Tech Docs
-

SMTP (Simple Mail Transfer Protocol) SMTP is the standard protocol for sending emails. It governs how messages are transmitted from the sender’s email client to the recipient’s email server. SMTP operates as a “push” protocol, meaning it pushes emails from the sender’s device to the server and between servers during mail relaying. SMTP uses commands…
-

Access Points (APs) are networking devices that extend the wireless coverage of a network by acting as a relay between wired and wireless devices. Unlike routers, which manage entire network traffic, access points focus specifically on connecting Wi-Fi-enabled devices to a wired network infrastructure. They are essential in environments requiring wide and reliable wireless coverage,…
-
Network issues can significantly impact productivity and user experience and often present as no connectivity, slow performance, intermittent dropouts, or limited network access. Wired network troubleshooting should always begin by verifying physical layer components—inspect Ethernet cables for damage, confirm they are rated properly (Cat5e, Cat6, etc.), and ensure that connectors are fully seated. Examine link…
-

Laptop display assemblies house several critical components beyond just the LCD or LED screen itself. These components typically include the screen panel, inverter (older models), backlight, digitizer (in touchscreens), webcam, microphone, Wi-Fi antennas, and sometimes even the IR sensor or ambient light sensor. Each of these components serves a specific function—LCDs/LEDs handle visual output, webcams…
-
Mobile device synchronization ensures that user data such as contacts, emails, calendars, media files, and application data remain consistent across multiple platforms. Synchronization can be conducted through several methods including cloud-based sync, local sync, and enterprise-level synchronization. Popular cloud services include Google Account Sync for Android devices and Apple iCloud for iOS devices, which automatically…
-

Canaan Inc., a leading provider of high-performance computing solutions, has unveiled the Avalon Q, a professional-grade Bitcoin mining machine tailored for home users. This announcement was made at Mining Disrupt 2025, a prominent industry conference held in South Florida. The Avalon Q delivers up to 90 terahashes per second (TH/s) of hash power with adjustable…
-

Cables serve as the physical medium that transmits data, power, and signals between devices in computing and networking environments. In IT, the most common data cables include Ethernet cables, coaxial cables, and fiber optic cables. Ethernet cables, or twisted pair cables, are the most widely used in local area networks (LANs) and come in categories…
-

When building a custom PC, the first step is understanding the user’s specific requirements. A basic family desktop is typically used for web browsing, document creation, streaming media, light photo editing, and running basic productivity applications. For such a system, a budget-friendly quad-core processor (such as an Intel Core i3 or AMD Ryzen 3) will…
-

The Windows Firewall, officially known as Windows Defender Firewall, is a built-in security feature included with modern versions of the Windows operating system. It provides both inbound and outbound traffic filtering based on customizable rules, protecting devices from unauthorized access and common network threats. By default, Windows Firewall operates with a balanced set of pre-configured…
-

Linux systems commonly rely on iptables and its modern replacement nftables as core utilities for firewall configuration. These tools allow administrators to create and manage firewall rules that filter traffic based on IP addresses, ports, protocols, and connection states. Linux firewalls operate at a very low level, offering fine-grained control of packet filtering and network…
-

Cloud computing is the delivery of computing services—including servers, storage, databases, networking, software, analytics, and more—over the internet rather than through local infrastructure. It offers organizations flexibility, scalability, and reduced upfront costs by eliminating the need for physical hardware. The most common cloud computing types are public cloud, private cloud, hybrid cloud, and community cloud.…
-

Client-side virtualization is the practice of running virtual machines (VMs) directly on a user’s local device, such as a desktop or laptop, instead of relying on remote servers. This is made possible through the use of hypervisor software, such as Type 2 hypervisors (hosted), which run on top of a host operating system. Common examples…
-

Self-Monitoring, Analysis, and Reporting Technology (SMART) is a monitoring system embedded in computer hard disk drives (HDDs) and solid-state drives (SSDs). Its primary function is to detect and report various indicators of drive reliability, aiming to anticipate potential hardware failures. When SMART data suggests an imminent drive failure, software on the host system can…
-
In the context of embedded systems and hardware-level communication, UART, or Universal Asynchronous Receiver-Transmitter, is a fundamental protocol for serial data transfer. It allows devices to communicate by transmitting data one bit at a time in a sequential fashion. Unlike synchronous protocols, UART does not rely on a shared clock signal but instead uses a…
-

IPv6 is the latest version of the Internet Protocol, designed to replace IPv4 due to the exhaustion of available IPv4 addresses. IPv6 provides a vastly larger address space by using 128-bit addresses instead of the 32-bit format used by IPv4. This means IPv6 can support approximately 340 undecillion (3.4 x 10³⁸) unique addresses, which is…
-

