Tech Docs
-

Trusted Platform Module (TPM) is a dedicated chip embedded on a computer’s motherboard, designed to secure hardware through integrated cryptographic keys. It stores sensitive information such as encryption keys, digital certificates, and passwords in a tamper-resistant environment. TPM is commonly used for: The current standard is TPM 2.0, which is required by modern operating systems…
-
The /bin directory is where Linux keeps many of its most essential commands that are available to all users, whether they are administrators or regular users. Inside /bin, you will find programs like ls for listing directory contents, cp for copying files, and mv for moving or renaming files. These commands are so vital that…
-

The Linux root directory (/) is the highest-level directory in the entire file system, acting as the central point from which everything else originates. To further clarify, the root directory (/) is the top-level of the entire Linux file system hierarchy, whereas /root is specifically the private home directory for the root (administrator) user. All…
-

What Is an SSD? A Solid-State Drive (SSD) uses flash memory chips to store data. There are no moving parts, making it faster, quieter, and more durable than traditional hard drives. SSDs have extremely fast read/write speeds, especially in NVMe (PCIe) form, which are ideal for boot drives, gaming systems, and business apps. SSDs come…
-

A thermal printer uses heat to transfer images onto paper. It comes in two types: Consumables and Maintenance Direct thermal printers require only thermal paper, while thermal transfer printers need both ribbon and label stock.Maintenance includes: Technicians must also check for signs of printhead wear, incorrect temperatures, or paper with poor heat response when troubleshooting…
-

Two of the most recognized and widely used printer languages in the industry are PCL (Printer Command Language) and PostScript. Each one comes with unique advantages and is suited for different types of environments and workloads. PCL, developed by Hewlett-Packard, is a standard language found in many office printers. It’s built for speed and efficiency—great…
-

Every desktop computer relies on a Power Supply Unit (PSU) to convert wall electricity into usable voltage levels that safely power internal components. The PSU takes in AC (Alternating Current) and outputs DC (Direct Current) in multiple voltages—typically +12V, +5V, and +3.3V—distributed to the motherboard, CPU, storage devices, and GPU. Without proper power regulation, even…
-

The snmpwalk command is used to perform a series of network management requests to a specific device using an IP address(example: 10.31.10.101),starting from the OID 1.3.6.1.2.1.2.2.1, using SNMPv3. Reference record for OID: Website to interpret OID Adresses snmpwalk -v3 -l authPriv -u l1monitor -a MD5 -A GEe9bb8h -x DES -X 4ixay7su 10.36.10.108 1.3.6.1.2.1.2.2.1snmpwalk: This is…
-
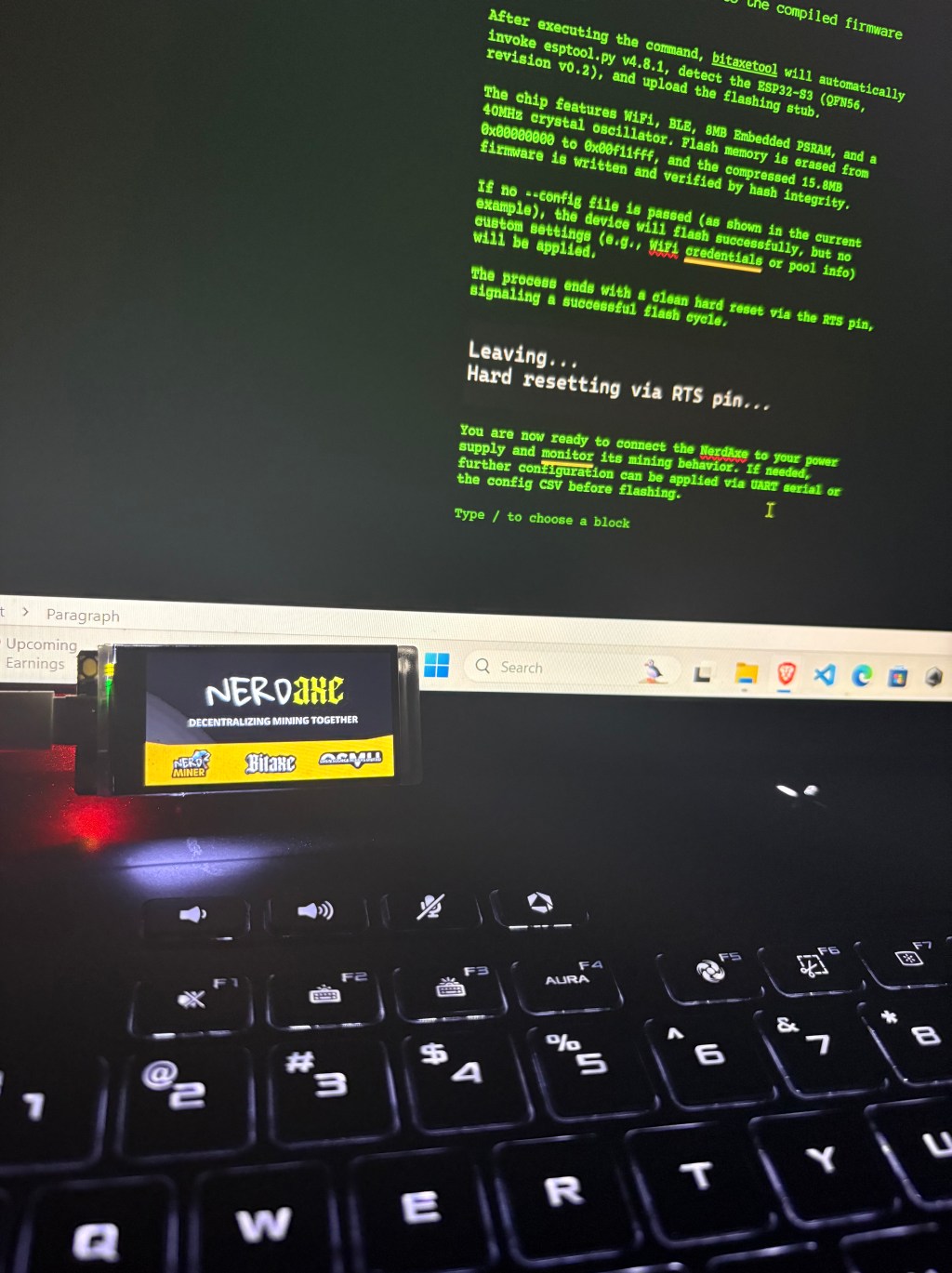
Esptool.py is a Python-based utility created by Espressif for flashing firmware onto ESP8266 and ESP32 chips. It operates cross-platform—working on Windows, Linux, and macOS—and is executed from the command line using Python. Although its name ends in .py, users interact with it using simple terminal commands, not actual Python code. The command-line arguments passed to…
-

ERCOT (The Electric Reliability Council of Texas) is the independent system operator that manages the flow of power for about 90 percent of Texas, serving more than 27 million customers and coordinating more than 54,100 miles of transmission and roughly 1,250 generation units; it oversees real time dispatch and market settlement for the state’s competitive…
-
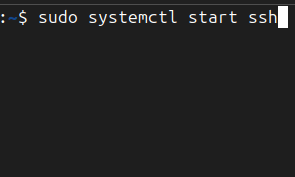
Secure Shell, commonly known as SSH, is a cryptographic network protocol used to establish secure and encrypted communication between two systems over an unsecured network. It allows users to remotely access and control another computer, typically through a command-line interface. SSH ensures that all data, including login credentials and command outputs, are encrypted to prevent…
-

Landauer’s Principle is a fundamental law of physics that establishes the minimum possible amount of energy required to irreversibly change or erase one bit of information in a computational process. This principle is rooted in the second law of thermodynamics, which states that any logically irreversible operation, such as resetting a bit from one state to…
-

The taskkill command is a powerful Windows OS CLI tool that allows users to forcefully terminate running processes directly from the terminal. Unlike the Task Manager’s graphical interface, taskkill gives users precise control over which processes to end, either by using the process name (also called the image name) or its unique process ID (PID).…
-
-
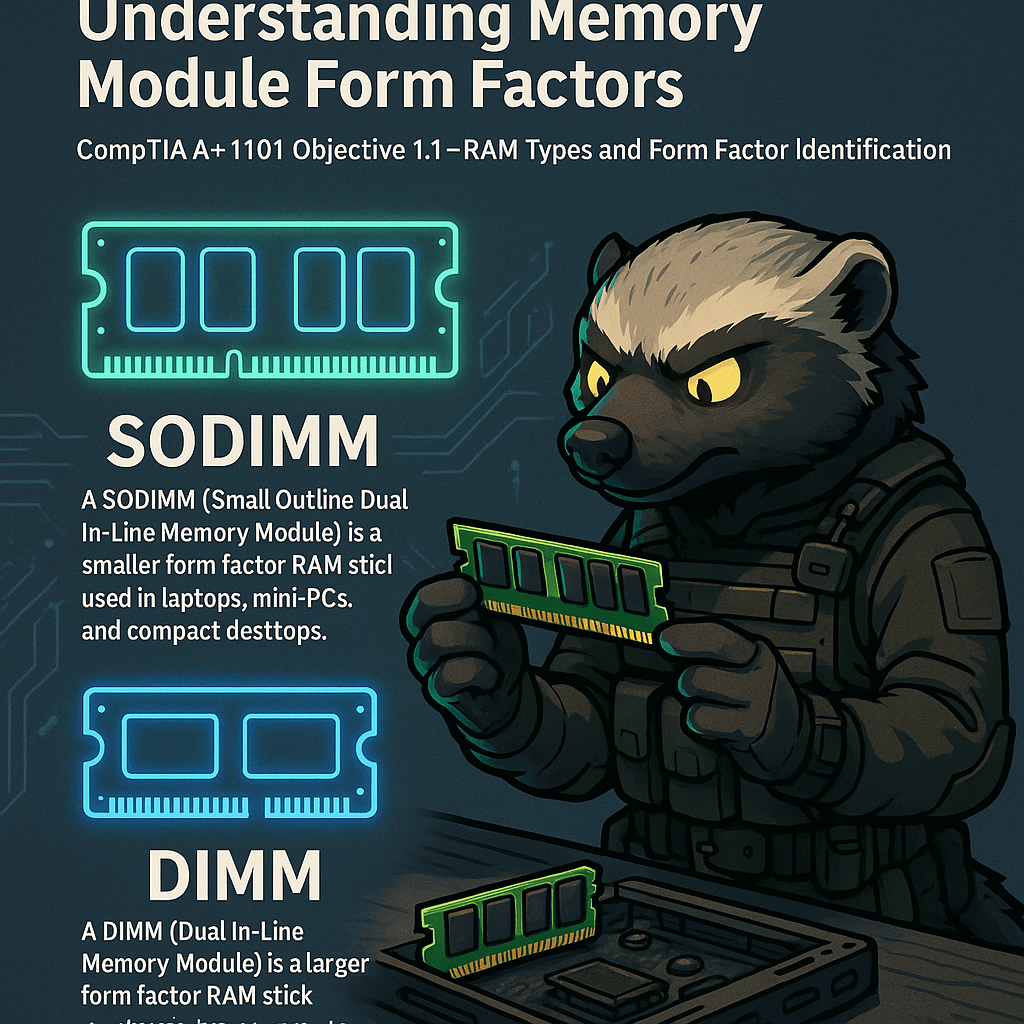
Memory modules come in different physical sizes depending on the device they’re intended for. DIMM (Dual Inline Memory Module) is the standard memory format used in desktop computers, while SODIMM (Small Outline DIMM) is the compact version used in laptops, mini-PCs, and some all-in-one systems. Both types serve the same function—providing volatile memory that supports…
-
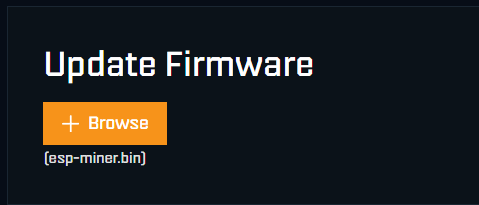
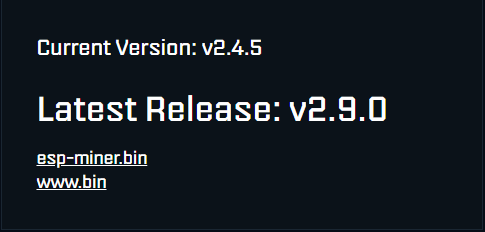
If your SupraHex unit is not appearing on your mining pool dashboard, it’s likely due to outdated or incompatible firmware. To resolve this issue: Check for the latest firmware release by clicking the Check in the settings section of your miners graphical user interface (GUI). After the Download of the “esp-miner.bin” and “www.bin” files upload…
-
The /var directory in Linux is where variable, constantly changing files are stored. It contains logs, mail spools, databases, temporary caches, and other files that grow or update as the system runs. Subdirectories like /var/log hold system logs, /var/spool manages queued jobs like print tasks or mail, and /var/tmp temporarily holds files that should survive…
-

