Tech Docs
-

RAID (Redundant Array of Independent Disks) is a data storage technology that combines multiple physical drives into a single logical unit to enhance performance, reliability, or both. Various RAID levels offer different balances between these factors. RAID 0 utilizes data striping, distributing data across multiple disks without redundancy. This configuration enhances read and write speeds…
-

Python’s package management landscape has been significantly shaped by pip, the default package installer for the language. Introduced in 2008 by developer Ian Bicking, pip—an acronym for “Pip Installs Packages”—was created to enhance the process of installing and managing Python software packages. It serves as a direct interface to the Python Package Index (PyPI), a…
-

M.2 is a compact, high-speed interface standard designed for internal expansion cards and solid-state drives (SSDs) in modern computers, including laptops, desktops, and embedded systems. It serves as a replacement for older standards like mSATA and mini PCIe, offering improved performance, efficiency, and space savings. M.2 devices utilize multiple bus interfaces, including PCI Express (PCIe)…
-

Accessing the web interface of the Cisco Catalyst 1200-8T switch is a straightforward process that allows IT professionals to configure and monitor network settings efficiently. The switch’s web-based graphical user interface (GUI) provides an intuitive platform for managing various network functions. Prerequisites: Accessing the Web Interface: Post-Login Configuration: For a visual walkthrough of the initial…
-
According to IEEE, the Transmission Control Protocol (TCP) has remained a cornerstone of modern internet infrastructure for over five decades. One of its fundamental processes, the FIN handshake, ensures a controlled termination of a network session, preventing data corruption or sudden disconnections. Unlike an abrupt RST (Reset) termination, the FIN handshake involves a four-step process…
-
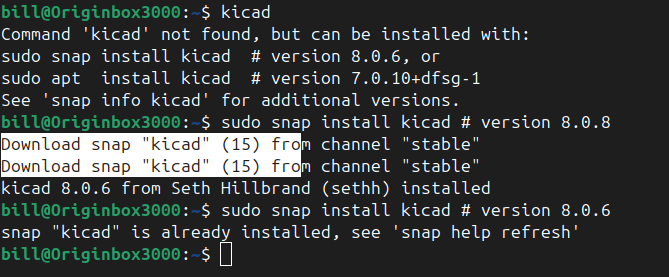
KiCad is a powerful open-source software suite used for designing printed circuit boards (PCBs). It offers a comprehensive set of tools for schematic capture, PCB layout, and 3D visualization, making it a go-to choice for both hobbyists and professional engineers. The software supports industry-standard formats and integrates essential features such as Gerber file export and…
-
-
UPDATE: the file names in this documentation have been changed. The server-side application is now referred to as VirtualServer.py, while the client-side script is called ProofOfScript.py. These names have been chosen to help readers easily follow along with the instructions. When running the API, please ensure you use the file names as indicated. In order…
-
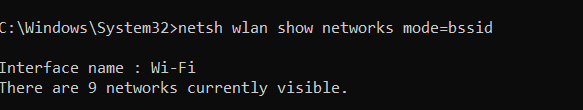
The command netsh wlan show networks mode=bssid is a Windows command-line instruction used to display detailed information about wireless networks available within range of the computer’s Wi-Fi router or adapter. The netsh utility, short for Network Shell, allows users to configure and monitor network settings from the command prompt. In this case, the command queries…
-

BIOS, or Basic Input/Output System, is integral to a computer’s startup process. Stored on the motherboard, it initializes and tests hardware components, ensuring proper functionality before loading the operating system. One of the primary functions of BIOS is the Power-On Self-Test (POST), which verifies the presence and correct operation of essential hardware like the processor,…
-

Troubleshooting a bricked NerdAxe device can be challenging, especially when a firmware update is interrupted, potentially leading to hardware issues. The NerdAxe, an open-source Bitcoin ASIC miner, utilizes the ESP32-S3 chip as its controller. Firmware updates for the NerdAxe are typically performed remotely via online platforms like Bitronics’ DIY Flasher. Interruptions during this process can…
-