The motherboard is the central backbone of any computer system, acting as the main printed circuit board (PCB) that connects and allows communication between all essential components. It houses the CPU socket, RAM slots, chipset, power connectors, and expansion slots such as PCIe, enabling the installation of graphics cards, network cards, or storage controllers. Motherboards…
-
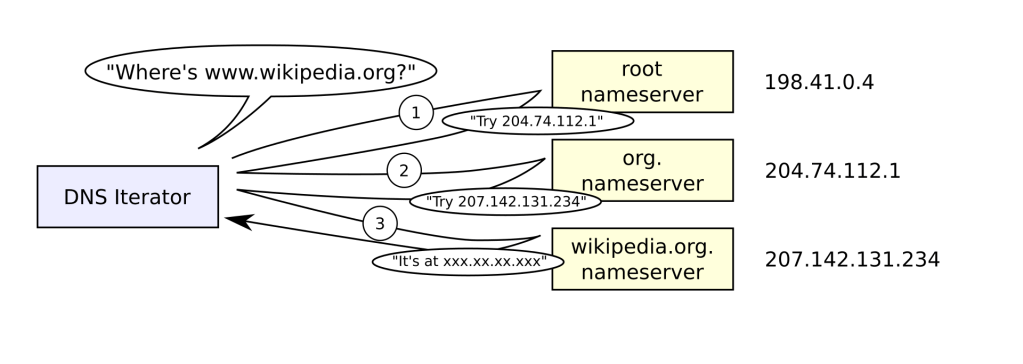
The Domain Name System (DNS) is like the phonebook of the internet. It translates human-friendly domain names such as www.google.com into IP addresses like 142.250.190.78, which computers use to locate and communicate with each other across networks. Without DNS, users would need to memorize long strings of numbers to access websites, making the internet much…
-
Add-on cards, also known as expansion cards, are hardware components inserted into expansion slots on a motherboard—typically PCIe slots—to extend a server’s functionality. These cards enable specialized performance beyond the system’s native capabilities, including enhanced network connectivity, accelerated processing, and advanced storage management. Common types include GPU cards for high-performance computing, network interface cards (NICs)…
-

Storage devices are critical components in computing, used to retain digital information permanently or temporarily. The two most common types of internal storage are Hard Disk Drives (HDDs) and Solid-State Drives (SSDs). HDDs use spinning magnetic platters and read/write heads to store data and are valued for their high storage capacities at lower cost per…
-
Selecting and installing RAM (Random Access Memory) starts with identifying the system’s compatibility requirements. The first step is to determine the form factor—most desktop motherboards use DIMM (Dual Inline Memory Module), while laptops use the smaller SO-DIMM (Small Outline DIMM). Next, determine the DDR generation your system supports—DDR3, DDR4, or DDR5. These are not backward…
-

Understanding cable types and their respective connectors is essential in modern IT environments, where the efficiency of data transmission depends on the correct physical medium. Common cable types include twisted pair (Ethernet), fiber optic, coaxial, HDMI, and USB, each serving unique roles in networking and communication systems. Ethernet cables, such as Cat5e, Cat6, and Cat6a,…
-
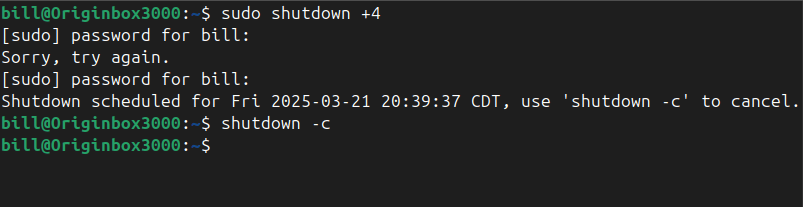
The shutdown command in Linux safely powers off or reboots a system, allowing users and administrators to schedule the shutdown after a certain time interval or at a specific time. It ensures the system terminates all processes correctly and prevents data corruption. The command accepts various parameters to specify time and behavior, with the option…
-

The Avalon Nano 3S, developed by Canaan, is a compact Bitcoin miner designed for home use, combining cryptocurrency mining with heating functionality. It offers a hashrate of 6 terahashes per second (TH/s) while consuming a maximum of 140 watts of power. The device operates on an input voltage of 28 volts and supports frequencies of…
-
Networked hosts provide essential services that enable communication, resource sharing, and security within a network. One of the most fundamental services is web hosting, where web servers deliver websites using HTTP and HTTPS protocols, ensuring content is accessible globally. File hosting and sharing services, such as FTP (File Transfer Protocol), SMB (Server Message Block), and…
-
Network configuration involves assigning and managing how devices connect and communicate across a network. IP addressing is a fundamental concept—devices can be assigned static IP addresses (manually set and unchanging) or dynamic IP addresses (automatically assigned by a DHCP server). Static IPs are often used for devices like servers or printers to ensure consistent accessibility,…
-
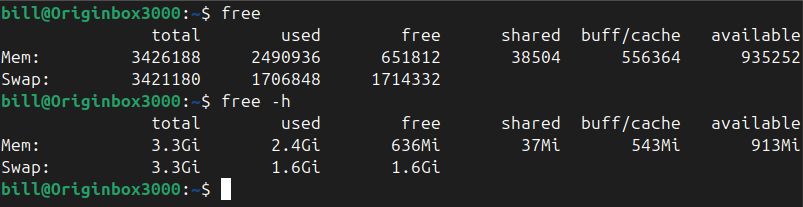
The free command in Linux is used to display comprehensive memory usage information, reporting the total, used, free, shared, buffer/cache, and available memory, including both RAM and swap space. It provides essential insights for system administrators and users to efficiently monitor and manage resources. By default, running the command free outputs memory details numerically in…
-

Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two core transport-layer protocols that facilitate network communication, each serving distinct purposes. TCP is connection-oriented, meaning it establishes a reliable session between devices before data is transmitted. It uses a three-way handshake (SYN, SYN-ACK, ACK) to ensure that both sender and receiver are ready to…
-

