command comes with a cost, reducing the risk of exploitation. Adjusting the difficulty of the proof-of-power process…
-

Marathon Digital Holdings (MARA) has significantly expanded its operations by acquiring two operational data centers in Hannibal and Hopedale, Ohio, totaling 222 megawatts (MW) of interconnect-approved capacity. These sites currently operate at 122 MW, with approval to expand by an additional 100 MW. Additionally, MARA is developing a 150 MW facility in Findlay, Ohio, which…
-

Coinbase, the leading U.S. cryptocurrency exchange, plans to expand its workforce by approximately 1,000 employees in 2025. CEO Brian Armstrong attributes this expansion to the pro-crypto policies of President Donald Trump’s administration. Armstrong announced the hiring initiative following the White House Crypto Summit, emphasizing the administration’s supportive stance on digital assets. He noted that…
-

In a historic move, Goldman Sachs has acknowledged the growing significance of digital assets in its latest annual letter to shareholders. The 2024 report highlights how blockchain technology and cryptocurrencies are intensifying competition within the financial sector. The letter notes that the rise of electronic trading, alongside blockchain and artificial intelligence, has transformed market…
-
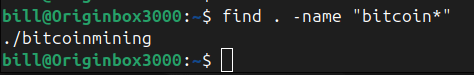
The find command in Linux is a powerful and versatile tool designed to search through files and directories based on specific criteria. It helps users efficiently locate files within a file system, filtering searches by name, file type, modification date, size, or even permissions. A typical syntax for using find includes specifying a starting directory,…
-

Strategy, formerly known as MicroStrategy, has expanded its Bitcoin holdings by acquiring an additional 130 BTC. This purchase, valued at approximately $10.7 million, was executed at an average price of $82,981 per BTC between March 10 and March 16, 2025. According to the company’s latest SEC filing, the acquisition was funded through the sale…
-

Colorado is poised to officially designate nuclear energy as a clean energy source, following the recent passage of House Bill 25-1040 by the state Senate. The bill, which updates statutory definitions of “clean energy” and “clean energy resource” to include nuclear energy, now awaits Governor Jared Polis’s signature. The legislation’s approval marks a significant…
-

Data centers, the backbone of our digital world, employ various cooling methods to maintain optimal operating temperatures for their equipment. One such method is immersion cooling, where IT components are submerged in thermally conductive, dielectric liquids. technique allows for efficient heat dissipation, as the liquid directly contacts heat-generating components, reducing the need for traditional air…
-

Molex connectors are standardized electrical connectors widely used in power and signal applications across various industries, including computing, consumer electronics, and automotive systems. They are known for their durability, ease of use, and reliable connectivity, often featuring plastic housings with metal contacts that enable secure electrical connections. These connectors originated from Molex Incorporated, a company…
-

Changpeng “CZ” Zhao, the founder of Binance, has been released from U.S. custody after completing a four-month prison sentence. Zhao was detained for failing to implement adequate Anti-Money Laundering (AML) controls at Binance, which allowed illegal transactions involving cybercriminals and terrorist groups. Zhao’s case was a result of Binance’s significant legal struggles in the U.S.…
-

Fred Thiel, CEO of Marathon Digital Holdings (MARA), recently acknowledged the Trump administration’s efforts in promoting cryptocurrency adoption. In an interview with Fox Business, Thiel highlighted how current policies have positioned the United States to become a dominant force in Bitcoin mining and blockchain technology. According to Thiel, Bitcoin miners possess the unique advantage of…
-