An Uninterruptible Power Supply (UPS) is a device that provides emergency backup power to a computer or network system during a power outage or voltage fluctuation. It acts as a buffer between the computer and the power source, ensuring that critical systems remain operational long enough to safely shut down or switch to an alternative…
-

In the realm of computer systems, memory plays a pivotal role in determining performance and data retention capabilities. Two primary categories of memory exist: volatile and non-volatile. Volatile memory, such as Random Access Memory (RAM), requires a continuous power supply to maintain stored data. When the system powers down, information in volatile memory is lost.…
-
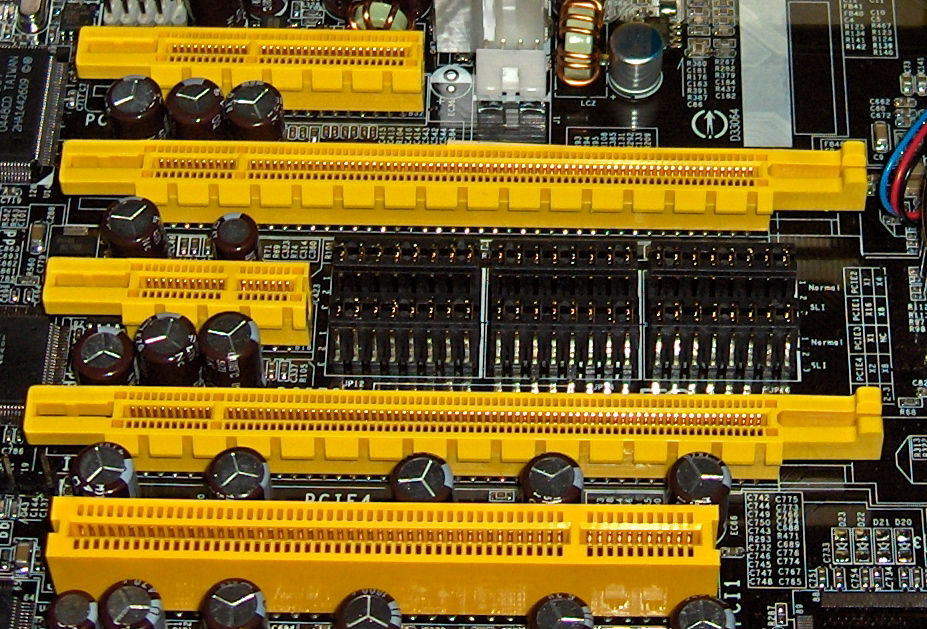
The Peripheral Component Interconnect Express (PCIe) is a high-speed expansion bus interface used to connect various hardware components to a computer’s motherboard. It serves as the primary interface for graphics cards, network adapters, storage devices, and other peripherals that require fast data transfer. PCIe uses a serial communication architecture, meaning it transmits data one bit…
-

The snmpwalk command is used to perform a series of network management requests to a specific device using an IP address(example: 10.31.10.101),starting from the OID 1.3.6.1.2.1.2.2.1, using SNMPv3. Reference record for OID: Website to interpret OID Adresses snmpwalk -v3 -l authPriv -u l1monitor -a MD5 -A GEe9bb8h -x DES -X 4ixay7su 10.36.10.108 1.3.6.1.2.1.2.2.1snmpwalk: This is…
-
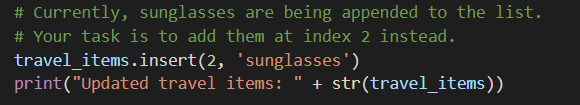
The code snippet provided shows how to insert an item into a list at a specific position rather than appending it at the end. Instead of adding “sunglasses” to the end of the list using append(), the task is to insert “sunglasses” at index 2 of the list travel_items. Explanation of the code:travel_items.insert(2, ‘sunglasses’) This…
-