Setting up network connectivity on a mobile device involves configuring Wi-Fi, cellular data, Bluetooth, and VPN settings to ensure seamless access to the internet and other devices. Wi-Fi networks must be set up using the correct security protocols, such as WPA2 or WPA3, to prevent unauthorized access. Users should also verify SSID visibility and ensure…
-
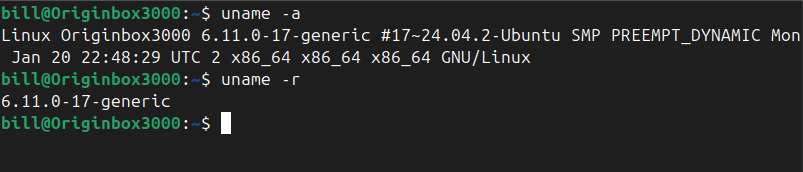
The uname command in Linux prints system information about the current machine. Specifically, it reports details such as the kernel name, kernel release, kernel version, machine hardware name, and the operating system. This command is commonly used by administrators and users alike to quickly determine system details for troubleshooting, software compatibility checks, or documenting system…
-
Understanding how to use networking tools in real-world scenarios is a core part of CompTIA A+ training. Each tool has a specific purpose, from diagnosing connection issues to testing cables or analyzing network traffic. Below is a breakdown of essential tools and how they would be used when given a practical situation: Cable Tester A…
-

Ensuring seamless network connectivity on mobile devices requires proper configuration of Wi-Fi, cellular data, and Bluetooth settings. Wi-Fi connections should be set up using the appropriate security protocols, such as WPA2 or WPA3, to prevent unauthorized access. When configuring cellular data, users must input the correct Access Point Name (APN) settings, which define how the…
-

Mobile devices rely on a variety of accessories and ports to enhance functionality and improve user experience. Properly setting up and configuring these peripherals ensures seamless connectivity and optimized performance. Common accessories include external keyboards, wireless headphones, docking stations, and styluses, each requiring correct pairing and settings adjustments. Bluetooth-enabled accessories must be paired through the…
-
Nano is a simple and user-friendly command-line text editor for Unix-based systems, including Linux. It is designed to be easy to use, even for beginners, with a straightforward interface and on-screen shortcuts. Unlike more complex editors like Vim or Emacs, Nano does not require users to learn advanced keybindings or modes, making it an accessible…
-
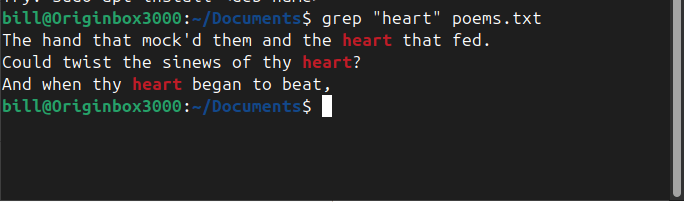
The grep command in Linux is a powerful text-search utility used to find specific patterns within files. In the screenshot, the command grep “heart” poems.txt was executed, instructing the system to search for the word “heart” inside poems.txt and display all matching lines. The output highlights instances where “heart” appears within the poem, helping the…
-

Links in Linux are essential for managing files efficiently, offering flexibility in how files are referenced and accessed. Two primary types exist: hard links and symbolic links (also called soft links). While both serve as references to files, they function differently in how they store and manage data. A hard link is a direct reference…
-

The Small Computer System Interface (SCSI), pronounced “scuzzy,” is a set of standards for connecting and transferring data between computers and peripheral devices. Introduced in the 1980s, SCSI became a prevalent interface for hard drives, scanners, printers, and other peripherals, especially in high-performance and server environments. Despite the advent of newer interfaces like USB and…
-

Installing and configuring laptop hardware involves replacing or upgrading essential components such as memory (RAM), storage drives, and batteries. When upgrading RAM, the laptop must be powered off, and the correct type and size of memory modules must be installed in the designated slots. Storage upgrades often involve swapping out traditional hard disk drives (HDDs)…
-
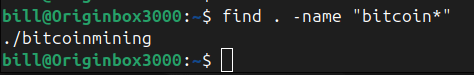
The find command in Linux is a powerful and versatile tool designed to search through files and directories based on specific criteria. It helps users efficiently locate files within a file system, filtering searches by name, file type, modification date, size, or even permissions. A typical syntax for using find includes specifying a starting directory,…
-

Data centers, the backbone of our digital world, employ various cooling methods to maintain optimal operating temperatures for their equipment. One such method is immersion cooling, where IT components are submerged in thermally conductive, dielectric liquids. technique allows for efficient heat dissipation, as the liquid directly contacts heat-generating components, reducing the need for traditional air…
-

Molex connectors are standardized electrical connectors widely used in power and signal applications across various industries, including computing, consumer electronics, and automotive systems. They are known for their durability, ease of use, and reliable connectivity, often featuring plastic housings with metal contacts that enable secure electrical connections. These connectors originated from Molex Incorporated, a company…
-