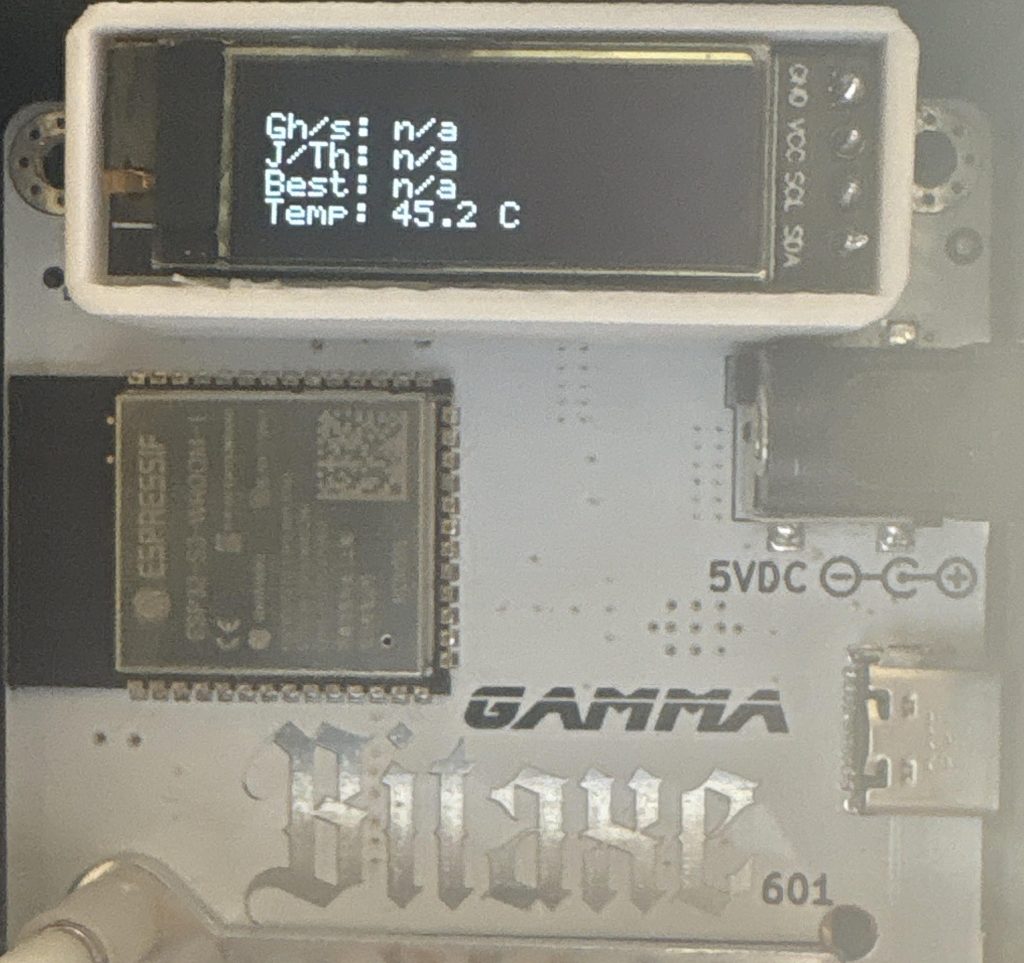
When your Bitaxe Gamma 601 periodically overheats, you’ll notice an indicator in your firmware UI and a “device overheat” message displayed on the miner’s LED screen. Don’t worry; Resolving it is straightforward. First, open your firmware “settings.” Make sure to reset the frequency and core voltage to the default values recommended for your ASIC chip.…
-

The apropos command searches manual page names and descriptions for a given keyword, helping users quickly discover relevant commands for a task. The apropos command helps Linux users find commands related to a keyword quickly. For example, typing apropos copy lists commands involving copying files or directories. Similarly, apropos network shows commands associated with network…
-

A new HBO documentary titled “Money Electric: The Bitcoin Mystery” has sent ripples through the cryptocurrency world, claiming to uncover the true identity of Satoshi Nakamoto, the elusive creator of Bitcoin. The film, directed by Emmy-nominated filmmaker Cullen Hoback, promises to reveal evidence pointing to a long-time Bitcoin developer, Peter Todd, as Nakamoto. However, Todd…
-
File System Hierarchy Standard (FHS): The File System Hierarchy Standard defines a consistent directory structure for Linux systems, specifying locations for system files, user files, and application data. FHS ensures predictability and uniformity across distributions, facilitating easier management and maintenance. Standard directories include /etc for configuration files, /var for variable data, /bin for essential binaries,…
-