The tasklist command is a Windows utility that lists all currently running processes on the system, along with key details like Process IDs (PIDs), memory usage, and executable names. It is commonly used for monitoring and troubleshooting processes. For instance, it can be combined with filters to locate specific tasks, such as running tasklist |…
-
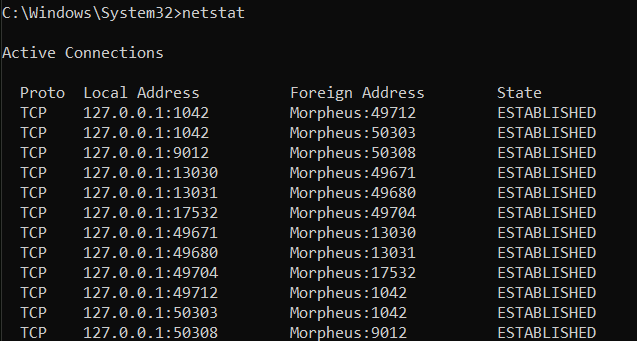
The netstat command provides statistics on current network connections and listening ports, offering insight into which applications are communicating over the network. Running netstat -a displays all active connections and ports. Netstat -b reveals the applications associated with each connection, valuable for security assessments (you need admin privileges for the “netstat -b” command). This command is used to detect suspicious…
-
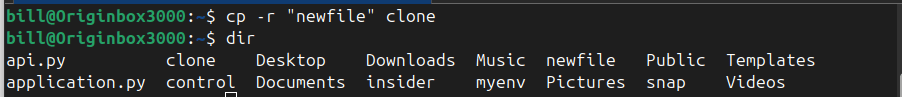
The cp command in Linux is used to copy files and directories. It’s a powerful utility that can create copies of data from one location to another, either within the same directory or across different directories. Adding the -r (recursive) flag allows you to copy entire directories, including their contents. This command copies the newfile…
-
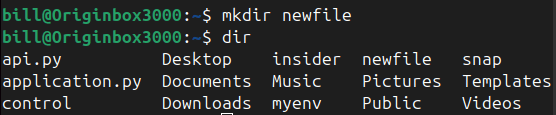
The mkdir command, an abbreviation for “make directory,” is a foundational tool for Linux users, enabling the creation of directories directly within the terminal. According to Linux documentation, the command is widely used to organize files systematically, promoting efficient file management practices for both personal and professional projects. Users simply type mkdir <directory_name> to create…
-
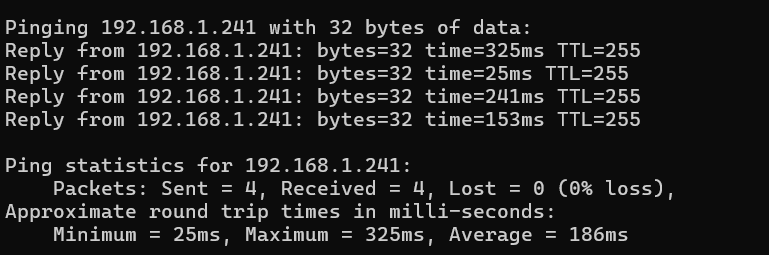
BitcoinVersus.Tech Editor’s Note: We volunteer daily to ensure the credibility of the information on this platform is Verifiably True.If you would like to support to help further secure the integrity of our research initiatives, please donate here The ping command is a fundamental network utility used to test the reachability of a host on an…
-
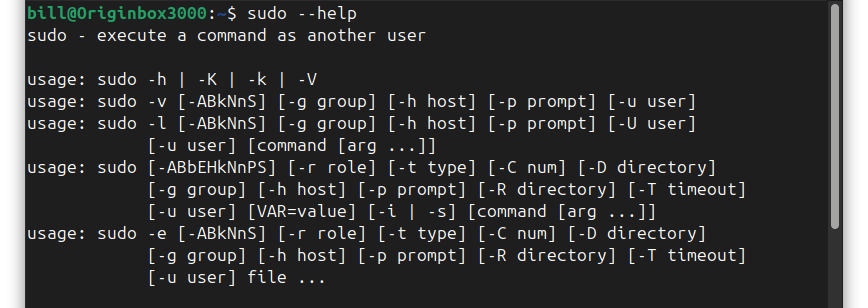
The sudo command in Linux enables authorized users to execute commands with superuser privileges, facilitating essential administrative tasks such as software installation, system configuration modifications, and service management. Key benefits of using sudo include enhanced security by requiring explicit permission before executing potentially harmful commands, accountability through logging each use for traceability, and controlled access…
-