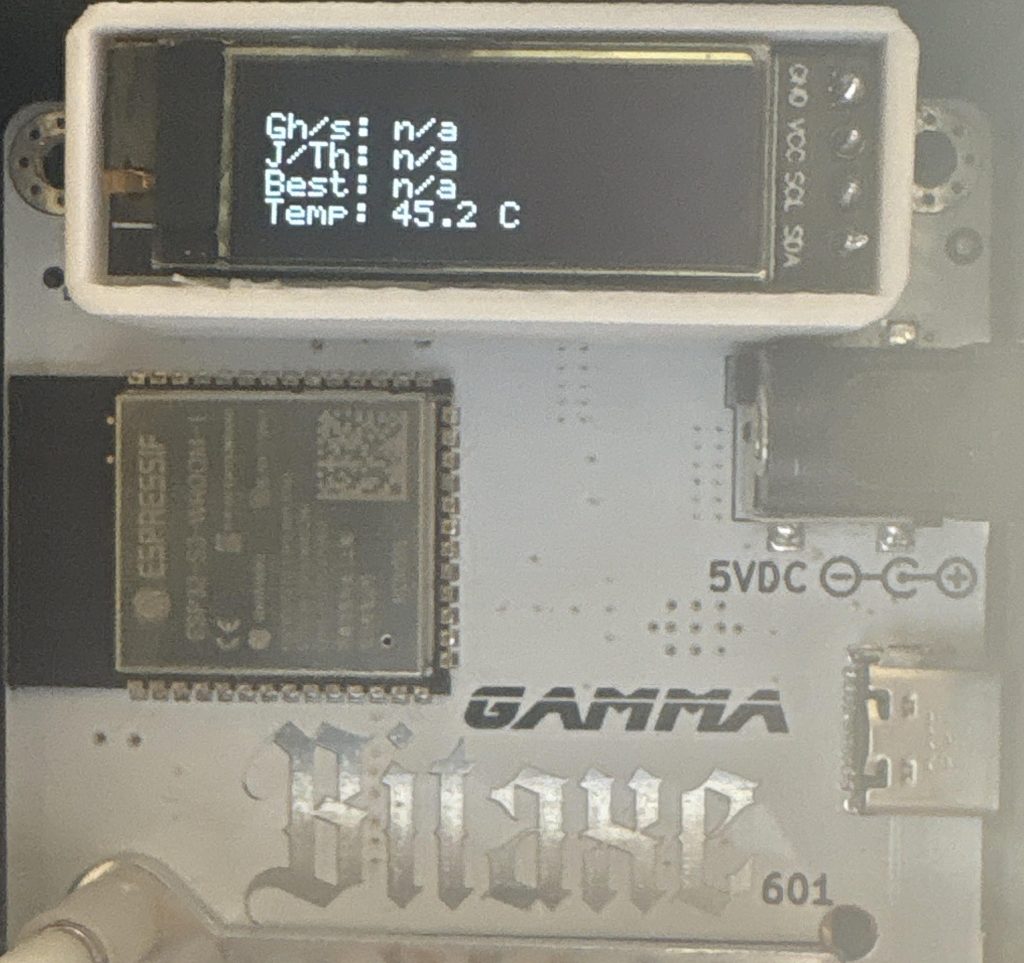
When your Bitaxe Gamma 601 periodically overheats, you’ll notice an indicator in your firmware UI and a “device overheat” message displayed on the miner’s LED screen. Don’t worry; Resolving it is straightforward. First, open your firmware “settings.” Make sure to reset the frequency and core voltage to the default values recommended for your ASIC chip.…
-

The apropos command searches manual page names and descriptions for a given keyword, helping users quickly discover relevant commands for a task. The apropos command helps Linux users find commands related to a keyword quickly. For example, typing apropos copy lists commands involving copying files or directories. Similarly, apropos network shows commands associated with network…
-
File System Hierarchy Standard (FHS): The File System Hierarchy Standard defines a consistent directory structure for Linux systems, specifying locations for system files, user files, and application data. FHS ensures predictability and uniformity across distributions, facilitating easier management and maintenance. Standard directories include /etc for configuration files, /var for variable data, /bin for essential binaries,…
-
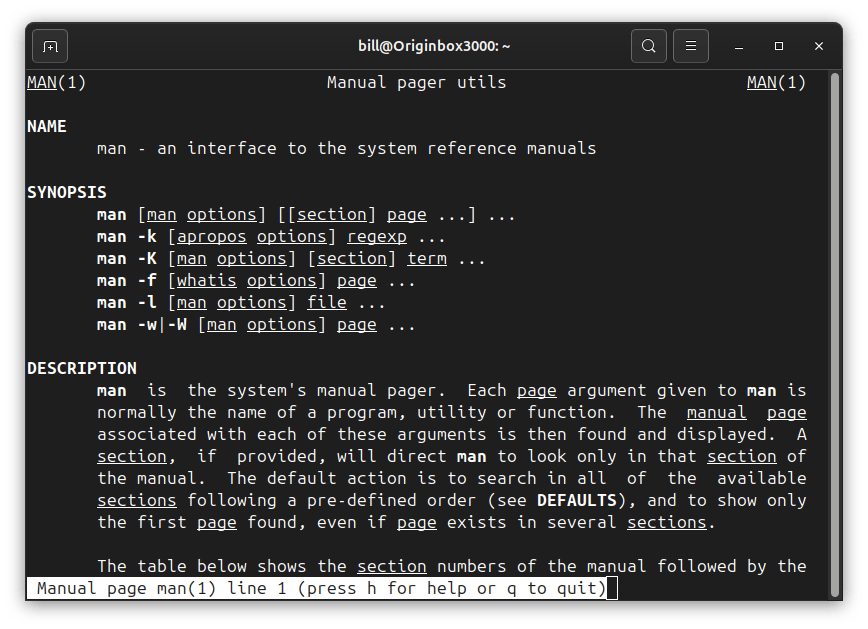
The man command, short for ‘manual’, is an essential tool in Linux, offering detailed documentation on virtually every command and program. By typing man followed by a specific command name, users gain immediate access to comprehensive manuals covering syntax, usage options, and practical examples. Ideal for beginners and seasoned professionals alike, the man command fosters…
-