Charles Schwab has announced its willingness to offer cryptocurrency trading services if U.S. regulatory laws evolve to allow it. This potential move could significantly impact the cryptocurrency market, injecting billions in investments and making crypto trading accessible to a vast number of traditional investors. CEO Walt Bettinger confirmed that Schwab is ready to act swiftly,…
-
“Nas Is Like,” the lead single from Nas’s third studio album, “I Am…,” released in 1999, stands as a testament to the rapper’s lyrical prowess and the seamless synergy between Nas and producer DJ Premier. The track is renowned for its intricate wordplay and introspective themes, reflecting Nas’s reflections on his identity and experiences.…
-
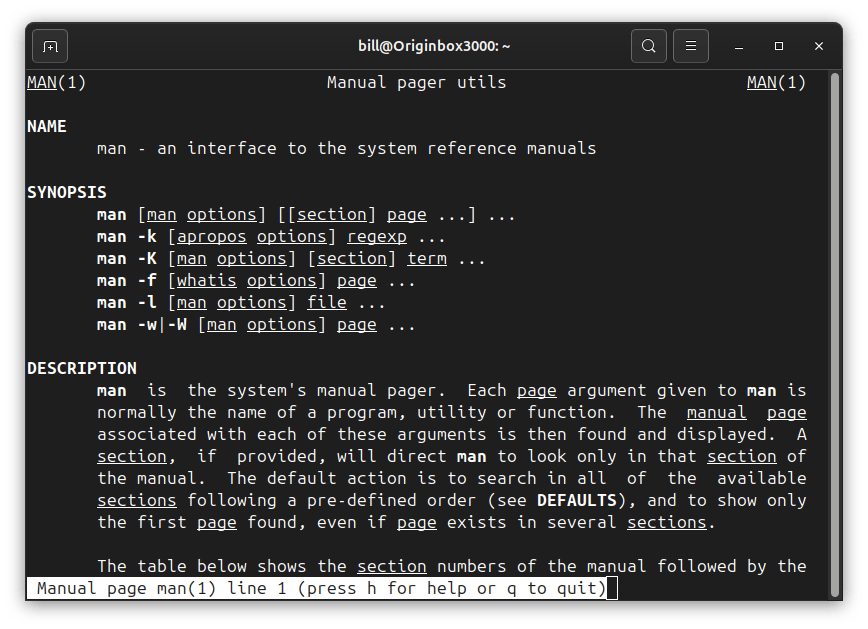
The man command, short for ‘manual’, is an essential tool in Linux, offering detailed documentation on virtually every command and program. By typing man followed by a specific command name, users gain immediate access to comprehensive manuals covering syntax, usage options, and practical examples. Ideal for beginners and seasoned professionals alike, the man command fosters…
-
-

Struggling to get your resume noticed on LinkedIn? Searching for a job can be overwhelming and at times feels like a job itself. During this time of applying to hundreds of jobs, I’ve found that filtering certain job preferences can dramatically increase your resume visibility. Try this 3-step strategy to boost your visibility instantly: 2.…
-
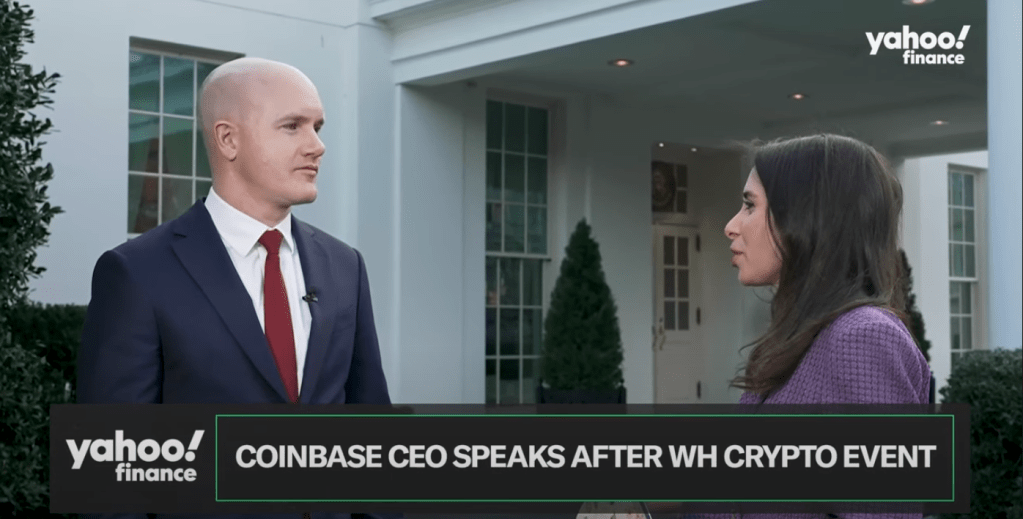
Coinbase CEO Brian Armstrong attended the first-ever White House crypto summit and praised President Donald Trump’s efforts to revitalize the industry. In an interview with Yahoo Finance Senior Reporter Jennifer Schonberger, Armstrong stated, “President Trump really breathed life back into this industry over the last few years. We really felt like we were being unlawfully…
-