Economist Peter Schiff has publicly criticized Michael Saylor’s characterization of Bitcoin as “digital energy.” Schiff questioned the practicality of using Bitcoin to generate power, contrasting it with crude oil’s essential role in preventing mass starvation. Michael Saylor, Executive Chairman of MicroStrategy, has previously described Bitcoin as “digital energy,” suggesting that it conserves energy in cyberspace…
-
The mkfifo command in Linux is used to create named pipes, also known as FIFOs (First In, First Out). Unlike regular files, a FIFO behaves like a pipe that allows data to flow between processes. You can think of it as a communication tunnel where one process writes data and another reads it. For example,…
-

The locate command in Linux is used to quickly search for files by name across the entire filesystem. Unlike the find command, which actively searches through directories in real-time, locate uses a prebuilt index from a database (usually updated with the updatedb command). This makes it incredibly fast and efficient. For example, typing locate passwd…
-
The /opt directory is used in Linux for installing optional or third-party software that is not part of the default package management system. Many commercial applications or special-purpose tools are installed into /opt to keep them separate from system-managed software. If you install proprietary software like VMware or a custom application, it may place its…
-

The /mnt directory in Linux serves as a traditional location for temporarily mounting filesystems. Unlike /media, which is mostly used for automatic mounting of USBs and other external devices, /mnt is primarily used by system administrators for manual mounts during maintenance, recovery, or troubleshooting. When you need to access another drive or partition for testing…
-
The /lib directory in Linux holds critical system libraries and kernel modules required for the core functionality of the operating system. Think of these libraries as building blocks that essential programs and commands rely on to work properly. For example, when you run commands from /bin or /sbin, those commands often need shared libraries stored…
-
The /home directory is where Linux stores all the personal files and settings for regular users. Each user gets their own subdirectory under /home, such as /home/alex or /home/jordan, where they keep documents, downloads, pictures, and personal configuration files. This structure helps separate user data from system data, making the system more organized and secure.…
-
OLED stands for Organic Light-Emitting Diode. Unlike traditional LCDs, OLEDs emit light directly from each pixel without requiring a separate backlight. This allows for ultra-thin screens, true blacks, and higher contrast ratios. Each pixel in an OLED screen is made from organic compounds that emit light when current passes through them. This direct emission is…
-

ATA, or Serial Advanced Technology Attachment, is a computer bus interface used to connect hard drives (HDDs), solid-state drives (SSDs), and optical drives to the motherboard. It replaced older parallel ATA (PATA) standards by using a 7-pin data cable and a 15-pin power connector, simplifying cabling and improving airflow. SATA supports hot-swapping (with the correct…
-
Impact printers, such as dot matrix printers, use a physical print head that strikes an ink-soaked ribbon against the paper—similar to a typewriter. These devices are primarily used in environments where multi-part forms, carbon copies, or durability in dusty conditions are required, such as warehouses, industrial settings, and point-of-sale systems. A key feature of impact…
-
An IP address is a unique identifier assigned to devices on a network to enable communication. There are two main versions: IPv4, a 32-bit address format (e.g., 192.168.1.1), and IPv6, a 128-bit format (e.g., 2001:0db8:85a3::8a2e:0370:7334), created to handle the growing number of connected devices. IPv4 supports around 4.3 billion addresses and uses dot-decimal notation. It’s…
-
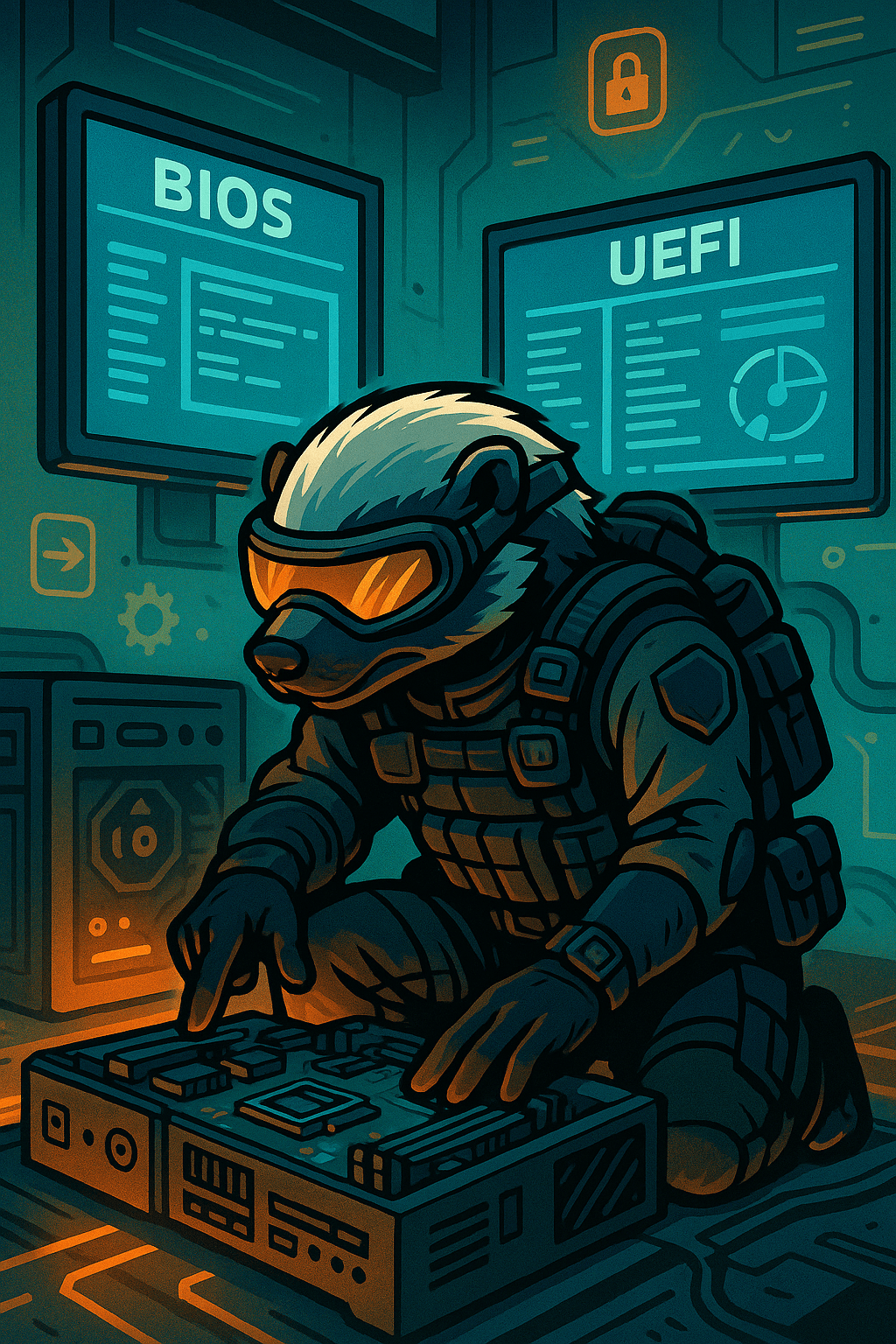
BIOS stands for Basic Input/Output System. It is firmware stored on a chip on the motherboard that initializes hardware components and loads the operating system. BIOS interfaces are text-based, and users access them by pressing keys like DEL, F2, or ESC during system startup. BIOS uses Legacy Boot, has limited drive support (up to 2.2…
-
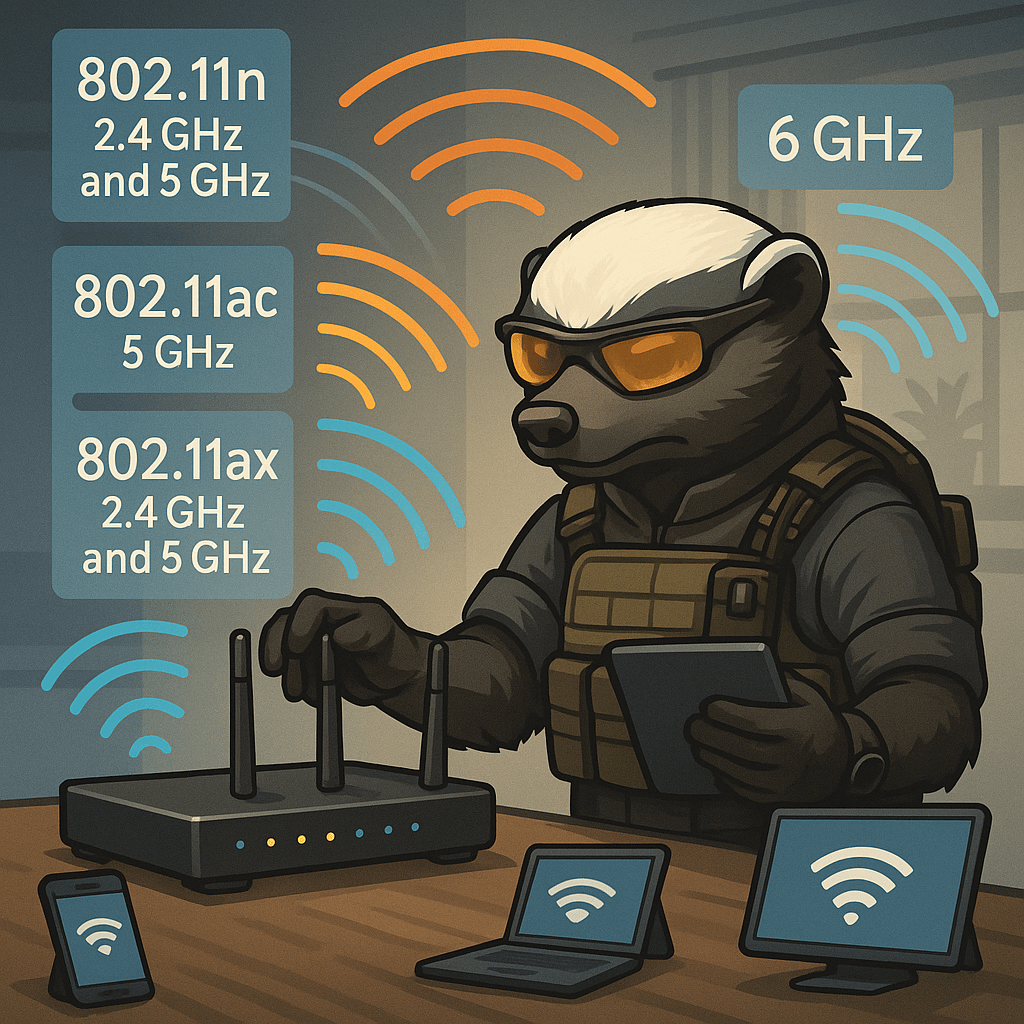
Modern wireless networks operate using evolving Wi-Fi standards, each offering different speed, range, and frequency capabilities. These standards, managed by the IEEE under the 802.11 umbrella, are critical to understand for any technician tasked with configuring or troubleshooting wireless networks. 802.11n, released in 2009, was the first to support dual-band operation—using both 2.4 GHz and…
-

The duplexing assembly is a specialized component in many modern printers that enables automatic double-sided printing—also known as duplex printing. Rather than requiring the user to manually flip pages to print on the other side, the duplexer takes over that function, flipping the sheet internally and refeeding it through the print path for the second…
-
The /etc directory is where Linux stores all of its system-wide configuration files. Everything from network settings, user account information, system services, startup scripts, and software configurations is organized here. Unlike directories such as /bin or /boot which hold programs or boot files, /etc is focused purely on settings that control how Linux and its…
-

Older laptop models that use CCFL (Cold Cathode Fluorescent Lamp) backlighting rely on a display inverter to power the screen’s illumination. The inverter’s job is to convert the laptop’s DC power into AC voltage needed by the CCFL tube inside the display panel. Without a functioning inverter, the screen may be technically on but will…
-

Trusted Platform Module (TPM) is a dedicated chip embedded on a computer’s motherboard, designed to secure hardware through integrated cryptographic keys. It stores sensitive information such as encryption keys, digital certificates, and passwords in a tamper-resistant environment. TPM is commonly used for: The current standard is TPM 2.0, which is required by modern operating systems…
-
Using FTP, File Transfers are fun; I can use tcp/20 or /21! With port 22, I’m feeling well; Secure communication in my little Shell. Telnet’s the same, but more easy to see; nobody likes you when you’re port 23. SMTP is where Simple Mail thrives; it’s Transferred to servers with port 25. With DNS, I…
-

The /bin directory is where Linux keeps many of its most essential commands that are available to all users, whether they are administrators or regular users. Inside /bin, you will find programs like ls for listing directory contents, cp for copying files, and mv for moving or renaming files. These commands are so vital that…
-

What Is an SSD? A Solid-State Drive (SSD) uses flash memory chips to store data. There are no moving parts, making it faster, quieter, and more durable than traditional hard drives. SSDs have extremely fast read/write speeds, especially in NVMe (PCIe) form, which are ideal for boot drives, gaming systems, and business apps. SSDs come…
-