Struggling to get your resume noticed on LinkedIn? Searching for a job can be overwhelming and at times feels like a job itself. During this time of applying to hundreds of jobs, I’ve found that filtering certain job preferences can dramatically increase your resume visibility. Try this 3-step strategy to boost your visibility instantly: 2.…
-

Definition and FunctionalitySerial communication refers to the process of transmitting data one bit at a time over a communication channel or computer bus. Unlike parallel communication, which sends multiple bits simultaneously, serial communication reduces signal interference and supports long-distance data transfer with fewer wires. It is widely used in telecommunications, industrial automation, and computer networking…
-

The Power-On Self-Test (POST) is a fundamental diagnostic process performed by computers immediately after they are powered on. This procedure verifies the functionality and integrity of essential hardware components before the operating system loads, ensuring that the system operates correctly. During POST, the system’s firmware—commonly the BIOS or UEFI—conducts a series of checks on…
-

Overclocking involves increasing a computer component’s clock rate beyond the manufacturer’s specifications to boost performance. This practice is commonly applied to processors and graphics cards, allowing them to execute more operations per second. While overclocking can lead to significant performance gains, it also raises power consumption and heat output, necessitating improved cooling solutions to maintain…
-
Network ports serve as essential communication endpoints, allowing devices to exchange data over the internet and private networks. These numerical identifiers, assigned to specific services and applications, ensure proper data routing between devices. The IT industry relies on well-defined port numbers to facilitate secure and efficient networking operations across various protocols and services. Commonly Used…
-
Client-side virtualization enables users to run multiple operating systems simultaneously on a single physical machine, enhancing flexibility and resource utilization. This technology allows each virtual machine (VM) to operate independently, with its own CPU, memory, and storage resources. A key component in client-side virtualization is the hypervisor, also known as the Virtual Machine Manager (VMM).…
-

The central processing unit (CPU) serves as the brain of a computer, executing instructions and processing data essential for system operations. A CPU’s architecture encompasses various components and functionalities that determine its performance and capabilities. Instruction Set Architecture (ISA) The ISA defines the set of instructions a CPU can execute, including operations like arithmetic, data…
-

Laser printers have become essential in both office and home environments, offering high-speed and high-quality printing solutions. Understanding their components and features is crucial for effective operation and troubleshooting. Key Components of a Laser Printer The Process of Paper Movement in a Laser Printer The movement of paper through a laser printer follows a structured…
-

RAID (Redundant Array of Independent Disks) is a data storage technology that combines multiple physical drives into a single logical unit to enhance performance, reliability, or both. Various RAID levels offer different balances between these factors. RAID 0 utilizes data striping, distributing data across multiple disks without redundancy. This configuration enhances read and write speeds…
-

Python’s package management landscape has been significantly shaped by pip, the default package installer for the language. Introduced in 2008 by developer Ian Bicking, pip—an acronym for “Pip Installs Packages”—was created to enhance the process of installing and managing Python software packages. It serves as a direct interface to the Python Package Index (PyPI), a…
-

M.2 is a compact, high-speed interface standard designed for internal expansion cards and solid-state drives (SSDs) in modern computers, including laptops, desktops, and embedded systems. It serves as a replacement for older standards like mSATA and mini PCIe, offering improved performance, efficiency, and space savings. M.2 devices utilize multiple bus interfaces, including PCI Express (PCIe)…
-