Network Address Translation (NAT) is a networking technique that enables multiple devices on a local network to access external networks, such as the internet, using a single public IP address. This process involves modifying the IP address information in the packet headers as they pass through a router or firewall, effectively mapping private internal addresses…
-
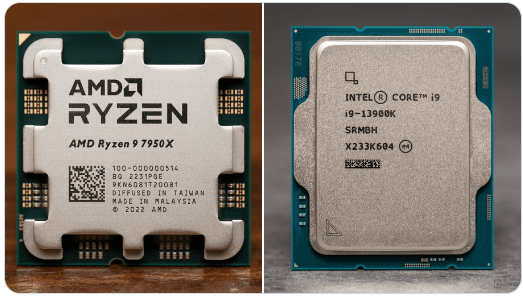
Intel and AMD, the two titans of the CPU industry, have recently unveiled their flagship processors: Intel’s Core i9-13900K and AMD’s Ryzen 9 7950X. The Core i9-13900K boasts 24 cores and 32 threads, operating at a base frequency of 3.0 GHz, with turbo frequencies reaching up to 5.8 GHz. In contrast, the Ryzen 9 7950X…
-
Bitdeer Technologies Group has completed a successful test of its SEAL02 Bitcoin mining chip, achieving an impressive power efficiency ratio of 13.5 J/TH. This milestone represents a significant advancement in energy efficiency within the mining industry, placing Bitdeer at the forefront of innovative mining solutions. SEAL02 was developed in partnership with TSMC, one of the…
-

Definition and FunctionalitySerial communication refers to the process of transmitting data one bit at a time over a communication channel or computer bus. Unlike parallel communication, which sends multiple bits simultaneously, serial communication reduces signal interference and supports long-distance data transfer with fewer wires. It is widely used in telecommunications, industrial automation, and computer networking…
-

President Donald Trump has imposed a 25% tariff on all steel and aluminum imports to the United States, effective immediately, aiming to bolster domestic manufacturing. The European Union swiftly retaliated with countermeasures targeting $28 billion worth of U.S. goods, including iconic products such as bourbon whiskey, jeans, and Harley-Davidson motorcycles. Canada, the largest supplier…
-

The ATX 24-pin main power connector (Also known as the P1 connector) provides essential electricity to the motherboard, supplying multiple voltages including 3.3V, 5V, and 12V. It is the primary source of power ensuring all motherboard components function correctly and maintain stable performance. The EPS (Extended Power Supply) connector is an 8-pin power connector delivering…
-

The release of the NFL 2K25 mod in October 2024 has once again highlighted the dominance of the NFL 2K5 legacy. With updated rosters, 4K textures, and modern gameplay mechanics, the mod breathes new life into the classic football game, making it an instant hit with fans who have long craved competition in the football…
-

Michael Saylor, Executive Chairman of Strategy, delivered a keynote address at the “Bitcoin for America” summit in Washington, D.C., organized by the Bitcoin Policy Institute. In his speech, Saylor emphasized Bitcoin’s potential to transform the U.S. economy and advocated for the nation to secure a substantial portion of the cryptocurrency. Bitcoin as a Strategic Asset…
-