The Linux root directory (/) is the highest-level directory in the entire file system, acting as the central point from which everything else originates. To further clarify, the root directory (/) is the top-level of the entire Linux file system hierarchy, whereas /root is specifically the private home directory for the root (administrator) user. All…
-

A thermal printer uses heat to transfer images onto paper. It comes in two types: Consumables and Maintenance Direct thermal printers require only thermal paper, while thermal transfer printers need both ribbon and label stock.Maintenance includes: Technicians must also check for signs of printhead wear, incorrect temperatures, or paper with poor heat response when troubleshooting…
-

Two of the most recognized and widely used printer languages in the industry are PCL (Printer Command Language) and PostScript. Each one comes with unique advantages and is suited for different types of environments and workloads. PCL, developed by Hewlett-Packard, is a standard language found in many office printers. It’s built for speed and efficiency—great…
-

Every desktop computer relies on a Power Supply Unit (PSU) to convert wall electricity into usable voltage levels that safely power internal components. The PSU takes in AC (Alternating Current) and outputs DC (Direct Current) in multiple voltages—typically +12V, +5V, and +3.3V—distributed to the motherboard, CPU, storage devices, and GPU. Without proper power regulation, even…
-
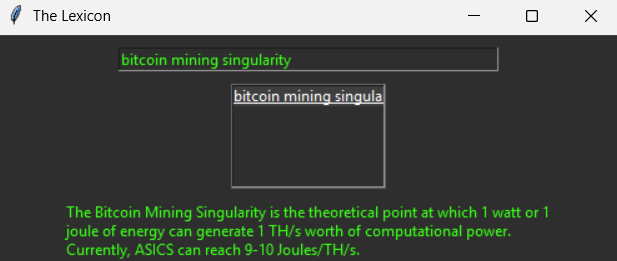
This study proposes a new theoretical framework: the Bitcoin Mining Singularity, defined as the point at which one joule of energy yields one terahash per second (1 J/TH) of cryptographic computation. This convergence of energy efficiency and computational output in Bitcoin mining represents a potential milestone in the global evolution of post-industrial labor, energy monetization,…
-
Liquid Crystal Display (LCD) monitors use liquid crystals and a backlight to create images on screen. Each pixel is composed of subpixels (red, green, and blue) controlled by liquid crystal alignment, which either blocks or passes light from the backlight. There are two key types of LCD panel technologies: All LCDs require a backlight, either…
-
UEFI, or Unified Extensible Firmware Interface, is the modern replacement for traditional BIOS in today’s computers. It is the firmware layer that initializes hardware components and passes control to the operating system during the boot process. UEFI offers several advantages over BIOS, including support for larger drives (over 2 TB), faster boot times, a graphical…
-

Inkjet printers are among the most common types of consumer and small office printers, known for their ability to produce detailed color images and sharp text on a variety of media. They function by spraying tiny droplets of ink directly onto paper through nozzles in the printhead. These droplets are controlled with extreme precision, often…
-

Setting up an Ubuntu Virtual Machine (VM) using Oracle VirtualBox begins with downloading the latest ISO file from Ubuntu’s official site. For Ubuntu 24.04, users typically select the desktop version compatible with their hardware architecture, commonly “amd64.” After downloading, users open Oracle VirtualBox, create a new VM, name it, select the Linux operating system type,…
-

RAID, or Redundant Array of Independent Disks, is a method of combining multiple physical drives into a single logical unit to improve performance, redundancy, or both. It’s commonly used in servers, NAS devices, and business-class desktops to ensure data reliability and uptime. Different RAID levels offer different trade-offs between speed, fault tolerance, and capacity. RAID…
-

C++ is not just a programming language. It is a system-building tool forged from necessity, optimized for control, and wielded by those who require deterministic performance across both time and space. Conceived in 1979 by Danish computer scientist Bjarne Stroustrup at Bell Labs, C++ was born out of a need to create simulations with both…
-

LDAP (Lightweight Directory Access Protocol) is an open, vendor-neutral protocol used to access and maintain distributed directory information services over an Internet Protocol (IP) network. LDAP is widely used for storing and managing information about users, groups, computers, and other resources in a centralized database, known as a directory. The protocol allows clients to connect…
-
In modern computing, Solid State Drives (SSDs) have largely replaced traditional spinning hard drives due to their superior speed and reliability. Among SSD types, two interfaces dominate: SATA SSDs and NVMe SSDs. Both offer fast performance compared to HDDs, but the underlying technology and connection methods set them apart significantly. SATA SSDs use the Serial…
-

When a Linux machine starts feeling slower than normal, it’s often a sign that system resources are strained. In this case, the user decided to troubleshoot by checking memory usage and cleaning up unused files. After running the free command to get a snapshot of RAM and swap usage, they used find to delete all…
-

To set up logical volume management in Linux, the first step is creating a physical volume (PV). A physical volume is typically a disk partition (like /dev/sdb1) that is initialized for use by the Logical Volume Manager. This is done using the pvcreate command, which prepares the partition to be added into a volume group.…
-
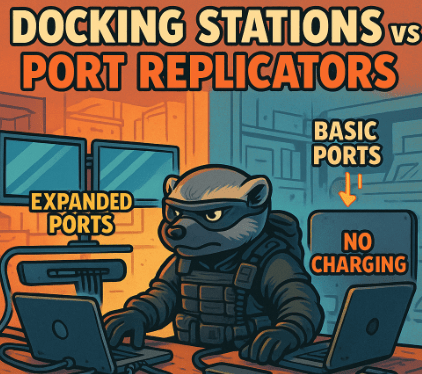
What Is a Docking Station? A docking station is a physical expansion unit that connects to a laptop and transforms it into a full desktop workstation. It adds additional ports such as USB, Ethernet, HDMI, DisplayPort, audio jacks, and charging capabilities, often through a single USB-C or proprietary connector. Docking stations typically: Used in corporate…
-

The IMEI (International Mobile Equipment Identity) is a unique 15-digit number assigned to every mobile device that connects to a cellular network. Unlike a SIM card, which identifies the user, the IMEI identifies the device itself. It is used by carriers to track stolen devices, block lost phones from network access, and enforce blacklists. IMEI…
-
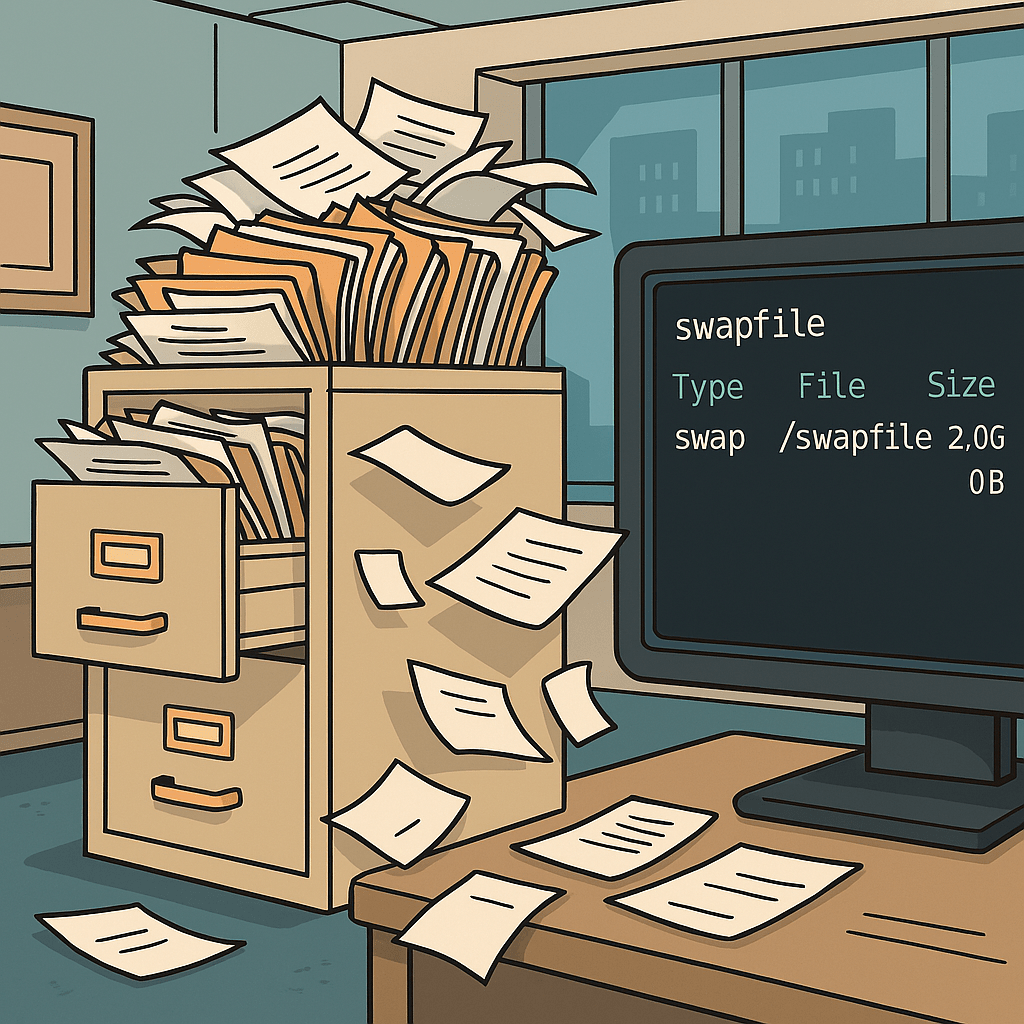
A swap file in Linux is a special file on the disk that acts as virtual memory when the system’s physical RAM becomes full. Instead of immediately failing or killing processes when memory runs low, the kernel moves less-used data from RAM into the swap file to free up space for active applications. This ensures…
-
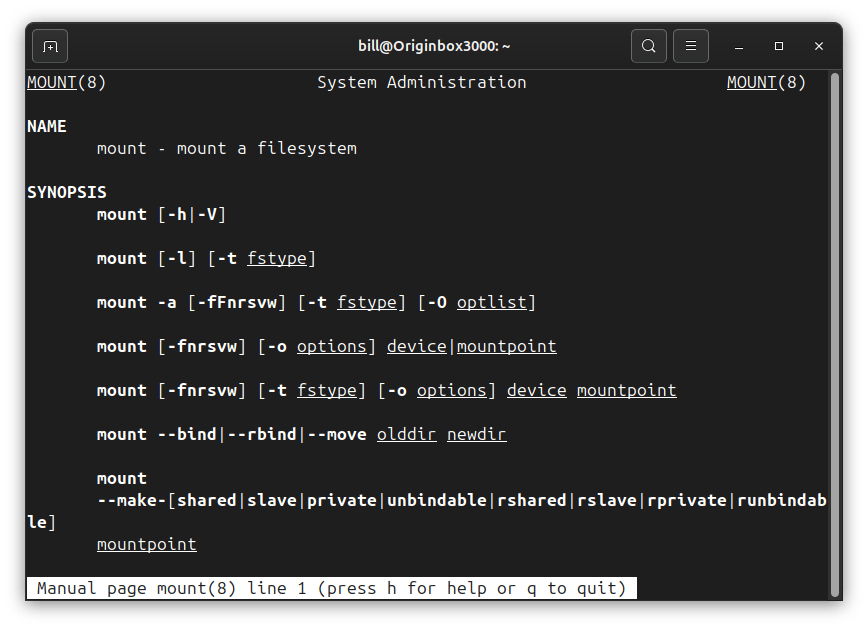
In Linux, mount refers to the process of attaching a storage device or partition—such as a hard drive, USB stick, or network share—to the system’s directory tree so that its contents become accessible. Unlike operating systems that assign drive letters, Linux integrates storage into a single hierarchical file system. When a device is mounted, it…
-