Accessing the web interface of the Cisco Catalyst 1200-8T switch is a straightforward process that allows IT professionals to configure and monitor network settings efficiently. The switch’s web-based graphical user interface (GUI) provides an intuitive platform for managing various network functions. Prerequisites: Accessing the Web Interface: Post-Login Configuration: For a visual walkthrough of the initial…
-
According to IEEE, the Transmission Control Protocol (TCP) has remained a cornerstone of modern internet infrastructure for over five decades. One of its fundamental processes, the FIN handshake, ensures a controlled termination of a network session, preventing data corruption or sudden disconnections. Unlike an abrupt RST (Reset) termination, the FIN handshake involves a four-step process…
-
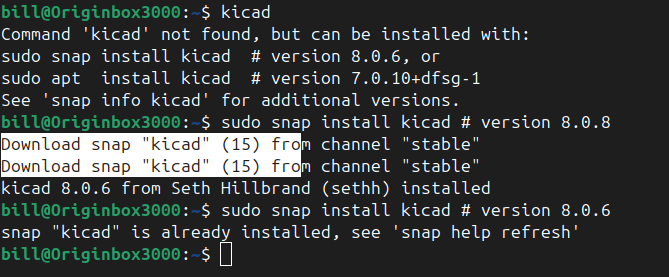
KiCad is a powerful open-source software suite used for designing printed circuit boards (PCBs). It offers a comprehensive set of tools for schematic capture, PCB layout, and 3D visualization, making it a go-to choice for both hobbyists and professional engineers. The software supports industry-standard formats and integrates essential features such as Gerber file export and…
-
-
UPDATE: the file names in this documentation have been changed. The server-side application is now referred to as VirtualServer.py, while the client-side script is called ProofOfScript.py. These names have been chosen to help readers easily follow along with the instructions. When running the API, please ensure you use the file names as indicated. In order…
-
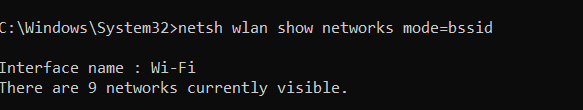
The command netsh wlan show networks mode=bssid is a Windows command-line instruction used to display detailed information about wireless networks available within range of the computer’s Wi-Fi router or adapter. The netsh utility, short for Network Shell, allows users to configure and monitor network settings from the command prompt. In this case, the command queries…
-
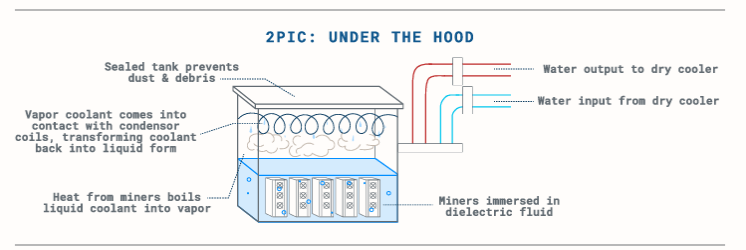
Marathon Digital Holdings has introduced the MARA 2PIC system, a two-phase immersion cooling solution designed to enhance data center efficiency and performance. The system submerges mining hardware in a dielectric fluid with a higher boiling point, which absorbs heat and vaporizes. The vapor then rises and condenses upon contacting chilled condenser coils cooled by a…
-

Troubleshooting a bricked NerdAxe device can be challenging, especially when a firmware update is interrupted, potentially leading to hardware issues. The NerdAxe, an open-source Bitcoin ASIC miner, utilizes the ESP32-S3 chip as its controller. Firmware updates for the NerdAxe are typically performed remotely via online platforms like Bitronics’ DIY Flasher. Interruptions during this process can…
-

An Uninterruptible Power Supply (UPS) is a device that provides emergency backup power to a computer or network system during a power outage or voltage fluctuation. It acts as a buffer between the computer and the power source, ensuring that critical systems remain operational long enough to safely shut down or switch to an alternative…
-
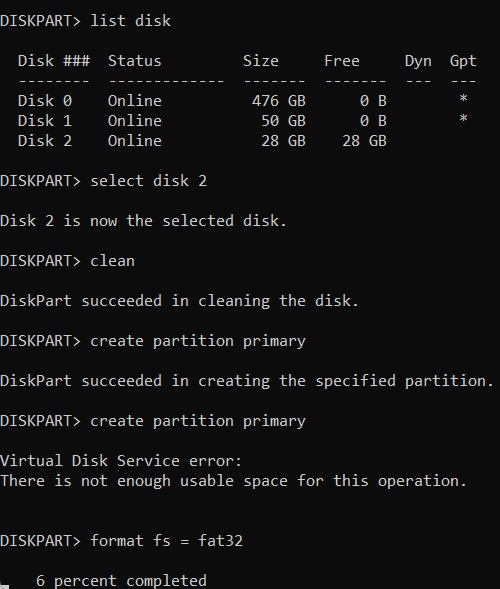
DiskPart is a command-line disk partitioning tool built into the Windows operating system. It allows users to manage their storage devices such as hard drives, SSDs, USB flash drives, and SD cards. DiskPart provides more control and flexibility over disk management compared to the GUI Disk Management utility in Windows. BitcoinVersus.Tech Editor’s Note: We volunteer…
-
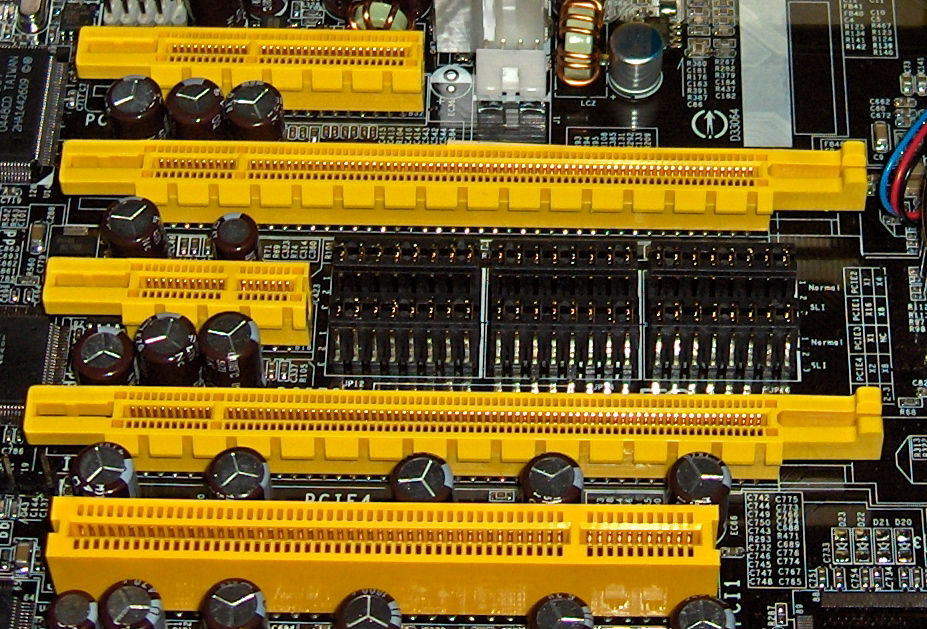
The Peripheral Component Interconnect Express (PCIe) is a high-speed expansion bus interface used to connect various hardware components to a computer’s motherboard. It serves as the primary interface for graphics cards, network adapters, storage devices, and other peripherals that require fast data transfer. PCIe uses a serial communication architecture, meaning it transmits data one bit…
-