The ‘tracert’ command, short for ‘Trace Route,’ is a network diagnostic tool that tracks the path data packets take from your device to a specified IP address or domain. By listing each hop and measuring the time it takes to travel between them, ‘tracert’ helps identify delays or connection issues along the route. For instance,…
-

In the realm of telecommunications, multi-band devices, such as dual-band, tri-band, quad-band, and penta-band, are engineered to operate across multiple radio frequency bands. This capability enhances connectivity and performance by allowing devices to communicate over various frequencies. Dual-Band Routers: An Overview Dual-band routers function on two distinct frequency bands: 2.4 GHz and 5 GHz. The…
-

The ipconfig command in Windows OS provides essential network configuration details, helping users view IP addresses, subnet masks, and default gateways, vital for resolving connectivity issues. Running ipconfig /all offers extended data such as DNS servers, DHCP settings, and MAC addresses. This command is commonly used in troubleshooting scenarios where network connectivity is interrupted or…
-
The reason I had to change the color of the cursor was simply because I kept having a recurring issue with the cursor “disappearing” on different platforms. Changing your mouse color on Windows can improve cursor visibility, making it easier to locate on a complex screen and reducing eye strain. It also adds a personal…
-

Printers are an essential part of many computing environments, and understanding how they work, as well as their maintenance and troubleshooting, is vital for the CompTIA A+ certification. There are several types of printers commonly found in workplaces and homes, each with unique characteristics. Laser printers, for instance, use a process involving a laser beam…
-

To remotely monitor and control individual sockets on a Power Distribution Unit (PDU) using Modbus communication, Modbus-TCP can be employed to access and modify specific registers over a network. Each socket (or outlet) on the PDU is associated with unique register addresses that allow users to read the status (on/off) or control the power state.…
-

American Wire Gauge (AWG) is a logarithmic stepped standardized wire gauge system used since 1857, predominantly in North America, for the diameters of round, solid, nonferrous, electrically conducting wire. Dimensions of the wires are given in ASTM standard B 258. The cross-sectional area of each gauge is an important factor for determining its current-carrying capacity.…
-
-
Modbus RTU (Remote Terminal Unit) is a widely used serial communication protocol developed by Schneider Electric in 1979 for industrial applications. It’s designed for communication between various devices such as programmable logic controllers (PLCs), sensors, and other industrial electronic devices. Modbus RTU uses a Commander/Executor architecture, where one device (Commander) initiates communication and controls one…
-
-
-
-

The power supply unit (PSU) is a fundamental component of the Bitcoin ASIC machine. The K9 PSU (pictured below) is a specific PSU for the K9 model ASIC machine. Generally, there are specific model PSU’s that are compatible with specific Bitcoin Mining Machines. 1. Materials needed:A. Drill (w/phillips head) B. Phillips head screwdriver. *Note –…
-
-
-
-

I recently completed the “Python Tutorial” by Red Tea Infusion. This course is a comprehensive introduction to Python, covering everything from basic syntax to essential data structures. Designed for beginners, it requires no prior programming experience, making it an excellent starting point for anyone new to coding. Course Content and Structure The course is divided…
-
You can download applications directly from the web using PowerShell on Windows. This guide explains how to use Invoke-WebRequest to download software, using Visual Studio Code as an example. Steps include opening PowerShell, defining the source URL, specifying the destination path, and executing the download command.
-

Network topology is essential for network design and performance, as it determines data transfer efficiency, scalability, and maintenance costs. Physical and logical topologies play vital roles, with key types including star, bus, ring, mesh, tree, and hybrid topologies. Understanding these is crucial for effective network management and resilience.
-

To the aspiring bitcoiner, Here’s some advice on how to get a job in the bitcoin sector: 1. Understand your purpose. The truth is that some people don’t understand the importance of the first and only digital monetary network in which you can exchange value on a global scale instantaneously without the need for permission…