Creating a filesystem means formatting a partition or volume with a specific structure that the operating system can understand—such as ext2, ext3, ext4, xfs, or fat32. This is often done on a new partition using the mkfs (make filesystem) family of commands. For example, formatting a device with ext4 can be done with: sudo mkfs.ext4…
-
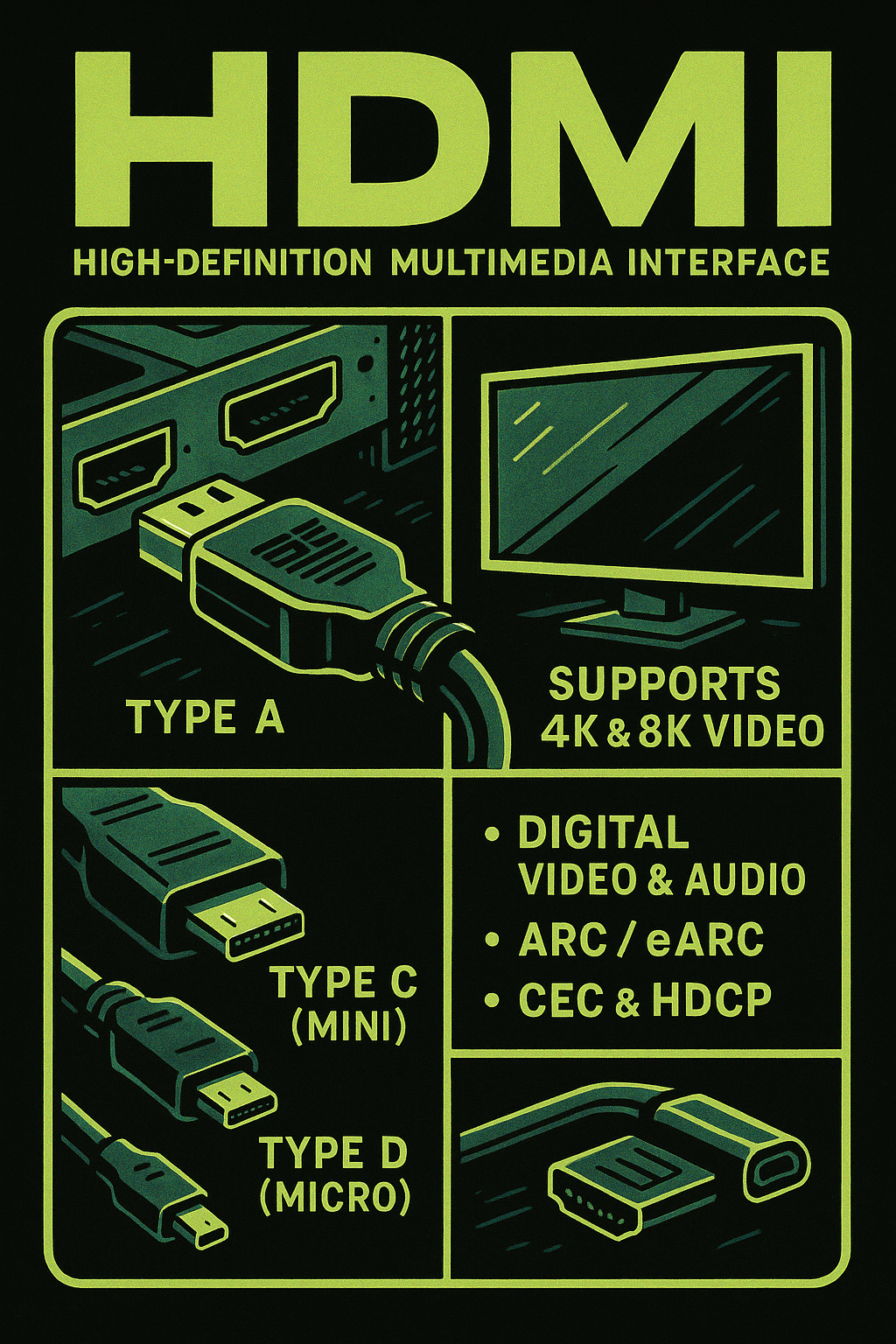
HDMI (High-Definition Multimedia Interface) is a proprietary audio/video interface designed to transmit uncompressed digital video and audio from a source device to a display or audio receiver. It supports a wide range of high-resolution formats, including 1080p, 4K, and even 8K video, along with multi-channel digital audio—all through a single cable. HDMI connectors come in…
-
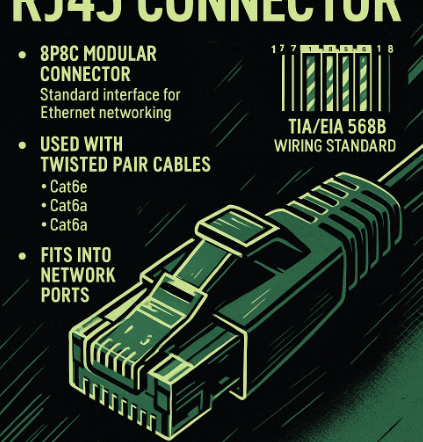
The RJ45 connector is the industry-standard interface used to terminate twisted-pair Ethernet cables for wired networking. Formally known as an 8P8C (eight positions, eight contacts) modular connector, RJ45 is used to connect devices such as computers, routers, switches, and patch panels in both residential and enterprise environments. It supports network standards like 10BASE-T, 100BASE-TX, 1000BASE-T,…
-

The Rockpi 4 SE is essentially a computer that you can program. The Rockpi has capabilities for various management, monitoring, and automation tasks to further optimize operations at a bitcoin mining facility. Software Overview Retrofitting “Brains”’ on a Rock Pi involves first opening a Fedora terminal to develop u-boot for the Rock Pi. Once the…
-
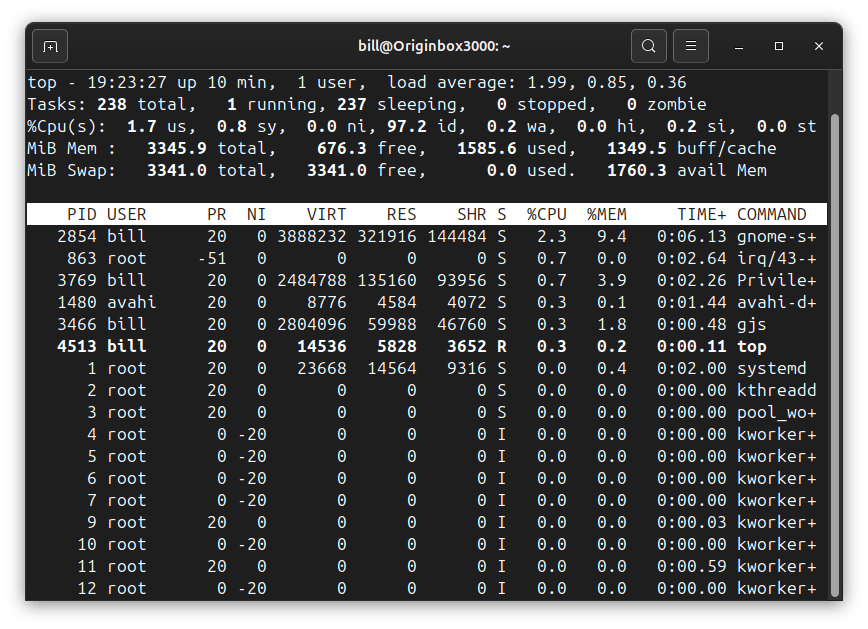
The top command in Linux provides real-time monitoring of system processes, resource usage, and performance metrics directly from the terminal. It dynamically displays essential information, including CPU utilization, memory consumption, swap usage, and running tasks. The interactive output updates automatically, offering an immediate overview of the system’s operational state, making it invaluable for troubleshooting, performance…
-

A Canaan Bitcoin miner experienced a power supply unit (PSU) failure, leading to significant damage. An analysis suggests two primary causes: inadequate power delivery from an extension cord and the use of a non-compliant USB-C cable. Theory 1: Inadequate Power Delivery from Extension Cord The PSU was connected via an extension cord, which may not…
-
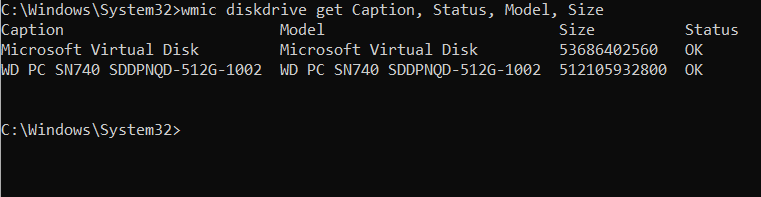
The Windows Management Instrumentation Command-line (WMIC) tool is a command-line utility that enables users to interact with the Windows Management Instrumentation (WMI) system. WMI provides access to detailed system information, hardware diagnostics, and management capabilities without requiring a graphical interface. WMIC simplifies querying system properties, retrieving hardware data, and monitoring system health using predefined aliases.…
-