The Bitaxe Machine offers open-source Bitcoin mining with customizable hardware and software. The Ultra model incorporates the efficient BM1366 chip, enhancing its power and accessibility. However, it’s important to note that Bitaxe Machines are not compatible with 5G frequency. Each model and version caters to specific needs and technical expertise in the competitive Bitcoin mining…
-

The snmpwalk command is used to perform a series of network management requests to a specific device using an IP address(example: 10.31.10.101),starting from the OID 1.3.6.1.2.1.2.2.1, using SNMPv3. Reference record for OID: Website to interpret OID Adresses snmpwalk -v3 -l authPriv -u l1monitor -a MD5 -A GEe9bb8h -x DES -X 4ixay7su 10.36.10.108 1.3.6.1.2.1.2.2.1snmpwalk: This is…
-
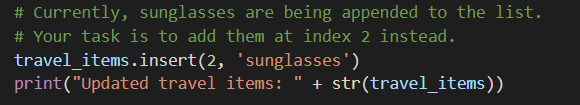
The code snippet provided shows how to insert an item into a list at a specific position rather than appending it at the end. Instead of adding “sunglasses” to the end of the list using append(), the task is to insert “sunglasses” at index 2 of the list travel_items. Explanation of the code:travel_items.insert(2, ‘sunglasses’) This…
-

The tasklist command is a Windows utility that lists all currently running processes on the system, along with key details like Process IDs (PIDs), memory usage, and executable names. It is commonly used for monitoring and troubleshooting processes. For instance, it can be combined with filters to locate specific tasks, such as running tasklist |…
-
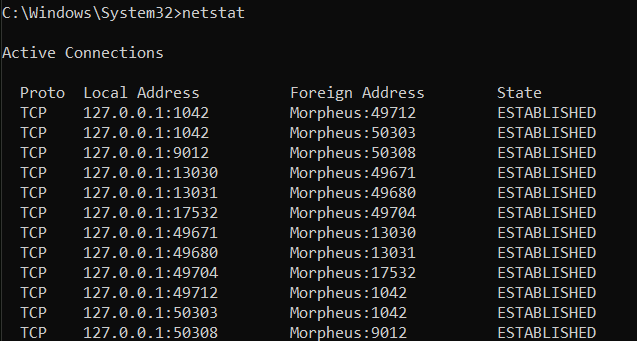
The netstat command provides statistics on current network connections and listening ports, offering insight into which applications are communicating over the network. Running netstat -a displays all active connections and ports. Netstat -b reveals the applications associated with each connection, valuable for security assessments (you need admin privileges for the “netstat -b” command). This command is used to detect suspicious…
-
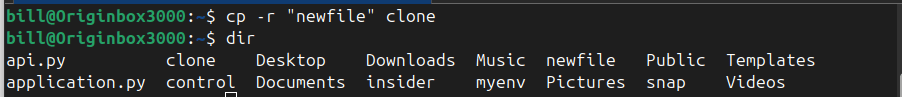
The cp command in Linux is used to copy files and directories. It’s a powerful utility that can create copies of data from one location to another, either within the same directory or across different directories. Adding the -r (recursive) flag allows you to copy entire directories, including their contents. This command copies the newfile…
-
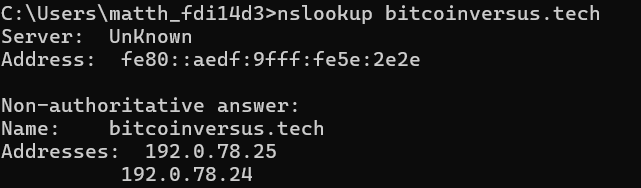
Nslookup (Name Server Lookup) is a command-line tool for querying Domain Name System (DNS) servers. It allows users to obtain the IP address associated with a domain name, or vice versa, helping in diagnosing DNS-related issues. For instance, nslookup google.com will show the IP addresses linked to bitcoinversus.tech This command is useful for troubleshooting DNS…
-
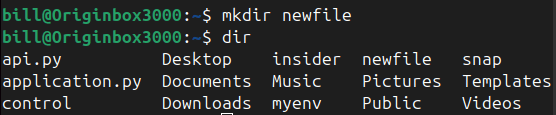
The mkdir command, an abbreviation for “make directory,” is a foundational tool for Linux users, enabling the creation of directories directly within the terminal. According to Linux documentation, the command is widely used to organize files systematically, promoting efficient file management practices for both personal and professional projects. Users simply type mkdir <directory_name> to create…
-
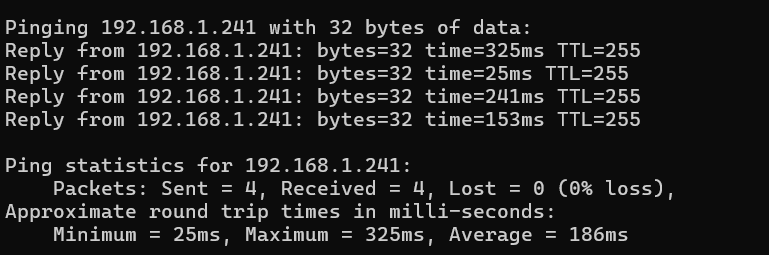
BitcoinVersus.Tech Editor’s Note: We volunteer daily to ensure the credibility of the information on this platform is Verifiably True.If you would like to support to help further secure the integrity of our research initiatives, please donate here The ping command is a fundamental network utility used to test the reachability of a host on an…
-
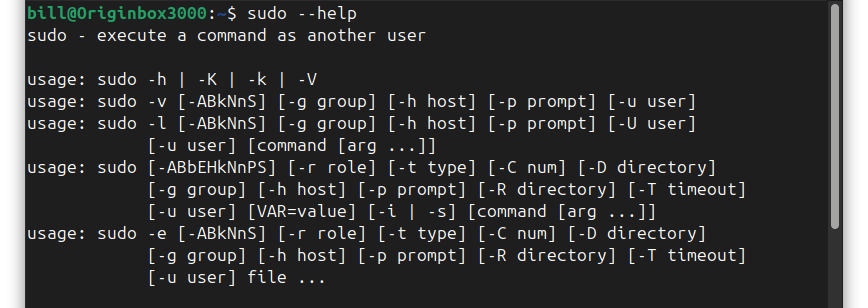
The sudo command in Linux enables authorized users to execute commands with superuser privileges, facilitating essential administrative tasks such as software installation, system configuration modifications, and service management. Key benefits of using sudo include enhanced security by requiring explicit permission before executing potentially harmful commands, accountability through logging each use for traceability, and controlled access…
-