Bitdeer Technologies Group (NASDAQ: BTDR) has announced the successful testing of its latest Bitcoin mining chip, SealMiner A3, achieving an exceptional power efficiency of 9.7 joules per terahash (J/TH) in low voltage, ultra power-saving mode. This advancement aligns with the company’s SEALMINER technology roadmap and reflects its commitment to enhancing mining efficiency. Developed in collaboration…
-
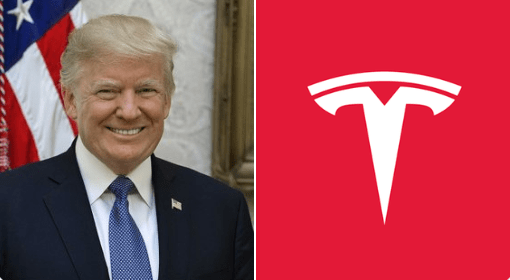
President Donald Trump showcased several Tesla models at the White House on Tuesday afternoon, expressing his intention to purchase a Tesla vehicle. This event occurred amid a significant decline in Tesla’s stock value, which has fallen by 50% since December 2024. Standing alongside Tesla CEO Elon Musk, President Trump inspected various Tesla models, including…
-
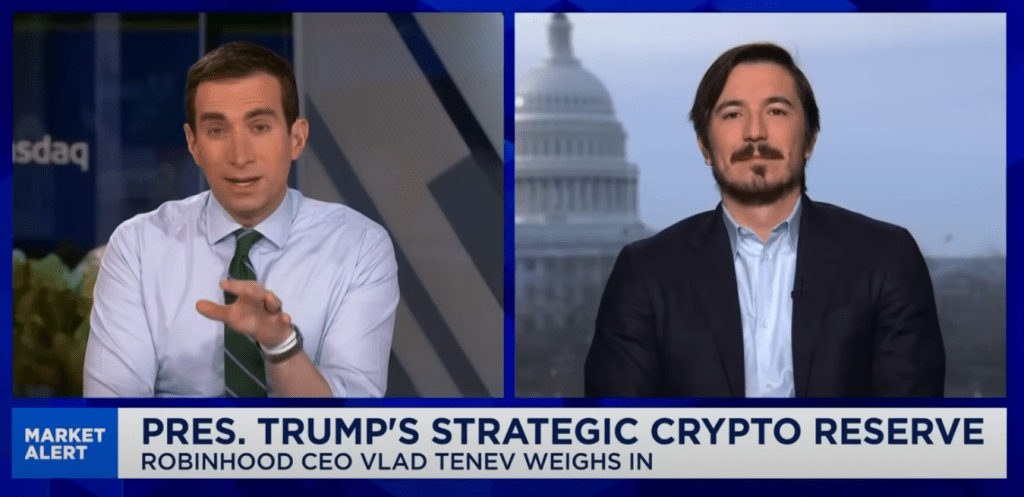
Robinhood co-founder and CEO Vlad Tenev joined CNBC’s Squawk Box to discuss the U.S. administration’s establishment of a strategic Bitcoin reserve, calling it a “sensible approach” to integrating digital assets into the national financial system. His remarks followed the White House Crypto Summit, where industry leaders and policymakers convened to discuss the role of Bitcoin…
-

The Trump administration formally launched the U.S. Crypto Strategic Reserve, a government-backed initiative designed to integrate digital assets into national financial infrastructure. The reserve was announced as part of the White House Digital Assets Policy Framework, marking a historic shift in how the federal government engages with cryptocurrency. The initiative aims to establish Bitcoin and…
-

Ontario’s Premier, Doug Ford, announced a 25% increase in electricity export charges to the United States, effective Monday, affecting approximately 1.5 million American homes and businesses. This move is a direct response to President Donald Trump’s recent trade measures against Canada. The surcharge targets electricity exports to states including Minnesota, New York, and Michigan. Ford…
-
-

NRG Bloom, a Canadian company co-founded and led by CEO Makir Volcy, is pioneering sustainable Bitcoin mining solutions in Africa. The company repurposes flared gas and stranded energy to power its mining operations, addressing environmental concerns while fostering technological advancement. Headquartered in Quebec, NRG Bloom has established a Bitcoin mining operation in Nigeria, utilizing…
-

The Power-On Self-Test (POST) is a fundamental diagnostic process performed by computers immediately after they are powered on. This procedure verifies the functionality and integrity of essential hardware components before the operating system loads, ensuring that the system operates correctly. During POST, the system’s firmware—commonly the BIOS or UEFI—conducts a series of checks on…
-

At the 2024 Digital Assets Conference in São Paulo, BlackRock once again positioned itself at the forefront of the cryptocurrency market, expanding its reach by discussing the impact of Bitcoin and launching its Bitcoin ETF in Brazil. Jay Jacobs, head of Thematics and Active Equity ETFs at BlackRock, highlighted how Bitcoin is evolving as a…
-

Overclocking involves increasing a computer component’s clock rate beyond the manufacturer’s specifications to boost performance. This practice is commonly applied to processors and graphics cards, allowing them to execute more operations per second. While overclocking can lead to significant performance gains, it also raises power consumption and heat output, necessitating improved cooling solutions to maintain…