Industrial-grade Bitcoin mining machines require robust and efficient power supplies to convert alternating current (AC) from the grid into the direct current (DC) necessary for their operation. Selecting the appropriate AC to DC power supply is crucial for optimal performance and longevity of the mining equipment. Power Requirements and Efficiency Each mining machine model has…
-
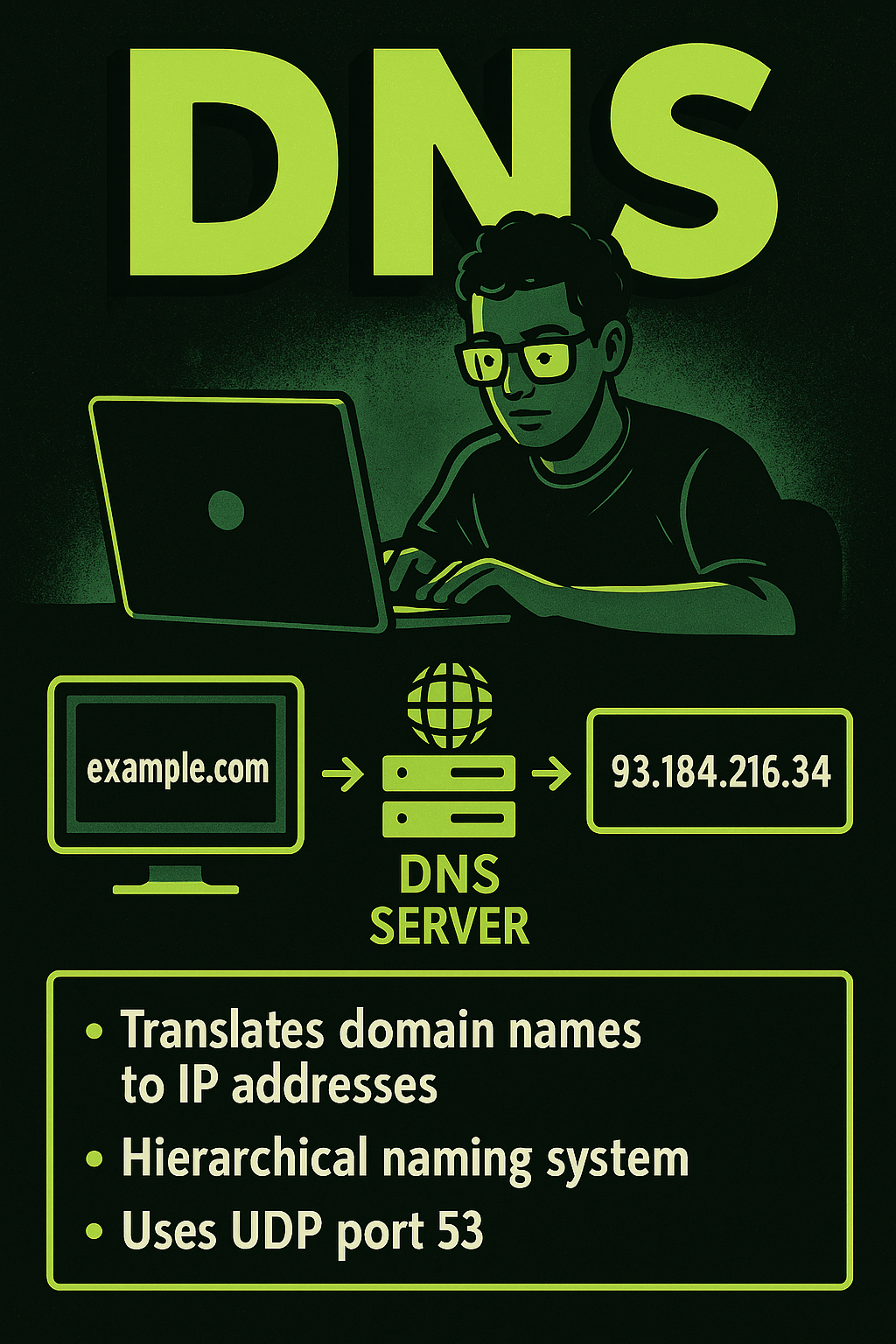
DNS (Domain Name System) is a foundational internet service that translates human-friendly domain names like example.com into IP addresses that computers use to communicate, such as 93.184.216.34. This system works in a hierarchical manner, involving root servers, top-level domains (TLDs), and authoritative name servers. When a user enters a URL into a browser, a DNS…
-
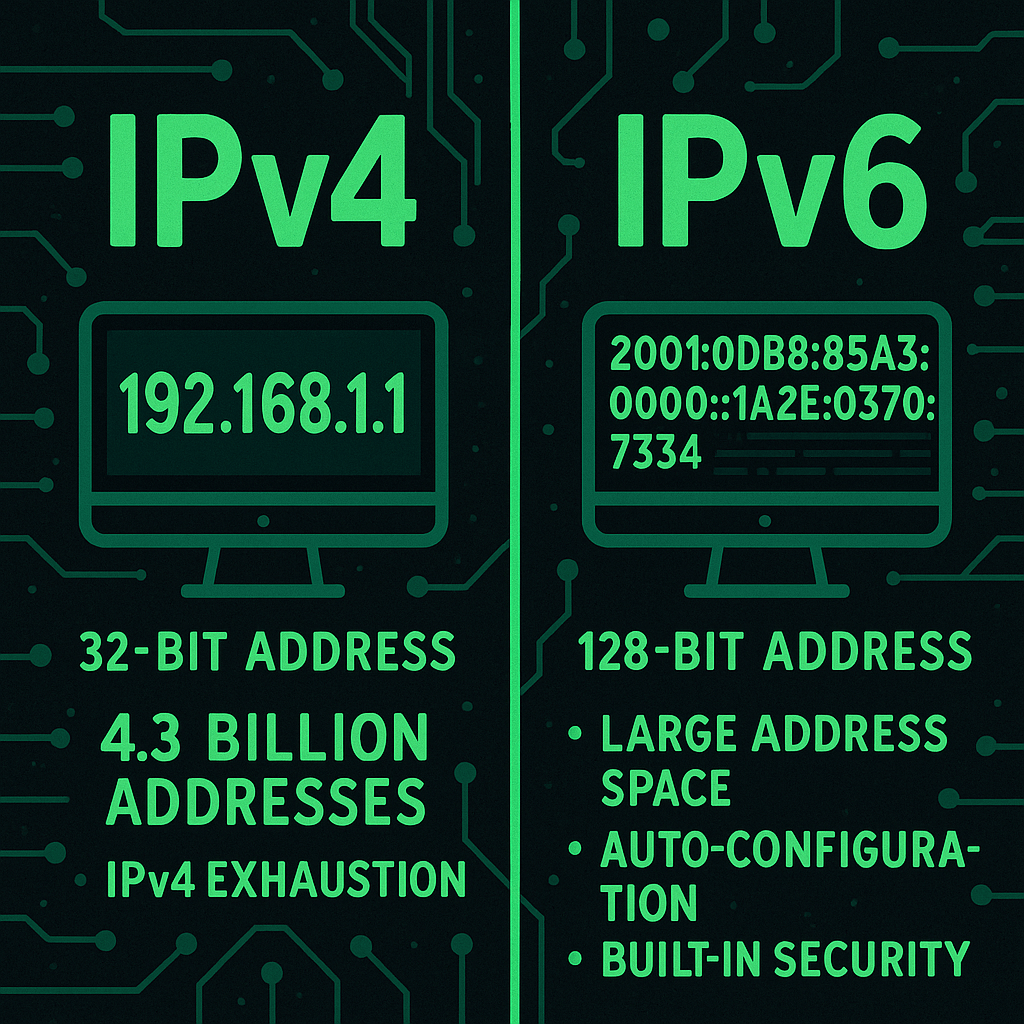
IPv4 (Internet Protocol version 4) is the fourth version of the IP protocol and remains the most widely used standard for assigning IP addresses on the internet and private networks. It uses a 32-bit addressing scheme, represented in dotted decimal format (e.g., 192.168.1.1), which provides approximately 4.3 billion unique addresses. Due to the limited pool…
-
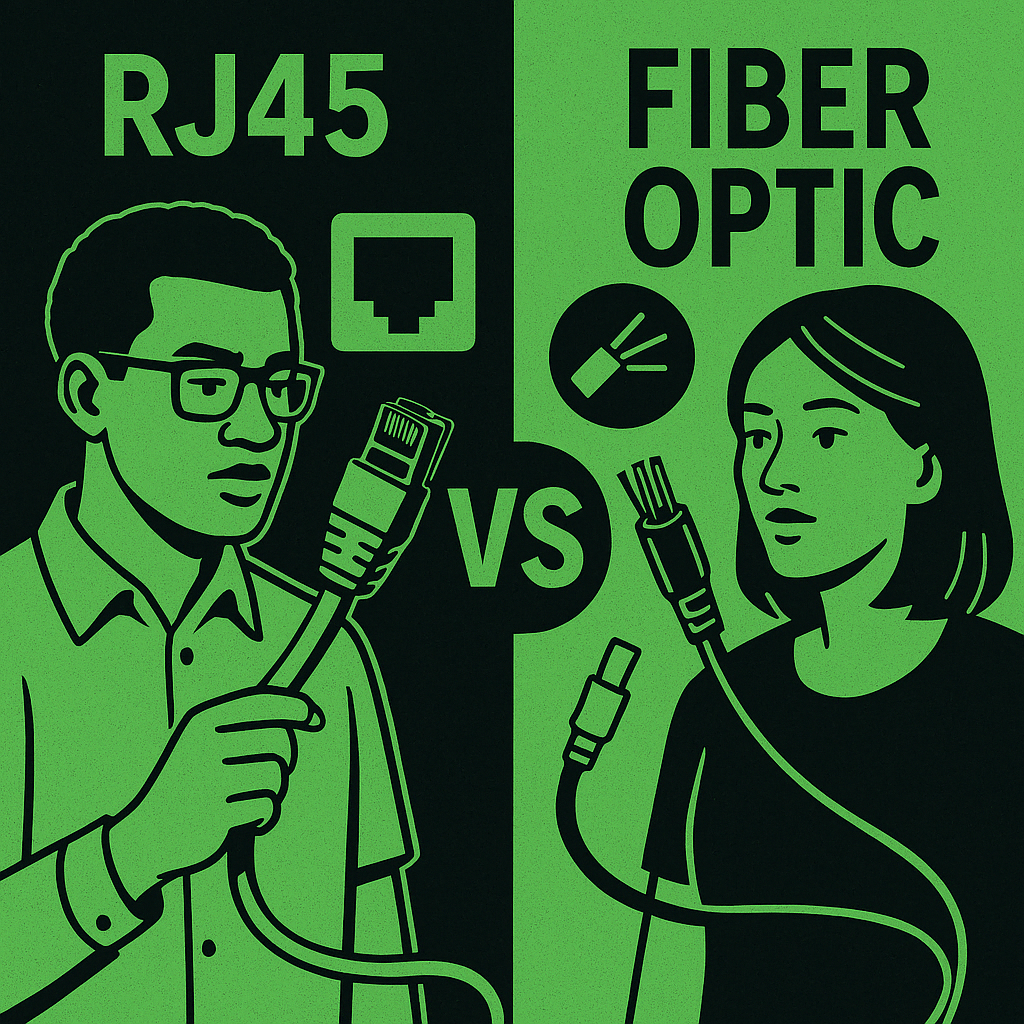
RJ45 Ethernet cabling and fiber optic cabling are two dominant physical media used in networking, each with unique characteristics suited for different scenarios. RJ45 uses twisted-pair copper wires terminated with an 8P8C modular connector (commonly referred to as RJ45) and is typically deployed in LAN environments. Ethernet standards like Cat5e, Cat6, and Cat6a support speeds…
-
HDMI (High-Definition Multimedia Interface) and DisplayPort are two widely adopted digital display interfaces, but they are optimized for different environments. HDMI is the standard for consumer electronics, including TVs, projectors, game consoles, and media players. It supports both audio and video in a single cable and includes features like CEC (Consumer Electronics Control) and ARC…
-

VGA (Video Graphics Array) and DisplayPort are two video output standards used to connect computers to monitors or projectors, but they differ drastically in technology, image quality, and capability. VGA, introduced in the late 1980s, is an analog interface that supports resolutions up to 1920×1080, but often suffers from signal degradation over long cable runs.…
-

Social media has ignited a new wave of debate over the authenticity and origin of luxury goods, as users allege that many high-end fashion brands are manufacturing their products in China before relabeling them as “Made in Italy” or “Made in France.” The criticism reemerged as global trade tensions intensify under President Trump’s new tariff…
-

Esptool.py is a Python-based utility created by Espressif for flashing firmware onto ESP8266 and ESP32 chips. It operates cross-platform—working on Windows, Linux, and macOS—and is executed from the command line using Python. Although its name ends in .py, users interact with it using simple terminal commands, not actual Python code. The command-line arguments passed to…
-

Peripherals are external devices that connect to a computer to extend its input, output, or storage capabilities. They fall into three main categories: input devices, output devices, and input/output (I/O) devices. Common input peripherals include keyboards, mice, trackpads, scanners, microphones, and webcams. These devices allow users to enter data, control the system, and capture images…
-
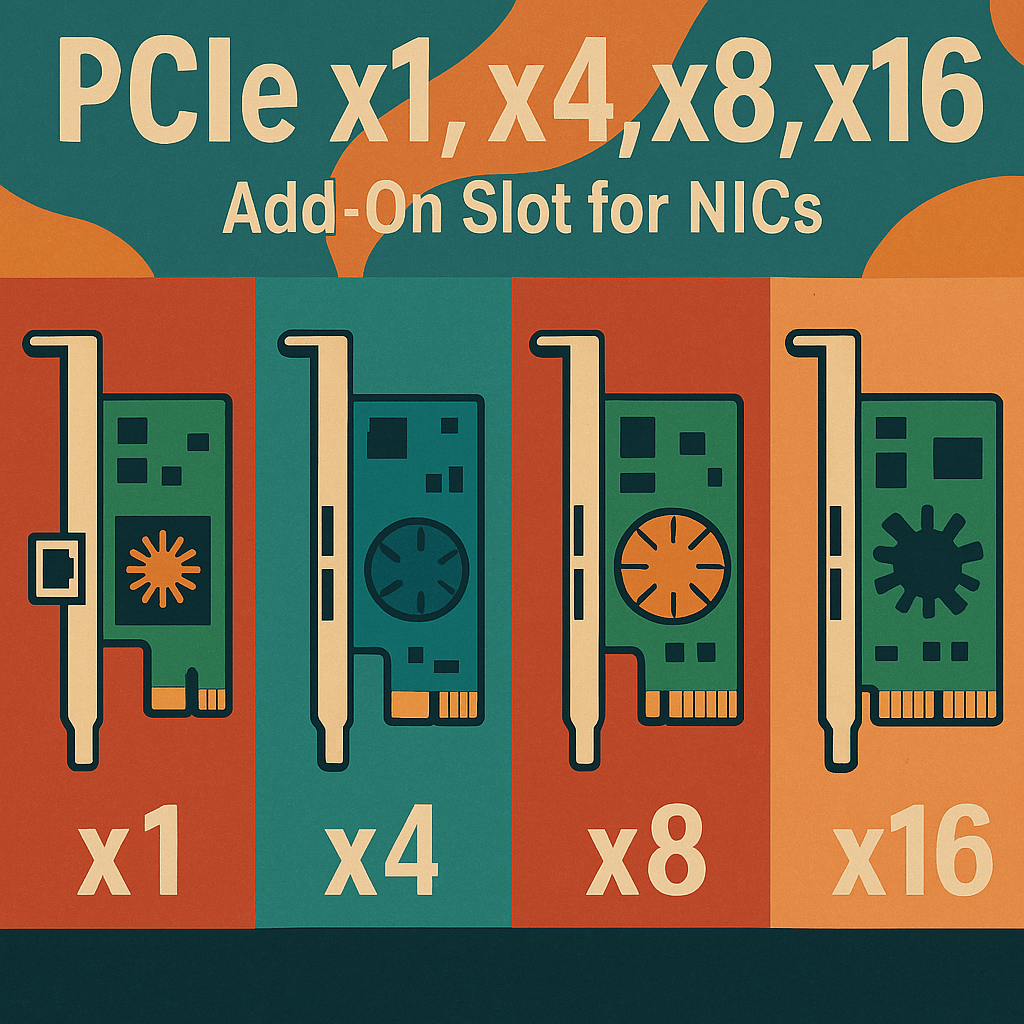
PCI Express (PCIe) is the industry-standard high-speed interface used to connect add-on components—like network interface cards (NICs)—to a computer’s motherboard. For NICs, PCIe offers dedicated data lanes to the CPU or chipset, ensuring low-latency, high-throughput, and scalable bandwidth. PCIe slots are designated by their lane count: x1, x4, x8, and x16. Each lane consists of…
-
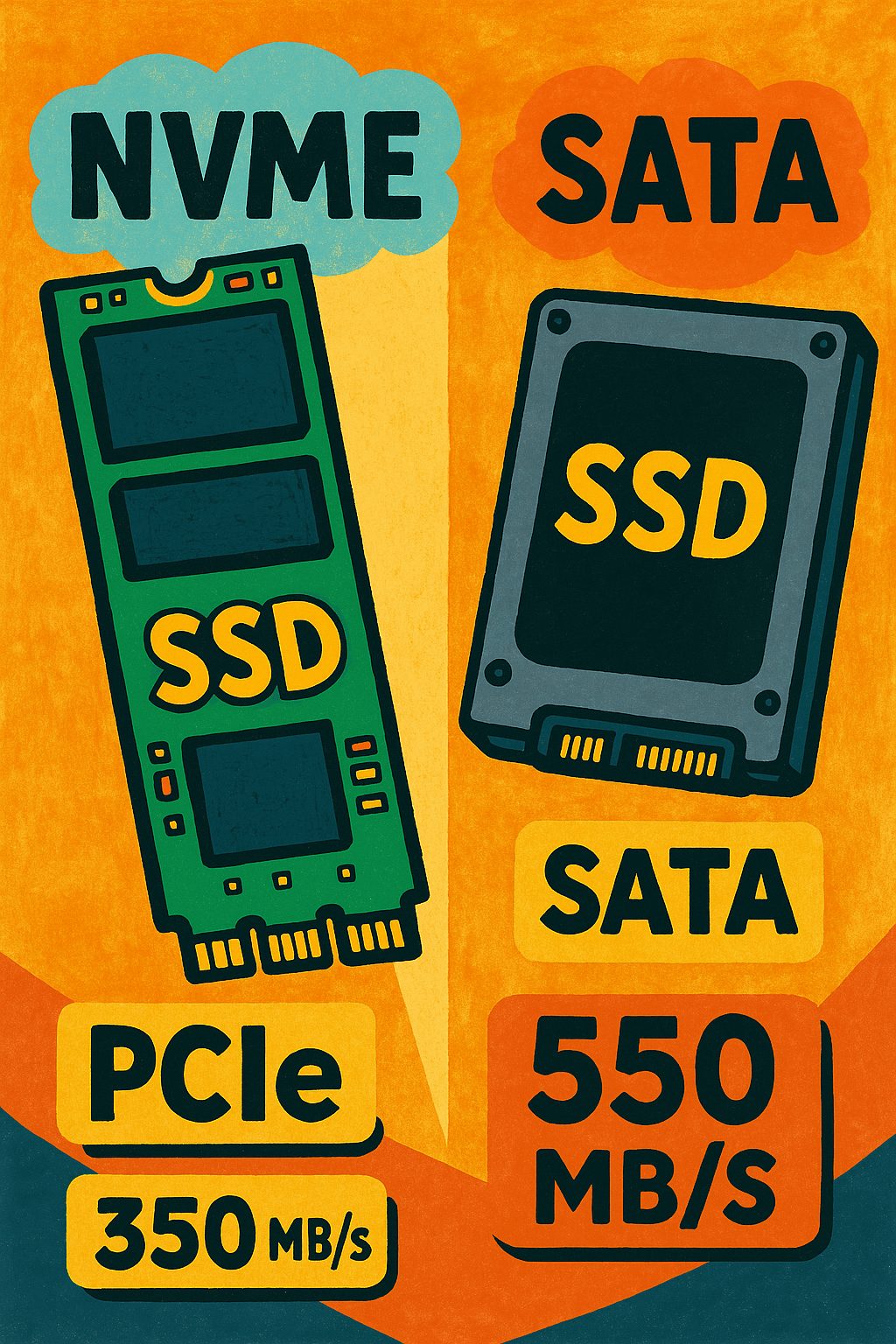
NVMe (Non-Volatile Memory Express) and SATA (Serial ATA) are two types of interfaces used to connect SSDs to a system, and while both offer significant advantages over traditional HDDs, their performance differences are critical. SATA SSDs, which use the older AHCI protocol and connect via the SATA III interface, typically max out at 550 MB/s…
-