The ‘tracert’ command, short for ‘Trace Route,’ is a network diagnostic tool that tracks the path data packets take from your device to a specified IP address or domain. By listing each hop and measuring the time it takes to travel between them, ‘tracert’ helps identify delays or connection issues along the route. For instance,…
-

In the realm of telecommunications, multi-band devices, such as dual-band, tri-band, quad-band, and penta-band, are engineered to operate across multiple radio frequency bands. This capability enhances connectivity and performance by allowing devices to communicate over various frequencies. Dual-Band Routers: An Overview Dual-band routers function on two distinct frequency bands: 2.4 GHz and 5 GHz. The…
-

The ipconfig command in Windows OS provides essential network configuration details, helping users view IP addresses, subnet masks, and default gateways, vital for resolving connectivity issues. Running ipconfig /all offers extended data such as DNS servers, DHCP settings, and MAC addresses. This command is commonly used in troubleshooting scenarios where network connectivity is interrupted or…
-

Embarking on the journey to create my own Bitcoin mining data center has been an exciting endeavor, involving precise planning, careful equipment selection, and a focus on efficiency. Here’s a breakdown of the components I’m using and why each one is essential for achieving a streamlined mining operation. The cornerstone of my setup is the…
-
The reason I had to change the color of the cursor was simply because I kept having a recurring issue with the cursor “disappearing” on different platforms. Changing your mouse color on Windows can improve cursor visibility, making it easier to locate on a complex screen and reducing eye strain. It also adds a personal…
-

Printers are an essential part of many computing environments, and understanding how they work, as well as their maintenance and troubleshooting, is vital for the CompTIA A+ certification. There are several types of printers commonly found in workplaces and homes, each with unique characteristics. Laser printers, for instance, use a process involving a laser beam…
-

To remotely monitor and control individual sockets on a Power Distribution Unit (PDU) using Modbus communication, Modbus-TCP can be employed to access and modify specific registers over a network. Each socket (or outlet) on the PDU is associated with unique register addresses that allow users to read the status (on/off) or control the power state.…
-

Pedro Domingos, a professor emeritus at the University of Washington and author of The Master Algorithm and 2040, envisions a future where humans may achieve unprecedented lifespans, potentially living up to 500 years. He suggests that such longevity could redefine human development stages, with people remaining in childhood until around 50. In recent public statements,…
-

American Wire Gauge (AWG) is a logarithmic stepped standardized wire gauge system used since 1857, predominantly in North America, for the diameters of round, solid, nonferrous, electrically conducting wire. Dimensions of the wires are given in ASTM standard B 258. The cross-sectional area of each gauge is an important factor for determining its current-carrying capacity.…
-

Tesla made headlines today with a massive movement of Bitcoin, reportedly shifting a total of $760 million, according to ArkhamIntel. The transfers occurred in increments of $225 million, $275 million, and $260 million, marking a significant financial maneuver by the company. This move has sparked speculation about Tesla’s broader strategy in the cryptocurrency space, as…