Storage drive problems can cause system crashes, data loss, and performance degradation. Symptoms may include the system failing to boot, slow file access, corrupted files, or frequent read/write errors. Initial troubleshooting begins by checking physical connections such as SATA, NVMe, or power cables, and confirming that the drive is detected in BIOS or UEFI. For…
-
The Dynamic Host Configuration Protocol (DHCP) is a network service used to automatically assign IP addresses and other configuration information—such as the subnet mask, default gateway, and DNS servers—to client devices on a network. This removes the need for manual IP configuration and helps avoid conflicts caused by duplicate IPs. DHCP is essential for managing…
-
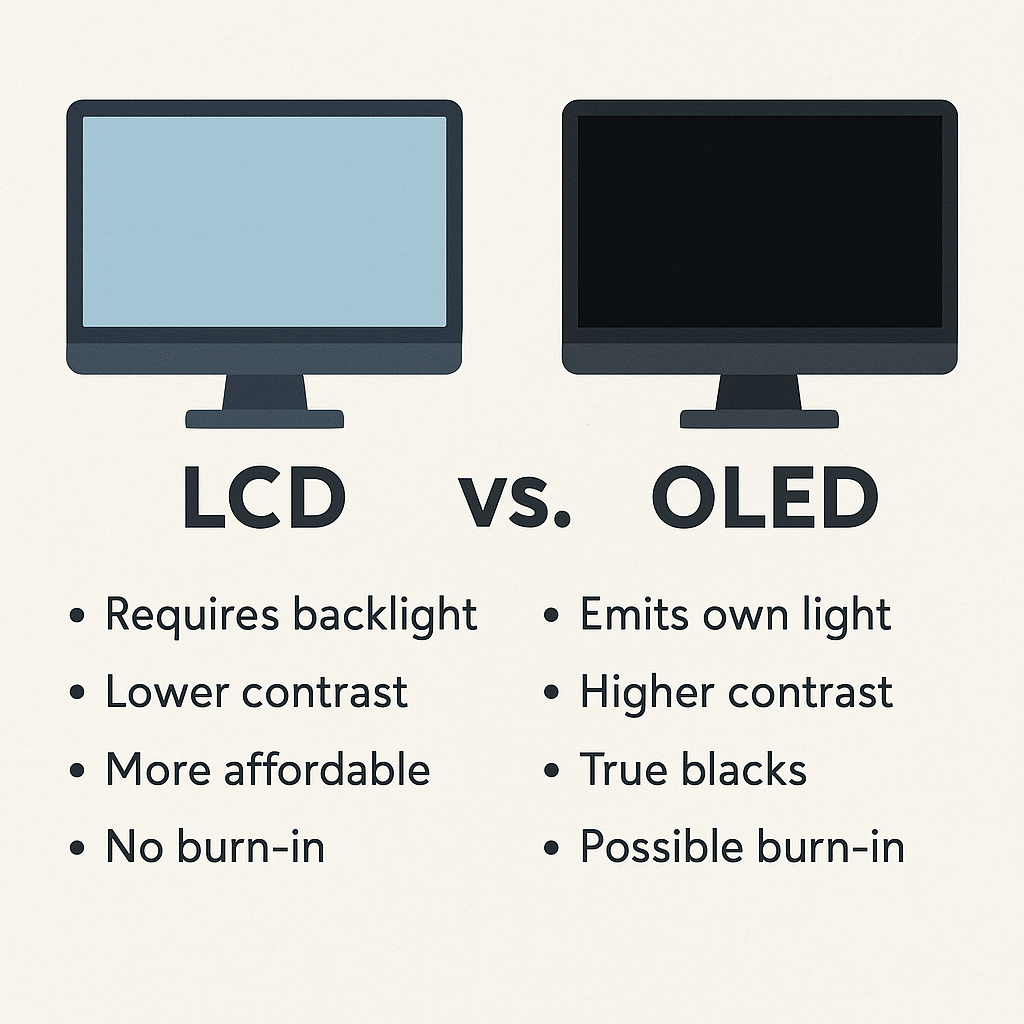
LCD (Liquid Crystal Display) and OLED (Organic Light Emitting Diode) technologies are two widely used screen types in modern devices, each with distinct characteristics. LCDs require a backlight to illuminate pixels, which means blacks can appear grayish, but they offer consistent brightness and are generally more affordable. OLED displays, on the other hand, emit their…
-
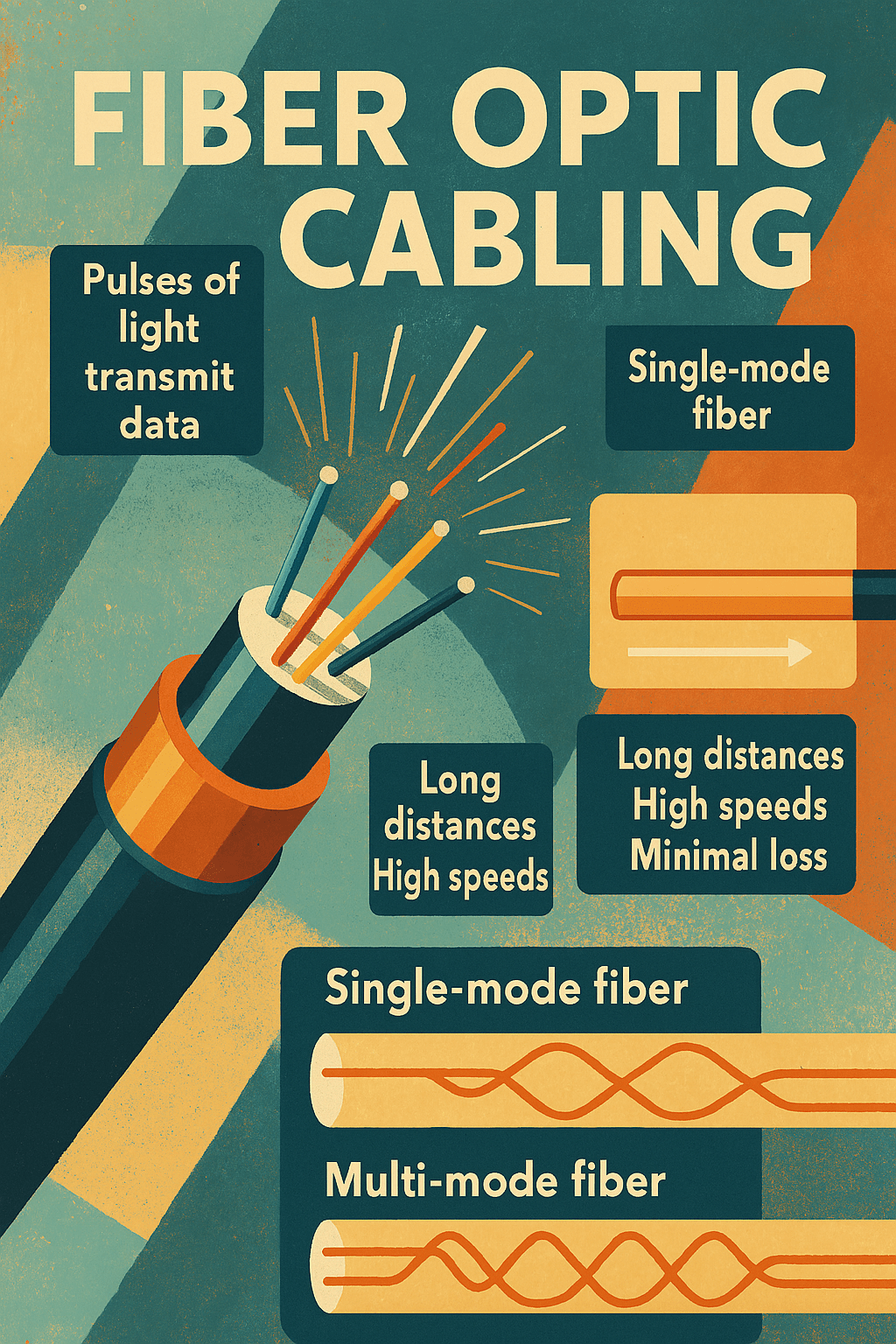
Fiber optic cabling is a high-speed transmission medium that uses pulses of light instead of electrical signals to carry data over glass or plastic strands. It supports far greater bandwidth and significantly longer transmission distances than copper cabling, making it essential for enterprise backbones, internet service providers, data centers, and long-haul telecommunications. Two core types…
-
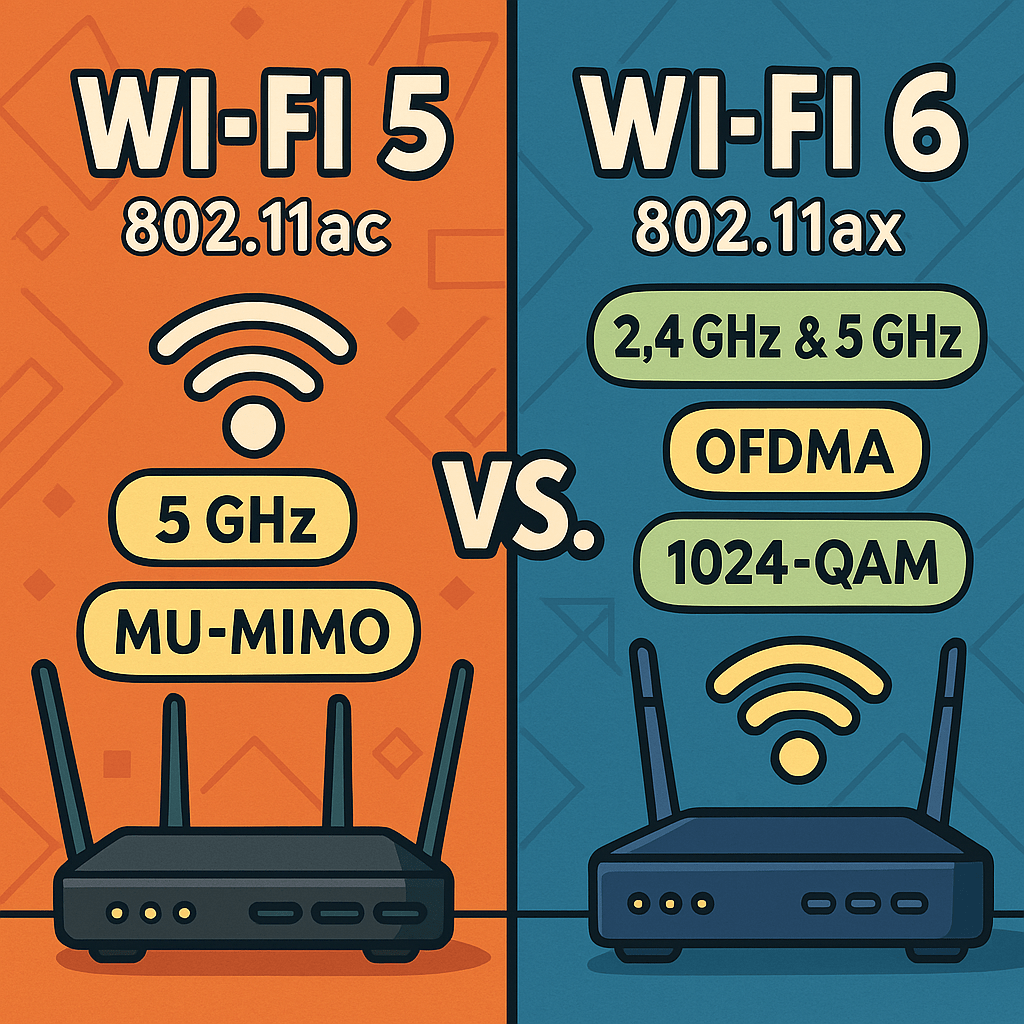
Wi-Fi 5 (802.11ac) and Wi-Fi 6 (802.11ax) are two prevalent standards that IT professionals should be familiar with. Wi-Fi 5 (802.11ac): Wi-Fi 5, introduced in 2013, operates exclusively on the 5 GHz frequency band. It brought significant improvements over its predecessor, 802.11n, by offering higher data rates and enhanced performance. The standard supports channel widths…
-
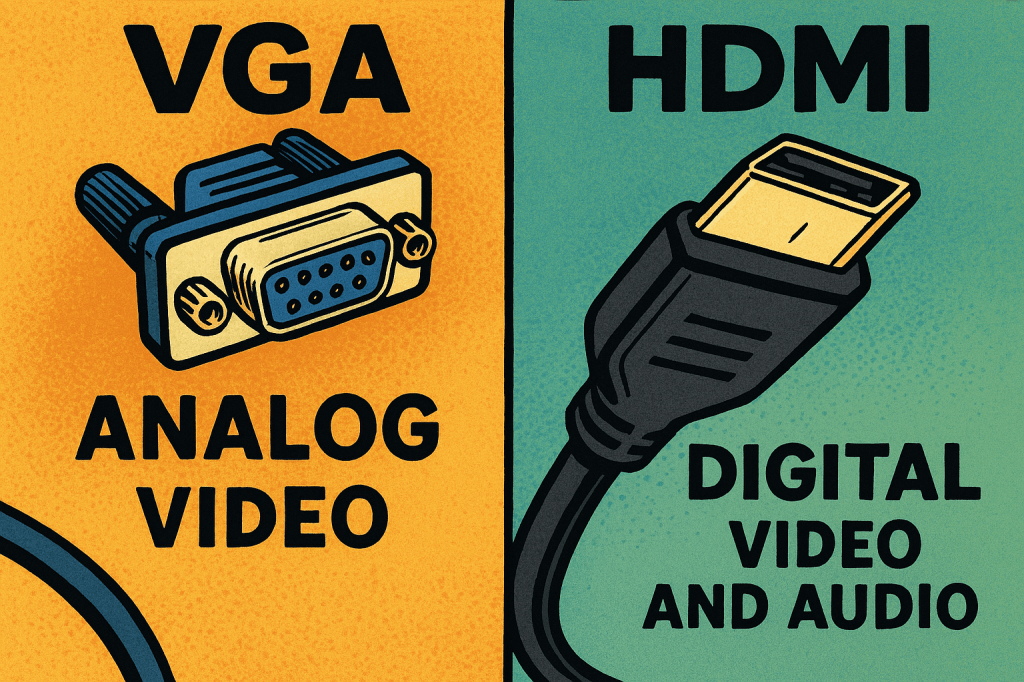
VGA (Video Graphics Array) and HDMI (High-Definition Multimedia Interface) are both used to connect displays to computers, but they differ in signal type, quality, and capabilities. VGA is an older analog interface introduced in the late 1980s that transmits video only. It uses a 15-pin D-sub connector and is prone to signal degradation over long…
-

External storage devices, like USB flash drives, external hard drives (HDDs), and portable solid-state drives (SSDs), are essential tools for storing and transferring data. USB flash drives are compact, portable, and often used for quick file sharing between devices, with capacities ranging from 4GB to 2TB. External HDDs, such as the WD My Passport, offer…
-

Mobile device issues are diverse and may involve power problems, unresponsive screens, charging failures, or connectivity issues. The first step is verifying the basics—does the device power on, is the battery charged, and is the power adapter functioning correctly? A common issue is a dead battery or a faulty charging cable, which can easily be…
-
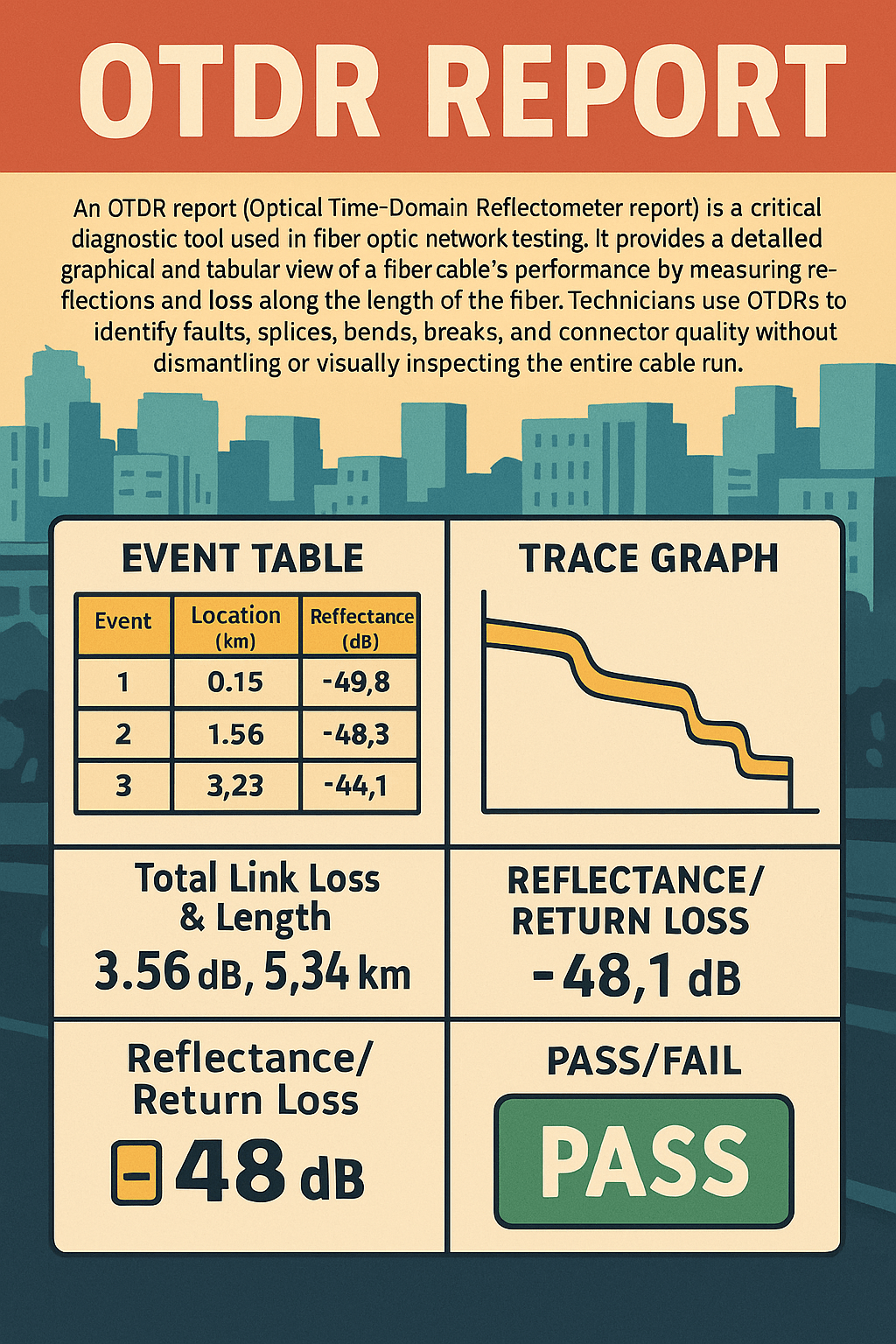
An OTDR report (Optical Time-Domain Reflectometer report) serves as a vital tool for technicians working with fiber optic networks by offering a non-intrusive method to assess fiber integrity. OTDRs send a series of light pulses down the fiber and measure the light that is reflected back due to scattering or changes in the fiber medium,…
-

Wi-Fi 5, also known by its IEEE standard 802.11ac, was introduced in 2013 and became the dominant wireless standard for high-speed consumer and enterprise networking. Operating exclusively on the 5 GHz frequency band, Wi-Fi 5 offered major improvements over its predecessor, 802.11n (Wi-Fi 4), by introducing wider channels (up to 160 MHz), MU-MIMO (Multi-User, Multiple…
-
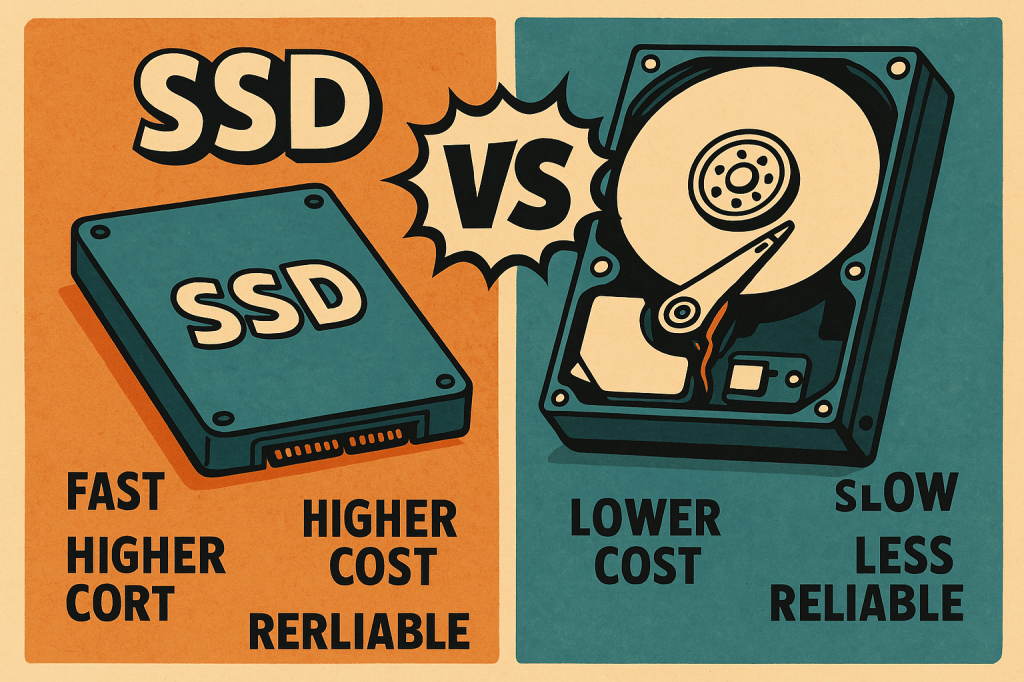
Solid-State Drives (SSDs) and Hard Disk Drives (HDDs) are two primary forms of internal and external storage used in desktops, laptops, and servers, each with distinct characteristics. SSDs store data on flash memory chips, offering lightning-fast read/write speeds, lower latency, and greater durability due to the absence of moving parts. They’re ideal for operating systems,…
-

SATA (Serial ATA) hard drives are widely used for internal storage in desktops and laptops, offering a balance of performance and cost for general computing tasks. Introduced as a replacement for older PATA (Parallel ATA) drives, SATA provides faster data transfer speeds and thinner cables for improved airflow within the system chassis. The most common…
-
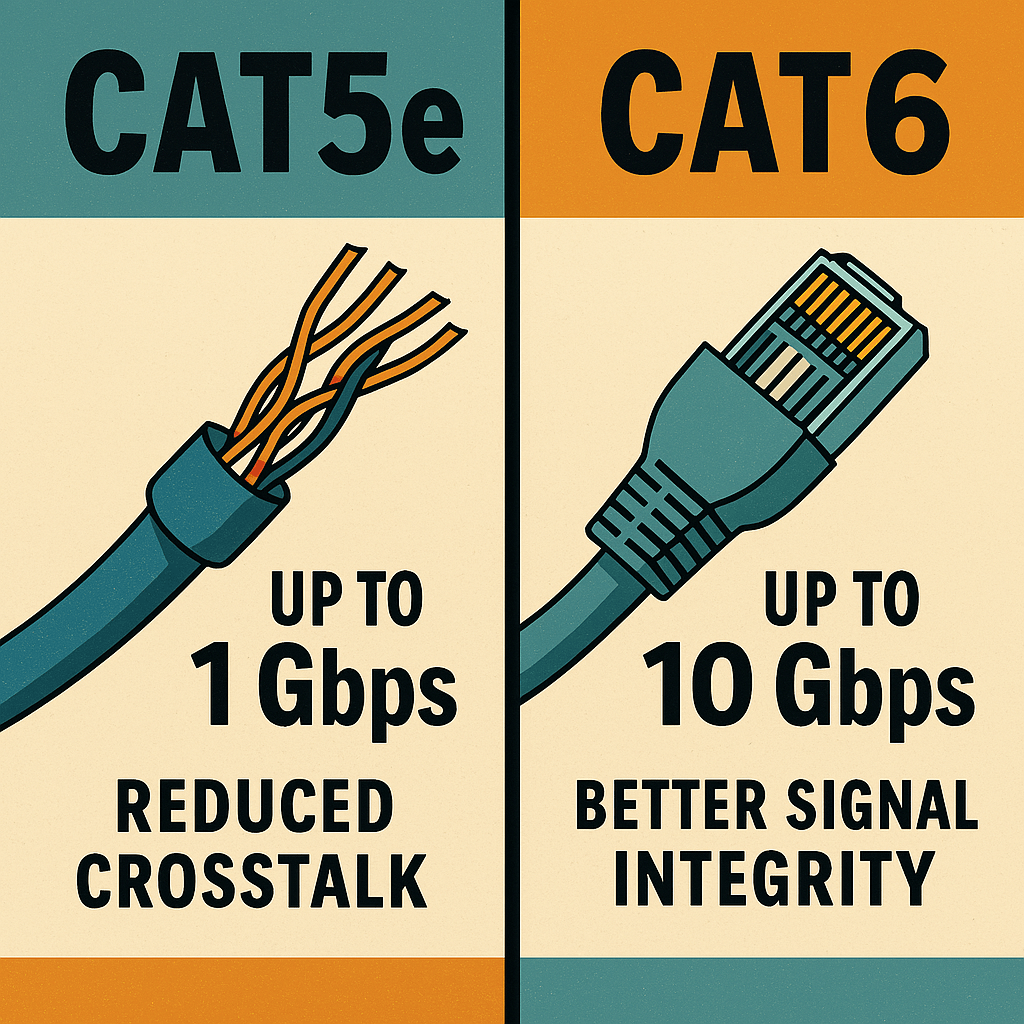
Cat5e (Category 5 Enhanced) and Cat6 (Category 6) Ethernet cables are both unshielded twisted pair (UTP) standards used for wired networking, but they differ in terms of performance, shielding, and signal integrity. Cat5e supports speeds up to 1 Gbps over distances of up to 100 meters and is commonly used in residential networks and small…
-
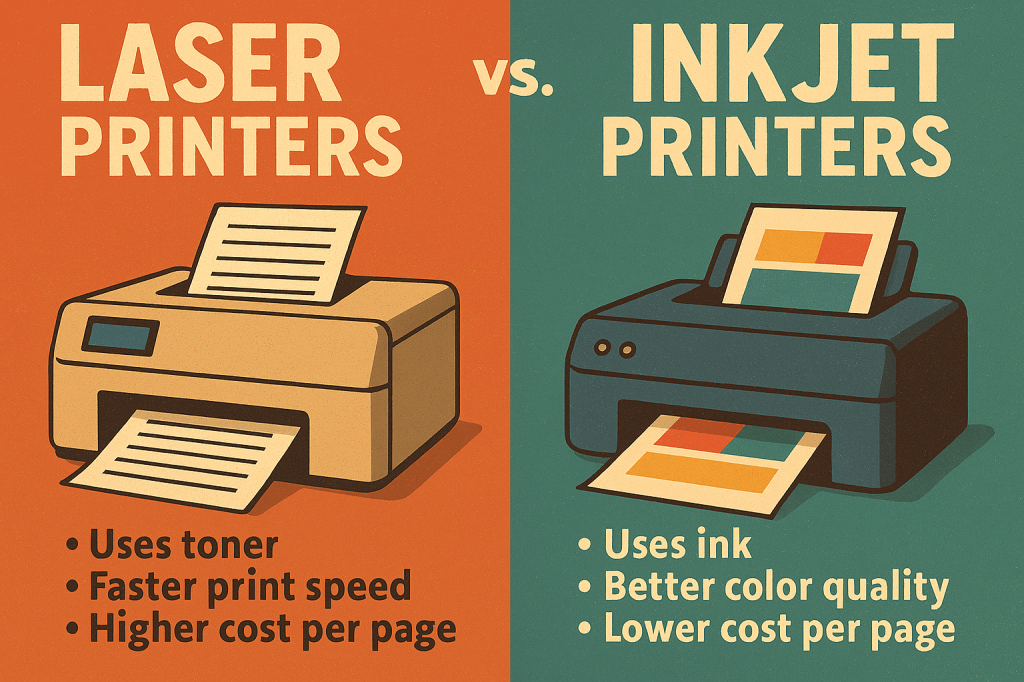
Laser printers and inkjet printers serve similar functions—producing printed output from digital sources—but differ significantly in technology, performance, and cost. Laser printers use a laser beam and toner (powdered ink) fused to the paper using heat, making them ideal for high-volume, fast, and sharp text printing. They are cost-effective per page and commonly used in…
-
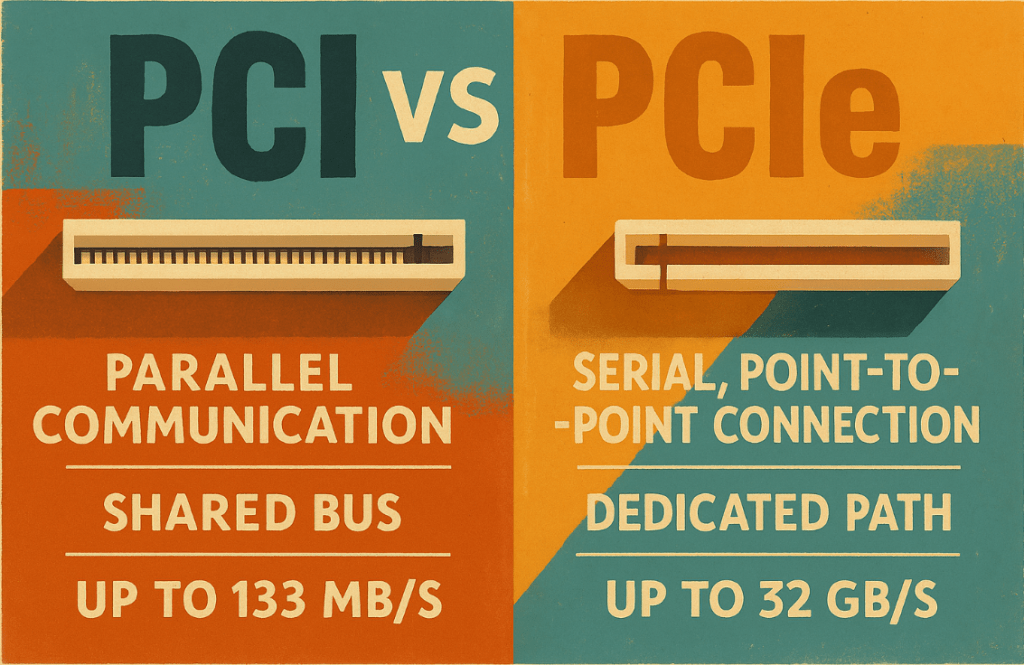
PCI (Peripheral Component Interconnect) and PCIe (PCI Express) are both expansion bus standards used to connect internal hardware components like network cards, sound cards, or GPUs to the motherboard—but their architectures and performance differ greatly. PCI is a parallel communication interface introduced in the early 1990s, capable of transferring data at speeds up to 133…
-
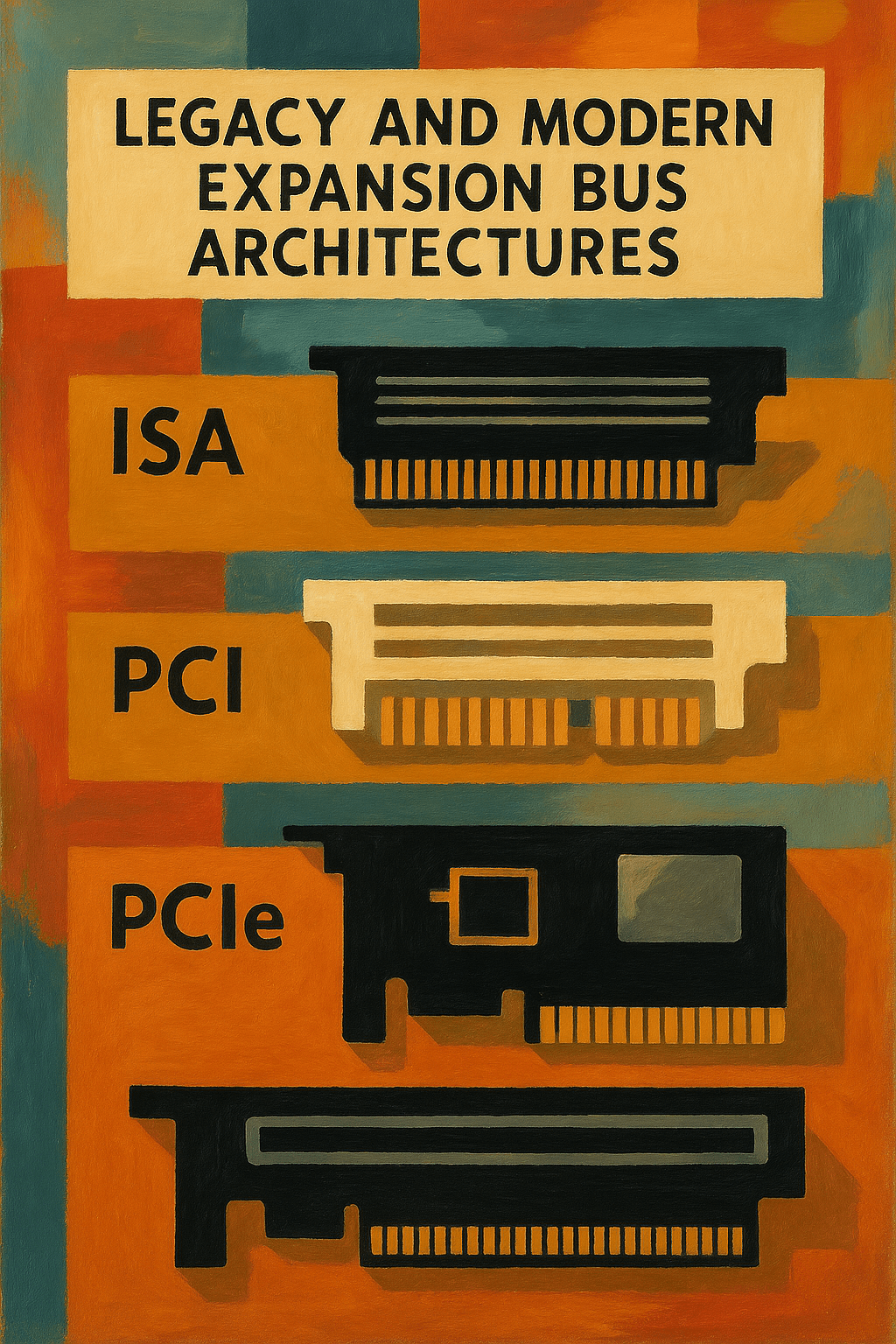
An expansion bus refers to the part of a computer’s internal architecture that allows additional hardware components to communicate with the CPU and other system components. These hardware additions are known as expansion cards, which are installed into the system’s expansion slots. Expansion cards provide specialized functions not handled by the motherboard directly—such as advanced…
-

Printer issues are among the most frequent hardware-related problems in both home and business environments. Symptoms include paper jams, poor print quality, printer not found errors, or no print output at all. Initial troubleshooting should start with physical inspection. Check for paper jams in the feed path, output tray, or duplex unit, and remove any…